Business continuity management (BCM) is no longer a luxury but an essential element of an organization's risk management program. For an organization to have any hope of survival, the BCM process must embrace risk, emergency, and recovery planning in order to manage a "crisis" or "disaster" event. Undertaking any business continuity activity should form part of a wider planning structure; it is not an end in itself but rather a means to an end.
For many organizations, the decision to invest in BCM is being forced upon them by legislation/regulatory obligations (e.g., since 1989, federally chartered institutions in the US have been required to have a disaster recovery plan). In addition, third parties (e.g., shareholders) have made directors/executive managers of corporations personally susceptible to legal action for failing to carry out their fiduciary duties to prevent and/or mitigate the impact of a disaster or near disaster on the organization. Certainly, the events of September 11 as well as the destruction of the US city of New Orleans caused by Hurricane Katrina in 2005 focused management's attention on BCM.
Organizations for many years have made a significant investment in their business continuity capability. This investment initially focused on the recovery of their information technology infrastructure, with little or no consideration given to the recovery of business processes. However, business continuity has evolved from disaster recovery planning and its focus on the recovery of information technology by repositioning itself and looking at business continuity holistically.
BCM covers the following areas:
-
Business continuity planning (BCP)
-
Disaster recovery planning (DRP)
-
Crisis management planning (CMP)
Below are definitions of these important terms taken from Disaster Recovery Institute International's "Business Continuity Glossary" [2]:
-
Business continuity plan — "the process of developing and documenting arrangements and procedures that enable an organization to respond to an event that lasts for an unacceptable period of time and return to performing its critical functions after an interruption."
-
Disaster recovery planning — "the technical component of business continuity planning." The advance planning and preparations that are necessary to minimize loss and ensure continuity of the critical business functions of an organization in the event of disaster.
-
Crisis management — "the overall coordination of an organization's response to a crisis, in an effective, timely manner, with the goal of avoiding or minimizing damage to the organization's profitability, reputation, and ability to operate."
-
Business continuity management — "a holistic management process that identifies potential impacts that threaten an organization and provides a framework for building resilience with the capability for an effective response that safeguards the interests of its key stakeholders, reputation, brand, and value-creating activities. The management of recovery or continuity in the event of a disaster. Also the management of the overall program through training, rehearsals, and reviews to ensure the plan stays current and up to date."
-
Crisis — "a critical event, which, if not handled in an appropriate manner, may dramatically impact an organization's profitability, reputation, or ability to operate. Or, an occurrence and/or perception that threatens the operations, staff, shareholder value, stakeholders, brand, reputation, trust, and/or strategic/business goals of an organization."
This Executive Report focuses on business continuity rather than the technical side of the recovery (disaster recovery).
Organizations develop a strategic risk management plan to assist in identifying, quantifying, and managing its risk, and business continuity is an integral part. Figure 1 provides an overview of the organization's strategic risk management plan. From the figure, it can be seen that business continuity is one of the strategies the organization employs to mitigate its risks.
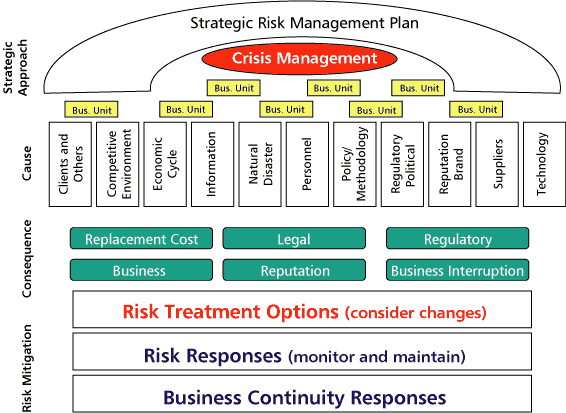
Figure 1 — Strategic risk management plan.
Successful implementation of the strategic risk management plan (and business continuity) requires executive management support. This support comes from the development of an organizational culture for managing risk through the implementation of policies and continuous commitment from management (i.e., resourcing and investment in business continuity).
This Executive Report begins by looking at the business continuity culture before offering an overview of business continuity management. The report then follows the business continuity development process and walks through the following areas: project initiation; risk evaluation; business impact analysis; BCM strategies; emergency response and operations; developing and implementing a BCP; awareness and training programs; exercising and maintaining the BCP; crisis communications; and coordinating with external agencies.
DEVELOPING A BUSINESS CONTINUITY CULTURE
Developing a business continuity culture in any organization is a significant undertaking, particularly if the organization has traditionally seen business continuity as an information technology risk and not as an organization-wide issue. Information technology is only one of many dependencies the organization has in the delivery of its products and services.
Many organizations fail to develop a business continuity culture because there is a perception that it is a costly, time-consuming process that requires a large amount of resources that would otherwise be directed toward the generation of revenue. Management must be assured that by investing in business continuity, it is ensuring its survival in the event of a disaster and that it makes good business sense.
Management needs to be continually reminded that the aim of business continuity is to keep the organization in business in the event of a disaster by maintaining its critical core processes in the delivery of products and services to its internal and external customers. It is important that once it has been recognized that business continuity is a critical component of the organization's risk management program the organizational processes embrace this concept and continue to support it.
The key to developing a business continuity culture is ongoing commitment from executive management. This is supported by:
-
A BCM policy that encompasses:
-
Business continuity
-
Crisis management
-
Crisis response
-
Crisis communication
-
Disaster recovery
-
-
Resourcing
-
Business continuity investment
-
A BCM education program
We examine each of these areas in this section.
Business Continuity Policy
Organizational policy is the highest level of control for any organization. The policy provides a control framework for the implementation of strategic objectives of the organization. However, too often organizations do not have a business continuity policy, which broadly states the organization's objectives for its survival. The policy should, at a minimum, include the following:
-
Policy statement — defining the organization's directive for business continuity
-
Purpose — defining why the BCP policy exists
-
Scope — defining to what and to whom the policy applies
-
Authority — defining under who/what the policy is issued
-
Responsibilities — defining who is accountable
For example, a simple policy statement may be phrased as: "Safeguards shall exist to minimize the risk, cost, and duration of disruption to business processes in the event of damage to, failure of, loss of, corruption of, or discontinuation of a strategic component of the critical infrastructure that supports the organization."
Resourcing
There are three ways of funding business continuity for an organization: corporate, business unit, and information technology.
Corporate Funding
For many organizations, the funding decision is very simple; as business continuity is viewed as an organizational responsibility and is part of the cost of being in business, funding is provided at a corporate level. The benefit of this strategy is that business continuity will have a strong and continuous commitment from executive management. Further, it can be seen as proof that the executive management of the organization has carried out its fiduciary duties and in the event of a disaster would be protected from any legal action.
