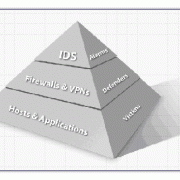
Historically, corporate security teams have focused the majority of their efforts and budgets on perimeter security systems: firewalls, network-based intrusion detection systems (IDSs), and virtual private network (VPN) servers. But by themselves, perimeter systems present a very skewed image of malicious or damaging activity on a corporate network.
Thinking Inside the Box: The Importance of Real-Time Log Monitoring for Network Security
Posted April 30, 2002 | |
Don’t have a login?
Make one! It’s free and gives you access to all Cutter research.

