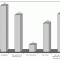
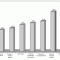
85% of Companies Satisfied with Outsourcing
The Latest Wrinkle in IT Certification
The Latest Wrinkle in IT Certification
Planning Your People Investment
Business Processes and CMM
The Capability Maturity Model (CMM) was developed at Carnegie Mellon University's Software Engineering Institute (SEI) in the mid-1990s. The book The Capability Maturing Model: Guidelines for Improving the Software Process , was published in 1995. (It had four editors and nine other contributors.
The OMG's Model Driven Architecture
Risk Matters: Techniques and Tools
Risks are a part of life, and therefore business. For organizations that practice sound risk management, and use risk techniques and tools, risks can be identified, avoided, minimized, and accepted to give companies a competitive advantage.
Risk Matters: Techniques and Tools
Risks are a part of life, and therefore business. For organizations that practice sound risk management, and use risk techniques and tools, risks can be identified, avoided, minimized, and accepted to give companies a competitive advantage.
Risk Matters: Techniques and Tools
Risks are a part of life, and therefore business. For organizations that practice sound risk management, and use risk techniques and tools, risks can be identified, avoided, minimized, and accepted to give companies a competitive advantage.
Risk Matters: Techniques and Tools
Risks are a part of life, and therefore business. For organizations that practice sound risk management, and use risk techniques and tools, risks can be identified, avoided, minimized, and accepted to give companies a competitive advantage.
The Demise of Computer Conferences
The Demise of Computer Conferences
Issues of Trust
Agile Software Development Ecosystems
Agile software development is a hot topic. As a generalization, it emphasizes team-oriented software develop practices that incorporate activities and steps that lead to successful software development.
Cybersecurity -- Has Anything Changed Since 9/11?
In an IEEE Software column earlier this year (Greg Goth, "Federal Government Calls for More Secure Software Design," IEEE Software, Vol. 19, No. 1, January/February 2002, pp. 90-92), we read the following quote from John Gilligan, CIO, US Air Force: "It is clear that the quality of software design and testing in the past does not measure up to the needs of the present and future." Along with this quote is a discussion of how terrorist attacks have galvanized agencies. All of this sounds impressive, but will there be any changes of consequence?
Security Then and Now
September 11 changed many things. Our personal lives have changed as much -- if not more -- than our professional lives. Some years ago, I had to beg for more money to enhance a security infrastructure. Why should we spend so much money on a "low-probability event" I was asked. Do we really need such a large off-site contingency facility? How will we pay for all this stuff? Today, it would be easy.
Security Technologies: What to Watch, What to Buy
Many of us are finally very concerned about security. We've already documented this increased awareness and commitment to just about all aspects of security (see the previous article). But what technologies are we looking at? Which ones should we buy? Which ones are likely to become "standard"? What should your technology hit list look like?