Business Unit Funding
Many organizations view business continuity funding as a business unit expense, and therefore each business unit must fund the cost of its business continuity planning. The disadvantage of this strategy is that the business unit managers, who are often under pressure to control costs, will target business continuity as a..candidate for cost-cutting, as it is seen as an easy target.
Although cost-effective (i.e., saving funds) in the short term, this decision may also expose the organization's management to criticism from third parties (e.g., shareholders, external auditor) and, in the event of a disaster, may expose executive management to legal action for failing to carry out its fiduciary duties.
Information Technology Funding
There are a number of organizations that view business continuity as an information technology issue rather than as a corporate or business unit issue. Therefore, funding is provided through the IT department budget. The advantage with this approach is that IT departments historically have a good understanding of the need to have a business continuity plan. The disadvantage of this approach is that it focuses only on the IT dependency of the organization and not on other critical business processes and dependencies that are outside of IT.
Business Continuity Investment
Determining how much the organization should invest in business continuity is difficult. However, one of the outcomes of the business impact analysis (discussed later in this report) is that it provides the organization with an indication of the financial impact if a disaster were to strike. Therefore, the organization needs to determine how much it is prepared to spend to minimize this financial impact and potential damage to its brand.
Management often asks, "How much should we spend on business continuity?" To answer this question, we need to consider many variables in determining the appropriate level of expenditure; for example:
-
Industry
-
Size of organization
-
Total revenue
-
Value of the organization's brand
-
Complexity of the organizational structure
-
Location
-
Range and distribution of products and services
-
Level of risks
-
Controls (plus cost) currently deployed to mitigate the impact of the disaster event
It appears that there has been very little research undertaken on quantifying how much organizations are spending on business continuity management. However, indications are that what research has been done has focused on disaster recovery with no consideration given to the other components of BCM; specifically, the crisis management plan, crisis communication plan, business continuity plan, and emergency response plan.
The research on disaster recovery spending indicates that approximately 2% of the organization's IT expenditure is spent on disaster recovery.
The Disaster Recovery Journal regularly conducts "straw" polls (a poll or vote with nonbinding results or an informal opinion survey) on business continuity/disaster recovery; while subjective, they do have some value as an indicator of trends. In the past few years, answers to questions about expenditure indicate that there has been no major increase in expenditure on business continuity.
This result is rather surprising when you consider that in the last few years organizations have dramatically changed the way they conduct business, in particular, the increase in e-commerce and global organization.
Education Program
Commitment by management extends to the implementation of a business continuity awareness program that is supported by adequate funding and resourcing. There are various levels of business continuity education in an organization, as we detail later in this report.
OVERVIEW OF BUSINESS CONTINUITY MANAGEMENT
It is important to use a recognized BCP methodology to make sure a structured approach is adopted and consistently applied throughout the development and implementation of a BCP. There are two internationally recognized professional associations dedicated to business continuity that have BCP standards. These standards have been developed from best practices. The organizations are:
1. DRI International (US)
2. Business Continuity Institute (BCI — UK)
While the methodologies differ slightly, the process and content of the two are almost identical. Both organizations have a certification program that supports the business continuity profession. Further, both have a strong training program to assist personnel to gain not only professional certification, but also training in developing, implementing, and testing BCPs.
Business Continuity Standards
A number of government and nongovernment associations have developed guidelines for business continuity, as outlined below:
-
National Institute of Standards and Technology (NIST — www.nist.gov) — an agency of the US Department of Commerce, in June 2002, NIST issued a document titled "Contingency Planning Guide for Information Technology Systems" (NIST SP 800-34). This document addresses specific contingency planning recommendations for seven IT platform types and provides strategies and techniques common to all systems. The platform types are:
-
Mainframe
-
Server
-
Desktop and portable systems
-
Web sites
-
WANs
-
LANs
-
Distributed systems
-
-
Standards Australia (www.standards.org.au) — its publication "Business Continuity Management" (HB 221:2004) outlines an approach to develop and implement business continuity within an organization. A companion to this publication is the world's first generic risk management standard (AS/NZS 4360:2004). This standard may assist in quantifying the likelihood and consequences of the impact upon the organization of a "disaster" type of event (e.g., fire destroying the organization's IT capability). This standard may soon be replaced by ISO/CD 31000 on risk management guidelines, which is nearing finalization for release.
-
ISO (www.iso.org) — section 11 of "ISO/IEC 17799 Information Technology — Security Techniques — Code of Practice for Information Security Management" specifically addresses business continuity (business continuity is also referred to in other sections).
-
National Fire Protection Association (NFPA — www.nfpa.org) — the aim of "NFPA 1600: Standard on Disaster/Emergency Management and Business Continuity Programs" is to establish a common set of criteria for disaster/emergency management and business continuity programs.
-
British Standards Institute (BSI Group — www.bsi-global.com) — BSI released part one of its business continuity standard in 2006 and part two — "BS 25999-2: Specification for Business Continuity Management" — in late 2007. BS 25999-2 specifies requirements for establishing, implementing, operating, monitoring, reviewing, exercising, maintaining, and improving a documented BCM system within the context of managing an organization's overall business risks. The requirements specified in BS 25999-2 are generic and intended to be applicable to all organizations, regardless of type, size, or nature of the business. The extent of the application of these requirements depends on the organization's operating environment and complexity.
THE BCP DEVELOPMENT PROCESS
DRI International's "Professional Practices for Business Continuity Planners" [3] outlines 10 steps in developing business continuity, as seen in Figure 2 and listed below:
-
Project initiation
-
Risk evaluation and control
-
Business impact analysis
-
Developing BCM strategies
-
Emergency response and operations
-
Developing and implementing a BCP
-
Awareness and training programs
-
Testing, exercising, (and maintaining) the BCP
-
Crisis communications
-
Coordinating with external agencies
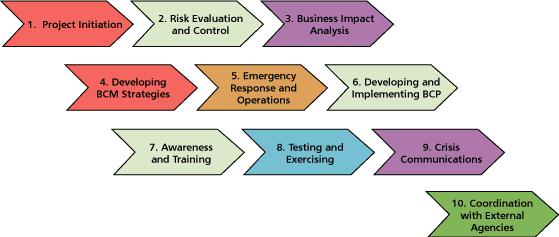
Figure 2 — Steps to develop business continuity.
The remainder of this report focuses on each of these 10 steps.
Project Initiation (Objectives and Assumptions)
The objective of this section is to establish a sound framework for the development of the business continuity plan to ensure that the project will achieve its strategic goal.
