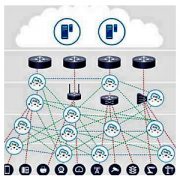
With the deployment of next-generation mobile networks, IoT and edge, and fog and cloud computing, the tech world is undergoing the largest-ever overhaul of its information service infrastructure. In this connected-everything/data-everywhere model, the benefits are numerous, but so are the challenges to system security. The OpenFog Reference Architecture for fog computing has emerged as a highly credible paradigm for architecting compute-intensive solutions for networks and applications that utilize IoT, 5G technologies, and AI. This Advisor describes three distinct aspects of an approach to node-centric security in an open, interoperable fog computing environment that are critical to understanding how fog bridges gaps in the continuum between the cloud and things.
Advisor
Don’t have a login?
Make one! It’s free and gives you access to all Cutter research.



