Enterprise-Wide Risk Management: Taking Off on the Wings of a CRO
As described in Cutter Consortium's Business-IT Strategies Executive Report, " The New Risk Management" (Vol. III, No. 9), today's business environment contains more diverse kinds of risks and rewards than ever before, ones that few organizations have much, if any, experience in managing.
Obstacles to Getting More from IT
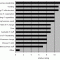
Cutter Consortium's online business-IT strategies survey asks respondents to identify the leading obstacles to getting more from information technology in their companies. Figure 1 summarizes the results, which are surprising in some areas. See how the results compare to your situation, and consider how these obstacles can be overcome.
The Variety of Servers
The term "server" has become a seriously overused word. There are hardware platforms called servers and there are operating systems called servers (e.g., Windows 2000 Server). At the same time that Microsoft has called one of its 2000 systems a server, it has included a variety of utilities inside Windows that it also calls servers (e.g., Microsoft Transaction Server [MTS], Microsoft Message Server).
November 2000 Component Development Strategies
Paul Harmon, Editor
Beyond Supply Chain Management: Supply Chain Synthesis and Technology
You can't spell business without "e." And business-to-business (B2B) e-commerce is hot right now. Analysts predict that B2B sales over the Internet will reach US $500 billion by early next year and be up to $2 trillion by 2004 (it is possible that they may even reach $10 trillion).
Beyond Supply Chain Management: Supply Chain Synthesis and Technology
Analysts predict that business-to-business (B2B) sales over the Internet will reach US $500 billion by early next year and $2 trillion or more by 2004. In contrast, business-to-consumer (B2C) e-commerce sales are not expected to reach $400 billion until 2003. Business analysts believe that B2B will cut costs, reinvent supply chains, improve communications, and increase customer satisfaction.
The Use Of Component-Based Application Servers
In this Executive Update, we'll take a look at the latest data from Cutter Consortium's ongoing survey on components/distributed computing and their relationship to component-based application servers. (We used the term component-based application servers on the survey to distinguish it from other application server uses, ranging from hardware servers to HTTP or Web servers.)
Crossing the Object-Data Divide
The norm for software development today is to use object-oriented (OO) and component-based technologies -- such as Enterprise JavaBeans (EJB), Java, and Microsoft's C# -- in combination with relational database technology such as DB2 or Oracle 8i.
November 2000 IT Metrics Strategies: Introduction
Two common metrics for software size are source lines of code and function points. But by no means are these the only units of size; others include objects, modules, programs, components, and frames. Obviously there are scaling relationships between these abstractions. How can you translate one from the other to understand the proportional aspects of one metric to the next? If you knew the size of a major application in source lines of code, is there a way to equate the size using a metric like function points for people who speak that language?
Using "Backfiring" to Accurately Size Software: More Wishful Thinking Than Science?
Functional size measurement is a fairly recent concept to be embraced by the IT industry. But, increasingly, the method of function point (FP) analysis, as maintained by the International Function Point Users Group (IFPUG), is establishing a position within the field of software measurement.
Determining Your Own Function Point and Lines of Code Proportions -- Three Things to Watch Out For
Understanding the inventory of IT applications is considered to be of high strategic value for organizations interested in IT benchmarking. For some, the purpose might be to better estimate future projects. Others might be embarking on a process improvement strategy and want to know how various IT groups perform relative to one another. A third group could include IT organizations involved in outsourcing or partnering, and they might need this information to quantify the respective roles and productivity commitments.
Measuring the Software Process
Measuring the Software Process by William Florac and Anita Carleton (Addison-Wesley, 1999) is a self-contained statistical process control (SPC) foundation in the context of software process improvement (SPI).
Data Warehousing and Business Intelligence Standardization Efforts
Data warehousing and business intelligence (BI) are no longer just about building a central repository where a company's data, sourced from multiple databases, is maintained in a static manner and analyzed on a "need be" basis.
BizWorks: Enterprise Application Integration Meets ENterprise Business Intelligence
Implemented on an enterprise scale, e-business requires integrating Internet applications with not only your core operational systems -- enterprise resource planning (ERP), supply chain, customer relationship management (CRM), data warehouse, etc.
Researchers Apply Data Mining to Predict Internet Traffic
Researchers at the Statistics and Data Mining Research department at Bell Laboratories/Lucent Technologies and MCNC's Next-Generation Internet (NGI) Research project (which develops technologies that enable networks to scale dramatically to accommodate extreme ranges of user demand) are
Oracle 9i for Business Intelligence
In the September and October 2000 BIAs, I covered a number of products useful for conducting business intelligence (BI) for personalizing online operations. Recently, I had the chance to examine the BI enhancements Oracle is making to the next version of its flagship database and application server platform -- Oracle 9i.
Light Methodologies: It's Like Déjà Vu All Over Again
When we saw that the November issue of the Cutter IT Journal was devoted to light methodologies, we knew we wanted to write an article. We have always had an academic and practical interest in methodologies. We have implemented a few, and Steve even created one. So it was with great interest that we started to look into this new genre of light methodologies (LM) and Extreme Programming (XP).
An Iteration in the Life of an XP Project
ThoughtWorks, Inc. is a Chicago-based system integration and consulting company of around 300 people. We specialize in building demanding business applications using technology that is both new and strategic for the industry. We also work on complex business applications that usually require stitching together various components and augmenting these components with complicated and changing business logic.
Emergent Control in Extreme Programming
Lightweight methods rely on emergent control rather than having decisions flow down from the big boss. Robust control can emerge from the interaction of locally optimizing rules. Extreme Programming (XP) relies on emergence at all levels of control -- project planning, personnel, architecture and design, verification and validation, and integration.
Balancing Lightness with Sufficiency
It is clear to most people by now that no one methodology will fit every software project. What is not clear is where to go next. If concrete advice can't be given across projects, how are we to find meaningful methodological advice for our projects?
Against a Sea of Troubles: Scrum Software Development
In Sebastian Junger's The Perfect Storm, a fishing boat out of Gloucester, Massachusetts, USA, encounters a storm -- not just any storm, but "the perfect storm" -- and ends up meeting a tragic end. This "perfect storm" was the result of a combination of various meteorological phenomena. Together, these phenomena made it impossible for the fishermen to do their job and bring swordfish back to port.