From the outset, a strong commitment from the organization's management to the business continuity project lifecycle is required. Too often there is commitment at the beginning of the project, but as other issues and/or projects occur, management's commitment diminishes, resulting in the project losing focus, authority, and more importantly funding, which sets it up for failure.
In this section, we highlight some of the key factors to consider during project initiation.
Objectives, Policies, and Critical Success Factors
From the outset, the project must have clearly defined objectives and policies that guide it through its lifecycle with criteria to measure its success or failure.
Project Governance
The main contributor to any type of governance failure is poor corporate culture. All the planning, policies, guidelines, procedures, and reporting structures may be in place, and all may conform to best practice requirements; however, if the culture is not right, people will always look for opportunities to circumvent correct procedures or do things that suit their own vested interests.
Culture is an important element in ensuring the success of governance. The tone at the top is essential for ensuring the culture is right. Senior executives cannot just make rules of governance and expect them to be followed. They must take an active role and champion the rules by communicating, setting the example by adhering to the rules themselves, monitoring compliance, and resolving instances of noncompliance. They have to not only "talk the talk," but more importantly "walk the talk."
To ensure strong project governance, a BCP project steering committee should be established from the outset. Members of this committee should include representatives from each of the major business units plus a member from the organization's IT department and internal audit. Further, the chairperson of the steering committee is to be the project sponsor. This conveys to the members of the steering committee that the organization's executive management supports a corporate governance culture as well as the development and implementation of an organization-wide BCP.
Project Sponsor
It is critical that the project has endorsement and support from the highest level within the organization. Ideally, the project sponsor should be the CEO or COO. However, at a minimum, the sponsor should be a member of the organization's executive team.
Business Continuity Project Steering Committee
A business continuity project steering committee is to be established from the outset with its role, responsibilities, and authority defined in the committee's charter. The charter contents are to be communicated to all key stakeholders to ensure that its mandate is clearly understood.
It is essential that the members of the project steering committee have a commitment to the business continuity project and have a clear understanding of their roles and responsibilities to ensure effective governance of the project.
Project Plan
The development of the project plan must include:
-
Scope
-
Objectives
-
Dependencies and assumptions
-
Deliverables
-
Project methodology including project reporting
-
Governance
-
Project milestones
-
Project role and responsibilities
-
Change management plan
-
Project risks and mitigations
-
Resource requirements
-
Financial budget
-
Quality plan
-
Project communication plan
-
Project success criteria
The project plan plus budget should be reviewed and approved by the project steering committee.
Risk Evaluation and Control
The objective of performing a risk evaluation and control analysis is to identify potential sources of threat including man-made, environmental, political, and technological hazards that may lead to a "disaster" type event.
Physical Risk Assessment
A physical risk assessment of each of the organization's sites should be performed to identify potential sources of threats and hazards and the current level of mitigation (i.e., controls) as well as to evaluate the effectiveness of the controls (see Figure 3).
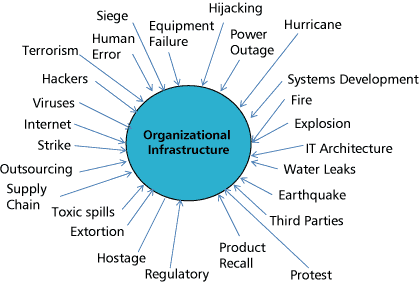
Figure 3 — Sources of threats and hazards.
In one organization, for example, local authorities assessed a region where the organization has a manufacturing plant as having a flood rating of 1:200 years. However, due to the construction of a major highway in the area, water flows had been altered. As a direct result, the flood rating was reassessed by local authorities and upgraded to 1:20 years.
Without having performed a risk assessment as part of developing the organization's business continuity plan, the potential risk from flooding may not have been detected.
To minimize the impact of possible flooding, the organization constructed a flood levee, planted with local flora, to a height of 1.5 meters (almost 5 feet) surrounding the manufacturing plant (with approval from the local authorities). Approximately 18 months later, a flood occurred. Without construction of the levee, the manufacturing plant would have been severely flooded with an estimated US $10 million-plus in physical damages and potential loss of major orders (approximately $30 million).
For each threat and/or hazard identified, an assessment of the likelihood (i.e., probability) and consequences is made, and from this the cost of mitigation is calculated. In other words, we are looking at the cost versus benefit of mitigating the potential threat and/or hazard.
Various risk methodologies can be used to perform the risk assessment and different techniques to gather the information. Each risk methodology has its advantages and disadvantages. However, whatever risk methodology is used, it must be consistently applied both qualitatively and quantitatively. Potential sources of threats and/or hazards can be identified by:
-
Physical inspection
-
Questionnaires
-
Interviews
-
Workshops and meetings
-
Documentation review
Each risk identified is to be classified according to predetermined criteria, including:
-
Risks with mitigation in place
-
Risks with no mitigation in place
-
Risks outside the organization's control
-
Exposures with prior warnings (such as tornadoes and hurricanes)
-
Exposures with no prior warnings (such as tsunamis and earthquakes)
For each risk category, determine the consequence (i.e., impact) on the delivery of services and products to the organization's customers.
Single-Point-of-Failure Analysis
The objective is to identify any single point of failure within the organization's infrastructure, in particular, information technology. Single points of failure have increased significantly due to the continued growth in the complexity of IT environments. This growth has occurred as a response to technology and customer demands for new channels in the delivery of services and/or products (e.g., e-commerce).
Organizations have failed to respond to this increase in exposure from single points of failure by not implementing risk mitigation strategies. Building redundancy into the design of the IT architecture is one strategy to minimize the impact of failure.
One common area of risk from single points of failure in the IT environment is telecommunications. It is because of its transparency that this potential risk is often overlooked. While the resiliency of the network and the mean average between failures of telecommunications devices (e.g., a router) have significantly improved, it is still a single point of failure, which may lead to a disaster being declared.
For example, one organization that had failed to build redundancy into its IT infrastructure architecture had all telecommunications (to more than 4,200 locations) passing through one large single switch. A component failure in the telecommunication's switch resulted in more than one-third of the locations being unable to process any transactions, with the loss of gross revenues of US $20 million for 24 hours before the resumption of services.
As organizations continually reengineer their processes by integrating with those of their suppliers, strategic business partners, and customers (e.g., e-commerce), the level of risk increases and the recovery-time window shortens. Organizations in their haste to deliver this infrastructure often give very little consideration to the elimination of single points of failure in their design.
To ensure that a single point of failure is identified within the organization's IT architecture at the earliest possible stage, it is essential that a technology risk assessment (TRA) be performed as part of any project.
