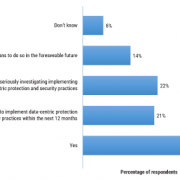
Data-centric protection and security focuses on the organization's sensitive data as opposed to its overall computer networks and applications, as is the case with the more traditional IT security models that typically operate by implementing a well-defended security perimeter designed to keep bad actors out. This is accomplished by locating, identifying, and cataloging sensitive data as well as by applying encryption, data masking, and policy-based data access controls (and end-user monitoring) to protect data residing across multiple enterprise environments. But to what extent are organizations adopting, or planning to adopt, data-centric protection and security practices?
Advisor
Adoption Trends for Data-Centric Protection and Security
By Curt Hall
Posted March 14, 2017 | Technology |
Don’t have a login?
Make one! It’s free and gives you access to all Cutter research.


