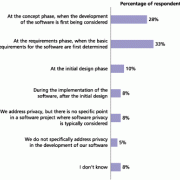
Part I of this three-part Executive Update series provided a short overview of how information security and privacy controls are -- or more often are not -- built into software, and also reviewed the responses to the first set of questions of a Cutter survey on developing privacy-sensitive software.
Executive Update
Building Privacy Controls into Software, Part II
Posted October 9, 2014 | Technology |
Don’t have a login?
Make one! It’s free and gives you access to all Cutter research.