The objectives of the TRA are to:
-
Identify the IT risks
-
Determine the level of risk
-
Identify the risk factors
-
Develop risk mitigation strategies
The benefits of performing a TRA are:
-
A business-driven process to identify, quantify, and manage risk while detailing future suggestions for improvement in technical delivery
-
A framework that governs technical choice and delivery processes with cyclic checkpoints during the project lifecycle
-
Interpretation and communication of potential risk impact and where appropriate, providing risk reduction to a perceived acceptable level
-
Implementation of strict disciplines for active risk management during the project lifecycle
The TRA needs to be a mandatory requirement for all projects to ensure that proactive management of risk occurs and that no single point of failure is inadvertently built into the overall architecture.
Internal Environment
Any proposed physical infrastructure changes must be communicated to ensure that potential risks to the existing business continuity plan(s) can be assessed. For example, proposed changes to the layout of a floor, such as cabling, workstation setup, and voice communications, due to restacking of the building to increase the floor occupancy density rate, may have an impact upon the strategy of an existing BCP.
The floor in question may have been designated as the area for another business unit to occupy during a disaster. The necessary infrastructure for the successful execution of the business continuity plan had been previously established. By implementing the restacking requirements, however, the business unit's business continuity strategy has been compromised.
The risk is that in the event of a disaster, the organization may not be able to gain access to its critical applications or access its voice communications, thereby either delaying recovery or failing to recover from the disaster.
Dependency on Third Parties
A risk assessment of the organization's dependency on third-party service providers should be undertaken. While the organization may have a strong business continuity environment with well-developed plans, this may not be the case for its strategic business partners. This is one risk that many organizations have not recognized.
A large number of organizations have a dependency upon third-party providers for the delivery of services and/or products. These third-party service providers are critical for the continual survival of the organization.
For manufacturing organizations, securing their supply chain is absolutely critical to ensure the continued supply of material for their production processes. Further, essential plants and equipment used in the production process often have long lead times for resupply.
During the past 10 years, many organizations have outsourced a number of processes that they have considered to be noncore; for example:
-
Marketing and distribution of promotional material
-
Production of credit cards
-
Information technology
-
Logistics
Where an organization has either outsourced or has a contractual relationship for the supply of services and/or products, you often find that there is no provision in the contract for the third-party service provider to have a BCP. The risk is that if a disaster event affects the third-party service provider, there is every likelihood that this strategic business partner will be unable to provide the service and/or product to the organization.
While the disaster may not directly affect the organization, collateral damage can occur through the failure to secure the organization's supply chain. The organization may face a potential disaster and a threat to its very survival. The organization's BCP strategies may not address this scenario.
If an organization has recognized this risk and contractually required its strategic business partner to have a BCP, there is no process to ensure that the third-party service provider has developed the BCP or has exercised it on a regular basis.
To minimize this risk, the organization must ensure that there is a contractual requirement for the third-party service provider to have an up-to-date BCP. Further, the contract should allow for the organization to either audit the BCP or for the third-party service provider's auditors to provide a certificate on an annual basis stating that the BCP has been tested within the last 12 months and that any deficiencies have been corrected.
Business Impact Analysis
This section is absolutely critical for the development of a BCP, as this is where the critical business processes, dependencies, and interdependencies are identified (e.g., IT, strategic business partners, key staff, vital records, and so on). Further, the analysis also identifies and quantifies the impact a disaster will have upon the organization.
A number of tasks are to be undertaken in this phase, including:
-
Identification of critical business processes
-
Identification and quantification of the threats/risks to critical business processes both in terms of outage and financial impact
-
Identification of dependencies and interdependencies of critical business processes and the order in which they must be restored
-
Determination of the maximum tolerable outage (e.g., four hours, 24 hours, three days, and so on, for each business process)
-
Consideration of the impact at the worst time of the processing cycle
-
Consideration of the type and quantity of resources required for the recovery (e.g., office furniture, faxes, photocopiers, safes, desktop computers, printers, telephone handsets, and so on)
-
Determination of the impact on the organization in the event of a disaster (e.g., financial, reputation, and so on)
To gather and collate the information for the above-mentioned tasks requires a number of techniques to be used in combination, including:
-
Workshops and meetings
-
Questionnaires and templates
-
Interviews
-
Documentation review
One issue encountered when gathering large amounts of data during the business impact analysis process is double counting, as the same information is collected from a variety of sources but in different formats, languages, and numbers. The issue is that the risk impact being reported is larger than the reality due to such double counting.
For example, a financial organization was undertaking a business impact analysis with data collated from a number of departments via questionnaires, workshops, and interviews; each had identified that if it did not report cash transactions greater than AUD $10,000 in the prescribed period of time (say, three days), the financial regulator would penalize the organization $50,000 for each transgression. Based on the numbers provided by five different departments, there were 500 transactions per day that were greater than $10,000.
If the organization suffered a disaster event and could not provide the details of those transactions, the penalties would amount to AUD $25 million. After validating the information received and cross-checking with the regulator, it was found that the correct number of transactions on average was 250 per day. Therefore, in the event of a disaster where the organization could not report to the regulator and assuming that the regulator would apply the maximum penalty, the penalties imposed would have amounted to $12.5 million per day.
Validation of outcomes from the business impact analysis process requires:
-
Documenting the business context, including:
-
A high-level organizational chart and a list of key business objectives and critical success factors
-
Key business processes noting key outputs and maximum tolerable outage, that is, how long the business unit can be without a critical business process (e.g., four hours, 24 hours, three days, and so on)
-
Key staff
-
-
Assessing the impact of a process failing, including:
-
Consideration of the impact in relation to the business and operations of the organization
-
Consideration of the impact of the process failing for a period of, for example, 24 hours, which is the maximum tolerable outage for the most critical process
-
An assumption that the incident causing failure occurs at the worst possible time for the organization
-
-
Identifying the resources and dependencies relied upon by the key processes:
-
Resources and dependencies assume the lowest maximum tolerable outage of the key processes that rely on them; this may require an organization-wide audit of assets, resources, and processes to be undertaken
-
Identification and quantification of the threats/risks to critical business processes both in terms of outage and financial impact should be undertaken. Table 1 provides assistance in this regard.
Table 1 — Degrees of Impact
| Impact | What Is Impacted? | Guidelines (Examples) |
| Insignificant | Consider all areas |
|
| Minor | Clients |
|
| Financial |
|
|
| Other parties |
|
|
| Moderate | Clients |
|
| Financial |
|
|
| Legal and regulatory |
|
|
| Reputation |
|
|
| Staff |
|
|
| Other parties |
|
|
| Major | Clients |
|
| Financial |
|
|
| Legal and regulatory |
|
|
| Reputation |
|
|
| Staff |
|
|
| Other parties |
|
|
| Catastrophic | Clients |
|
| Financial |
|
|
| Legal and regulatory |
|
|
| Reputation |
|
|
| Staff |
|
|
| Other parties |
|
The business impact analysis identifies critical business processes undertaken by the organization and identifies the resources and dependencies essential to their operation and performance. Risk mitigation ensures the likelihood of resources/dependencies affected by an "event" is managed at all stages.
Developing BCM Strategies
The objective of this section is to determine the available options and formulation of appropriate alternative operating strategies so as to provide timely recovery for all critical processes and their dependencies in the event of a disaster.
There are various strategies that can be adopted in developing the plan. The following are examples that need to be considered:
-
Doing nothing; in some circumstances, this is a viable strategy
-
Deferring action; await the outcome and make decisions after the impact is fully known
-
Manual workaround procedures
-
Reciprocal agreements with strategic business partners
-
Alternative site or business facility
-
Alternate sourcing of services and/or products
-
Third-party service providers/outsourcers
-
IT strategies, for example:
-
Hot site — fully operational computer center, including data and voice communications
-
Alternate LAN server — a LAN server fully configured and ready to be shipped and installed at the same site or alternate site
-
Physical separation of telecommunications devices — previously centralized to reduce the likelihood of a single point of failure
-
Establishment of service-level agreements (SLAs) with BCP recovery company (i.e., hot, warm, or cold sites and mobile)
-
Duplication of telecommunications network — another telecommunications carrier, switching capability, and so on
-
-
Insurance
If a business is to survive a disaster, it must select the right recovery strategies. If the wrong BCP strategy is selected, then the BCP plan will be developed upon an incorrect premise, which in the event of a disaster may actually exacerbate the situation [1].
The recovery strategies may be two-tiered:
-
Business — logistics, accounting, human resources
-
Technical — information technology (e.g., desktop, client-server, midrange computers, mainframe computers, data and voice networks)
The organization's recovery strategy needs to be developed for the recovery of the core business processes. In the event of a disaster, it is survival and not business as usual.
One of the critical determinants used in selecting the business continuity strategy is the maximum tolerable outage. However, for the IT side of the recovery — that is, disaster recovery — the recovery-time objective needs to be determined.
The recovery-time objective is the time that is taken to restore the IT infrastructure once the disaster is "declared." The recovery-time objective is different from the maximum tolerable outage, which is based on how long the business can survive without its critical processes before business survival is in jeopardy.
The overall objective is to identify the BCP recovery strategies that are low risk and cost-effective. Too often, there is a greater emphasis on cost rather than on the risks associated with the recovery strategy. A risk methodology needs to be used to undertake this analysis.
In general, the shorter recovery time required, the higher the costs; conversely, the longer the outage, the greater the impact. Figure 4 illustrates this point.
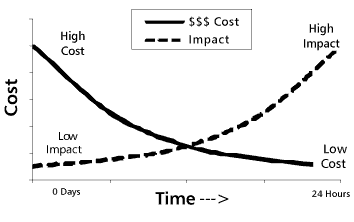
Figure 4 — Cost of recovery versus cost of impact.
In any recovery strategy that depends on third parties, there must be a business continuity SLA specifying the contractual obligations for the delivery of services and/or products when a disaster is declared.
Emergency Response and Operations
The objective of this section is to develop and implement procedures for response and stabilizing the situation following an incident or event, including establishing and managing a crisis command center that is to be used for the duration of the emergency.
A number of tasks are undertaken in this phase, including:
-
Selecting the most appropriate tools for the creation and maintenance of the emergency response plan(s) (e.g., word processing, BCP software, spreadsheets, and so on)
-
Developing procedures for emergency response, a crisis management plan, and a crisis communication plan
-
Defining the recovery tasks (including sequence and timing) and assigning responsibilities (including accountability) for each plan
-
Defining the escalation processes
-
Identifying dependencies and interdependencies or individuals required to perform required tasks
-
Differentiating between crisis response, crisis management, and crisis communication teams
-
Establishing a crisis command center
-
Identifying and listing key contacts, suppliers, and resources
-
Structuring and documenting the plans to facilitate ease of use and future maintenance (including version control)
Figure 5 indicates the relationships between crisis response, crisis management, business continuity, and disaster recovery.
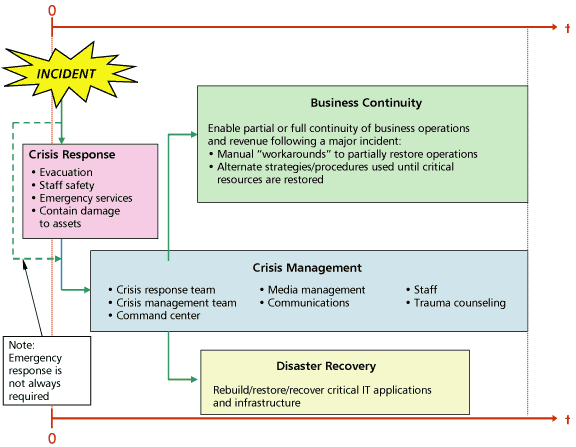
Figure 5 — The relationships between crisis response, crisis management, business continuity, and disaster recovery.
Crisis Management Plan
Crisis management planning involves the development of a plan and structure that enable an organization to effectively and cohesively deal with all aspects of a crisis. This is particularly critical in the first 24 hours.
This plan includes details of the crisis response team, crisis management team, support staff, the crisis command center, and a schedule of roles and responsibilities. The main steps of the crisis management cycle from the initial incident through to closure of the crisis are explained. There is an emergency contact list, checklists, guidelines, and suggestions for communication with both internal (e.g., staff, managers, directors) and external stakeholders (e.g., media, customers, suppliers, and regulator).
While every crisis is different, all share, to some extent, the following characteristics:
-
Insufficient information when you need it most
-
Escalating flow of events
-
Events outpace response by organization (real or perceived)
-
Loss of control (real or perceived)
-
Surprise
-
Panic/confusion
-
Intense scrutiny from the outside
-
Development of a siege mentality
-
Disruption of regular decision-making process
-
Important interests at stake
-
Affected managers focus on short-term planning/decisions/actions
-
Ambiguity
The aim is to prepare the organization's executive management that has been identified as having a key role to be equipped to deal with these challenges.
The main requirements for effective crisis management are strong communication, effective decision making, teamwork, and preparation. Due to the fact that there are so many permutations of loss scenarios or situations that could give rise to a crisis, and it is impossible to plan for each one, crisis management plans are not prescriptive. Rather, the aim is to enable decision makers to communicate with each other by concentrating on making sure that they will have access to the facilities and information they will require.
It is critical that any crisis response and crisis management plans interact with the local emergency services, such as fire, police, ambulance, and rescue.
Crisis Response
As stated earlier, it is essential that crisis response procedures be developed for various emergency scenarios that may occur, including fire, flood, electrical problems, hazardous materials leak, and medical problems (e.g., Avian flu).
In developing these crisis response procedures, consideration must be given to the existing emergency responses such as evacuation procedures and emergency action procedures (e.g., firefighting) to ensure that they are not compromised by the development of the crisis response procedures.
The crisis response procedures are to cover the crisis response team's role and responsibilities, which include:
-
Liaising with emergency services
-
Escalation to the crisis management team
-
Activation of the crisis command center
-
Securing the damaged site (if applicable)
-
Dealing with affected staff, injuries, families, and so on
-
Damage assessment
-
Liaising with the media
The crisis response procedures must integrate into the crisis management plan and crisis communication plan to ensure that there are no gaps.
Crisis Communication Plan
Effective communication with key stakeholders is the key to good crisis management. There are many examples of organizations that have adequately addressed the actual problem/incident but lost credibility due to poor communications, particularly media management. Conversely, there are others who handled communications so well following a serious incident that they were embraced by the public and actually increased market share.
Therefore, it is essential that a crisis communication plan be developed, as we discuss in more detail later in this report.
Crisis Command Center
The development of a crisis management plan requires the establishment of a crisis command center from where the effective management of the emergency response is coordinated.
Depending upon the organization's business model, geographical location and diversity of operations will influence the location of the crisis command center. If we assume for the purposes of this report that the organization has a head office with branch operations geographically spread across the country, then there may be two crisis command centers, one located at the head office, for a branch-based crisis event, and the other outside of the head office, which will cater to a crisis event that may impact the head office location.
The crisis command center should have all the necessary facilities to address an extended period of crisis and must be maintained in a state of readiness. Facilities include those seen in Table 2.
Table 2 — Facilities for a Crisis Command Center
| Office | Information |
| Tables, chairs, filing cabinets, whiteboards, flip charts | Videoconferencing |
| Multifunction unit(s) (photocopier, scanner, printer) | Media center |
| Dedicated and specialist printers (e.g., check printers) | TVs, radios |
| Fax machine(s) | Computers (desktop, notebook) |
| Stationery, including company letterhead, checks, and so on | Data and voice communications |
| Catering facilities | Backup copies of the various business continuity plans, including:
|
| Separate breakout rooms for assigned teams | |
Developing and Implementing a BCP
The objective of this section is the design, development, and implementation of the business continuity plan that will meet the business recovery requirements.
BCP Documentation
The most popular tool to document a BCP is word-processing software (e.g., MS Word). However, a number of suitable software packages have been designed specifically for BCPs. To select the appropriate software, consideration should be given to the following:
-
Software organizational parameters:
-
The complexity of the various plans
-
The skill set of the personnel assigned the responsibility for updating the various plans (this is where the various plans have been decentralized)
-
Physical location of the personnel
-
The availability of organizational resources (e.g., hardware, inhouse software support, training)
-
-
Software selection criteria:
-
The software tool's compatibility with the organization's software architecture (detailed in the IT strategic plan)
-
Support and ongoing maintenance from the software vendor
-
Price and performance of the software
-
Ease of use
-
Functionality (including export of text and graphics)
-
Report generation
-
Query capabilities
-
Security
-
Capacity
-
Remote access, via Internet
-
Each type of software tool — word processing, database products (e.g., MS Access), and BCP software — will have its strengths and weaknesses. Ensuring that the most appropriate software tool is selected may require a detailed evaluation of each of the products in accordance with the organization's systems development methodology. This requirement may be waived where it has been decided that a word-processing package will meet the basic requirements.
The systems development methodology generally requires the following:
-
A user requirement document should be prepared, detailing:
-
The mandatory and desirable functions of the software in order of priority
-
Installation, testing, and implementation requirements
-
Hardware and software architecture (compliance with the organization's IT architecture)
-
This will reduce the number of software packages for detailed evaluation and testing.
-
The user requirements should be matched to those of the selected software packages. The mandatory and desirable requirements are to be compared to those offered by the software package(s) to eliminate those software packages that do not meet the requirements.
-
Each short-listed software package must be tested. As software vendors are reluctant to provide a full version of the software on an evaluation basis, a demonstration version will probably be used.
-
The reasons for acceptance or rejection of each software package should be documented.
On a periodic basis, the software tool needs to be revalidated, specifically where, due to organizational changes (e.g., change in hardware and software architecture, IT strategic plan, organizational growth and expansion), the BCP continues to grow/expand in size and complexity. The software tool(s) may not continue to have the capacity and functionality to meet the BCP maintenance requirements.
Plan Format and Structure
Various BCP formats and structures can be utilized. It is a matter of deciding which style fits the organization's mode of operations. When designing the plan, DRI International's "Professional Practices for Business Continuity Planners" [3] suggests the following:
-
Plan designs and structures:
-
Define how plan structures are tied to the organization
-
Document structure and design of plans
-
Ensure the format and structure facilities ease maintenance
-
Define the process for gathering data required for plan completion
-
-
Allocate tasks and responsibilities:
-
Identify tasks to be undertaken
-
Identify necessary teams to perform required tasks
-
Assign responsibilities to teams
-
Identify and list key contacts, suppliers, and resources
-
Plan Content
Again, depending upon the style of the plan, the content may vary. However, DRI International's guidelines suggest the following for the BCPs:
-
General information:
-
Introduction
-
Scope
-
Objectives
-
Assumptions
-
Responsibility overview
-
Testing
-
Maintenance
-
-
Plan activation:
-
Notification
-
Primary
-
Secondary
-
Disaster declaration procedures
-
Mobilization procedures
-
Damage assessment concepts
-
Initial
-
Detailed
-
Team members
-
-
Team organization:
-
Team description
-
Team organization
-
Team leader responsibilities
-
-
Policy statement
-
Crisis command center:
-
Location
-
Facilities description
-
Security access procedures
-
Detailed procedures are documented for each team, including the execution, sequence, responsibility, and timeline. For example, DRI International's guidelines [3] suggest the following:
-
Essential business functions:
-
Information protection and recovery
-
Activation actions
-
Disaster site recovery and restoration actions
-
End-user computing needs
-
-
Action sections:
-
Recovery team
-
Personnel
-
Responsibilities
-
Resources
-
-
Action plans:
-
Specific department and individual plans
-
Checklists
-
Technical procedures
-
A number of steps are to be undertaken to implement the BCPs, as listed below:
-
Determination of the plan owner's role and responsibilities
-
Establishment of processes for:
-
Distribution and control of the various plans
-
Distribution and control of the results of any plan exercises
-
Distribution and control of plan changes and updates
-
-
Security of the offsite copies of the plans
-
Maintenance of version control over the plans
-
Maintenance of any documentation (e.g., contracts) that supports the plans
Awareness and Training Programs
The objective of this section is to develop and maintain corporate awareness and to enhance the skills required to develop and implement the BCM program.
Once the plans have been developed, tested, and documented, it is important that a business continuity awareness program be implemented. The business continuity awareness program is to be driven corporately for large organizations. This will provide some level of assurance that the program will be comprehensive and cost-effective.
There are a number of segments to the business continuity awareness program, including:
-
BCP policy
-
BCP maintenance regime
-
Communication plan, for example:
-
Posters
-
Newsletters
-
Mouse pads
-
E-mails
-
-
Training program:
-
Types training
-
Employee induction program
-
Employee training program
-
Occupational health and safety
-
E-learning
-
Disaster scenario testing training
-
Crisis management plan
-
Crisis communication plan
-
Business continuity plan(s)
-
Disaster recovery plan
-
Building evacuation plan(s)
-
Emergency action plan(s)
-
Employee Induction Program
Business continuity education for employees must start from the beginning of their employment and be ongoing throughout their career within the organization. The employee induction program introduces the employee at a high level to the organization's policies and processes. It is here that the employee is first introduced to the organization's business survival strategy.
In the business continuity segment, the concepts of business continuity are outlined and discussed. Further, an explanation is given with examples of how the employee's future role and responsibilities may interact with the organization's business continuity processes.
Employee Training Programs
Organizations offer education programs (inhouse, external, or by professional associations) to enhance employees' skill set. In many of these education programs, business continuity is included. However, for inhouse-developed education programs, there is a need to ensure that business continuity is included and builds on what was presented in the employee induction program. This will ensure that employee awareness of business continuity is maintained and enhanced.
Business Continuity Training Program
Many organizations have either developed their own business continuity training program or utilize the services of external parties (e.g., DRI International or BCM Consulting). This type of training program targets employees who will have responsibility for the development and maintenance of the BCP for either their business unit or the organization.
The business continuity education program extends to the various business continuity testing programs that cover:
-
Crisis response
-
Crisis management
-
Crisis communication
-
BCP
-
Disaster recovery
-
Building evacuation
-
Emergency action plans
It is critical that the business continuity education program is ongoing to ensure that in the event of a disaster, the business will minimize the loss of life and/or injuries to employees and organizational assets while recovering to survive.
Testing, Exercising, and Maintaining the BCP
The objective of this section is to structure comprehensive and effective test exercises to ensure that the plan will work as designed.
BCP Testing
The objectives of performing BCP tests are to ensure that:
-
The recovery procedures are complete and workable
-
The competence of personnel in its performance of recovery procedures can be evaluated
-
Such resources as business processes, IT systems, personnel, facilities, and data are obtainable and operational to perform recovery processes
-
The manual recovery procedures and IT backup system(s) are current and can either be made operational or restored
-
The success or failure of the business continuity training program can be evaluated
A number of tasks are to be undertaken for this section, including:
-
Defining testing strategies
-
Selecting the testing method
-
Defining test objectives and preparing test control plans, including testing scripts for staff (and external resources)
-
Coordinating organizational resources to undertake the testing
-
Conducting tests utilizing organizational and IT infrastructure resources
-
Documenting testing deviations from recovery processes
-
Preparing a post-test report
-
Taking appropriate action to amend the BCP based upon post-test report recommendations
There are various levels of business continuity testing, as seen in Table 3.
Table 3 — Levels of Business Continuity Testing
| Level | Description |
| Level I | Desk checking (i.e., a structured walkthrough) of selected organizational business units' critical business processes (as identified in the business impact analysis) using the business continuity plan procedures for various disaster scenarios (e.g., fire destroying building). |
| Level II | Recovery of selected business units' critical business processes (as identified in the business impact analysis) using business continuity plan recovery procedures. This level may include the recovery of critical IT systems (requires coordination with the IT service provider) and assembly of recovery personnel at an alternate location. |
| Level III | Recovery of all of the business units' critical business processes (as identified in the business impact analysis) using business continuity plan recovery procedures. This level is to include the recovery of critical IT systems (requires coordination with the IT service provider). This may also require coordination with other organizational divisions or business units. |
It is critical that a post-test review be conducted to ensure that the lessons learned to improve the various plans are acted on. An example where this did not occur is the case of a financial organization that identified, from testing insufficient data communications, capacity to meet production requirements between the recovery site and the IT outsourcer's data center. Testing analysis indicated that a 10-megabyte data communications link was required. The testing recommendation was not acted upon.
Some 12 months later, a major incident (the building next door had a fire, and there was no access to the organization's building for three days) resulted in the decision to invoke the BCP and for the relocation of critical staff to the recovery center. While at the recovery center, those involved quickly discovered that there was insufficient capacity to meet operational requirements. Fortunately, the organization's telecommunications carrier was able to upgrade the line within 24 hours without significant financial loss or reputational damage.
Plan Maintenance
The objective of this section is to develop processes to maintain the BCP in a state of readiness. This is considered to be an integral part of the risk management program. Management must be made to see that there is a need to build and fund processes that will ensure the BCP remains in a state of readiness.
The tasks to be undertaken for this phase are:
-
Determining the ownership and responsibility for maintaining the various BCP strategies within the organization
-
Identifying the BCP maintenance triggers to ensure that any organizational, operational, or structural changes are communicated to the personnel who have the accountability for ensuring the plan remains up to date
-
Determining the maintenance regime to ensure the plan remains up to date
-
Determining the maintenance processes to update the plan for static and dynamic review points and testing results
-
Implementing version control procedures to ensure that the plan is maintained and up to date
-
Developing a business continuity awareness program
Maintenance Review Points
Ideally, a combination of the following three processes will ensure that the business continuity plan remains up to date:
-
Maintenance
-
Static reviews
-
Dynamic maintenance review
It is critical that review processes be established and continually maintained to ensure that the business continuity plan is kept in a state of readiness rather than rely on static reviews to identify that the plan is not up to date. A static review is a cyclical maintenance process whereby the BCP is reviewed at predetermined times. An annual review is a typical example of a static review regime.
Dynamic maintenance reviews happen when a strategic change occurs (e.g., with an organizational restructuring or the integration of a new business).
An understanding of the dynamics of the organization's operational processes is required in order to identify the potential points of change. There are a number of key areas in which a change may occur. The maintenance process needs to be implemented to ensure the detection of changes in any of the critical areas, including those in information technology or changes to a building's maintenance program.
Let's look at a couple of examples. The first involves a banking organization that did not embed business continuity maintenance dynamic review points into its IT processes; this resulted in a major outage of 12 hours after an incident occurred during an upgrade to the organization's head office telecommunications switch. No business continuity risk assessment had been performed. Therefore, no contingency plan was developed in the event of an incident to minimize the impact and to reduce the likelihood of invoking the business continuity plan.
In the second example, a large insurance company had implemented a program to lower the cost of doing business to remain competitive. Part of the program was to reduce the cost of building maintenance, and one of the cost-reduction actions was to change the testing regime of the building's emergency power (diesel generator) from monthly to annually.
The annual maintenance regime included a cursory inspection of the diesel generator hoses and running the generator for 15 minutes to identify any major problems. However, there was no base load test included as part of testing the diesel generator — that is, connecting the building's emergency services (fire, lighting, etc.), elevators, air-conditioning, and so on, to the generator to place it under load to identify any weaknesses (e.g., the capability of the hoses to withstand the load).
Therefore, the failure to include the base load test did not test that the hoses had deteriorated to such an extent that, when required in an emergency, the hoses were unable to cope with the power demand and failed. If the manufacturer's recommended testing regime had been followed, including the base load test, then the generator's hoses' deterioration would have been detected.
The result of the failed diesel generator included:
-
A number of staff members were trapped in elevators for an extended period.
-
Customer service was severely disrupted, leading to a large number of complaints.
-
Reputational damage occurred, as the incident was broadly reported in the various news media.
-
The financial regulator asked some very hard questions of the organization's executive management regarding its risk management regime.
Table 4 provides an example of a BCP maintenance schedule.
Table 4 — BCP Maintenance Schedule
| Business Continuity Plan Component | Static Review Cycle (Months) | Dynamic Review Events | ||
| 3 | 6 | 12 | ||
| Chapter 1: Introduction/Overview | X | Strategic changes | ||
| Chapter 2: Emergency Evacuation Procedures | X | Organizational and structural changes (buildings, etc.) | ||
| Chapter 3: Escalation Procedures | X | Strategic changes and/or business process changes | ||
| Chapter 4: Plan Activation Procedures | X | Strategic and/or organizational changes; information technology | ||
| Chapter 5: Recovery Team Procedures | X | Strategic and/or organizational changes; business process changes | ||
| Chapter 6: Maintenance and Testing | X | Strategic and/or organizational changes; business process changes; information technology; service-level agreements | ||
| Contact Listing | X | Changes in personnel, emergency services, third-party service providers | ||
| RESOURCE LISTINGS | ||||
| Building Facilities | X | Organizational and structural changes (contractors, etc.) | ||
| Information Technology | X | Software modifications/ implementation; hardware changes/network changes; service-level agreements; change in outsourcers | ||
| Personnel | X | Personnel changes/organizational changes | ||
| Third-Party Service Providers | X | Renewal of contracts; service-level agreements; change in outsourcers | ||
Crisis Communications
The crisis communication plan is the glue that provides essential information to the internal and external stakeholders. Without effective communication, the activation of the various plans will not be coordinated to deliver the desired outcomes, such as recovery within the maximum tolerable outage time frame and minimizing reputational damage (i.e., protecting the organization's "brand"). The sidebar "Emergency Media Response Guidance" lists some dos and don'ts regarding dealing with the media.
Preparation for Media Interviews/Questions
-
Determine background information to answer such media questions as:
-
What exactly happened?
-
Has anyone been injured, if so, how many and to what extent?
-
What caused it?
-
What disruption is there to customers and for how long?
-
Are there alternate services? Where?
-
-
Prepare for a confrontational/aggressive line of questioning, such as:
-
Who is to blame? When will the party "at fault" be dealt with? How?
-
When did the organization discover the problem? What did it do before it became a crisis, and what is it doing now?
-
How can the interests at stake be protected and/or compensated?
-
-
Look for any good news stories (e.g., heroics).
Remember the following key points:
-
Managing perception is often more difficult than managing the problem.
-
The media can be a powerful friend — or foe — during a crisis.
Staff Information Updates
Staff morale can be affected during a crisis, particularly when individuals are uninformed. They may speculate, usually envisioning a worst-case scenario, or they may have concerns about their job security. Various methods can be used during a crisis to disseminate information, including:
-
Staff information hotlines (telecommunications services carrier)
-
The intranet (if available)
-
Web site (if available)
-
Voice mail
-
Telephone contact via their managers
Coordination with External Agencies
This section's objective is to develop procedures and policies for coordinating response, continuity, and restoration activities with external agencies (local, state, national, emergency services, etc.) while ensuring compliance with applicable statutes or regulations. There are a number of steps that need to be undertaken, as we discuss below.
Identify Applicable Laws and Regulations
Identify applicable laws and regulations for the industry in which the organization participates by contacting local and government agencies (e.g., emergency services, police) and determine their requirements for inclusion in the crisis response and crisis management plans.
It may be necessary to submit the plans to the local and government agencies for review (and approval) to ensure compliance with their specific requirements.
Test Exercises with External Agencies
Depending upon the organization's industry sector, the company may have to participate in local and government agency emergency testing exercises. Where this occurs, it is necessary to coordinate the organization's testing exercises with the local and government agencies to minimize the impact and cost on the organization.
CONCLUSION
Business continuity is a business survival strategy for an organization. Executive managers who fail to take action to protect their organization will be held accountable by the shareholders, strategic business partners, regulatory authorities, and other interested parties.
Business continuity is an integral part of an organization's day-to-day business processes. Without this integration, the organization's ability to survive a disaster significantly increases as the organization continues to change to meet the dynamic requirements of today's business environment.
A strong business continuity environment provides assurance to the organization's executive management that in the event of a disaster the organization is in a superior position to survive.
The value of business continuity planning is appreciated only in the event of a crisis and or disaster.
REFERENCES
1. Doughty, Ken. "Selecting the Right Business Continuity Strategies." EDP Auditing, Auerbach Publications CRC Press, 2000.
2. DRI International. "Business Continuity Glossary." Disaster Recovery Journal (www.drj.com/glossary/drjglossary.html).
3. DRI International. "Professional Practices for Business Continuity Planners," 28 August 2003 (www.drii.org/DRII/ProfessionalPractices/about_professional_detail.aspx).


