Using Zoom; Is It Safe?
Cutter Consortium uses Zoom for virtual training, meetings, and webinars. Below are some answers to questions you may have about Zoom security. If you have further questions, please ask; we are happy to talk with you about our virtual meeting and event delivery. You can also find more on Zoom security at the Zoom site.
Q: Do I need a license for Zoom?
A: If you are invited to a Zoom meeting, you do not need a license.
Q: There has been bad press about Zoom’s security. Can you explain what’s going on?
A: A correctly managed deployment of Zoom Enterprise, which Cutter Consortium uses, has the ability to define additional controls as standard to protect all users. These include, for example:
-
End-to-end encryption
-
Access to meetings to authorized users only (users need to be logged in and invited)
-
Meeting passwords
-
No host tracking
-
Expiring meeting IDs
-
Lobby functionality – thereby requiring the host to admit people
All of these controls are in line with Zoom’s competitors, such as Teams, Skype, WebEx, GoToMeeting/GoToWebinar, etc.
The bad press is primarily about Zoom’s free-tier application, which has some limitations in functionality. Most “new” technology companies offer free or free-tier products as an entry point to gain as many users on their platforms as possible, with the intention of converting a percentage of those users into paid customers. The saying, “If you are not paying for the product, you are the product,” is very true. In fact, one of the most popular KPIs for boards and investors in these types of tech companies is “Conversion to paid.” By design, they want you up and running as quickly as possible — no complicated screens to get through, just click and run. When using free products, the vendor tracks information about the user for two purposes: (1) target the free-tier user to try convert them to paid; (2) monetize the user’s data. Note that with Zoom, that data does not include the voice and video streams within the meetings, nor the contents of any files sent through the platform. This does not get exposed or sold to third parties.
Free-tier consumers are looking for ease of use and rapid results — with no learning curve. They don’t want to have to worry about security or complex configurations. Zoom offered just that, catching the interest of huge numbers of people who were scrambling to find a tool to communicate amid current events.
Q: What is “Zoom-bombing”?
A: There has been a lot of press recently about what they’re calling “Zoom-bombing,” where meetings have been interrupted by uninvited people, some behaving badly. Free-tier Zoom uses just a 10-digit numerical meeting code, so there is a possibility for someone to enter a meeting just by using 10 random digits. This could not be targeted, however; it would be completely random. There is no determinable relationship between the meeting ID code and the host, so you could not work out a code based on who is hosting the meeting. If the host is using a “default” meeting code that does not change, then there is a chance that these details could be inappropriately shared and then used maliciously. This is a human factor and is the same across all online meeting platforms.
Cutter Consortium configures its Zoom Enterprise meetings/webinars to mitigate this:
-
Cutter Consortium does not use the default meeting codes. Ensuring that meetings are created properly limits the likelihood of the details being shared too widely.
-
Cutter Consortium can customize meeting passwords to stop random meeting bombing.
Q: What other precautions will you take?
A: There are several features that Cutter Consortium can employ to enhance security:
-
Virtual waiting room. We can enable the virtual waiting room, ensuring every participant is scanned prior to admittance. If someone joins after the meeting/webinar begins, they will have to wait in the waiting room until they are admitted by the host.
-
Remove participants. Once an attendee has been admitted, we can easily push them back to the waiting room, remove them from the meeting altogether, and can even prevent their return.
-
Randomly generated meeting IDs. We always schedule new meetings with randomly generated meeting IDs. That way, only invited attendees will know how to join your meeting.
-
Passwords. We can take meeting security even further by requiring a password to join your meetings.
-
Restrict participants. We can restrict participants to those who are logged into Zoom, and can even restrict it to Zoom users whose email address uses a certain domain.
-
Screen sharing. Zoom gives us the ability to determine whether participants in the meeting can share their screens, or if we want to be the only one with that ability. We can easily toggle this feature on and off from the screen-sharing menu, as well as from the security menu.
-
Denying reentry. An attendee can be removed from any meeting at any point. For additional security, we can also choose to not allow participants to re-join once they’ve been removed.
Q: Do you have any technical insight re: security?
A: Zoom is encrypted. Within the platform, the encryption is fully end-to-end. There has been some misrepresentation in the press recently regarding the definition of end-to-end encryption. Here are the important points:
-
When using the Zoom client (Mac, Windows, iOS, Android, and Linux), it is fully encrypted end-to-end. If both sides of the meeting are using the Zoom client (PCs, Macs, Tablets, Mobiles), then the session is truly encrypted end-to-end: Zoom client to Zoom cloud via HTTPS, TLS1.2 and AES-256.
-
When using Zoom via a web browser, it is fully encrypted end-to-end. If one or many sides of the meeting are being accessed via a web browser, then the session is truly encrypted end-to-end: Zoom client and browser to Zoom cloud via HTTPS, TLS1.2 and AES-256.
-
When accessing a Zoom meeting via a third-party device or service, such as dialing in via an SIP phone, there is no true end-to-end encryption, it is not possible! The sessions within the Zoom environment are fully encrypted end-to-end. However, the people calling into the meeting via other devices (phones, etc.) are leveraging the communication protocol that is native to that device. While this may in truth be encrypted, it cannot be classed as true end-to-end encryption.
This last point is not an issue unique to Zoom, as it is the same across all competitive platforms. But this is where the popular press recently has focused on Zoom as the “new kid on the block.” Zoom has publicly responded to this and has subsequently updated its terms of service and privacy policies to clarify this.
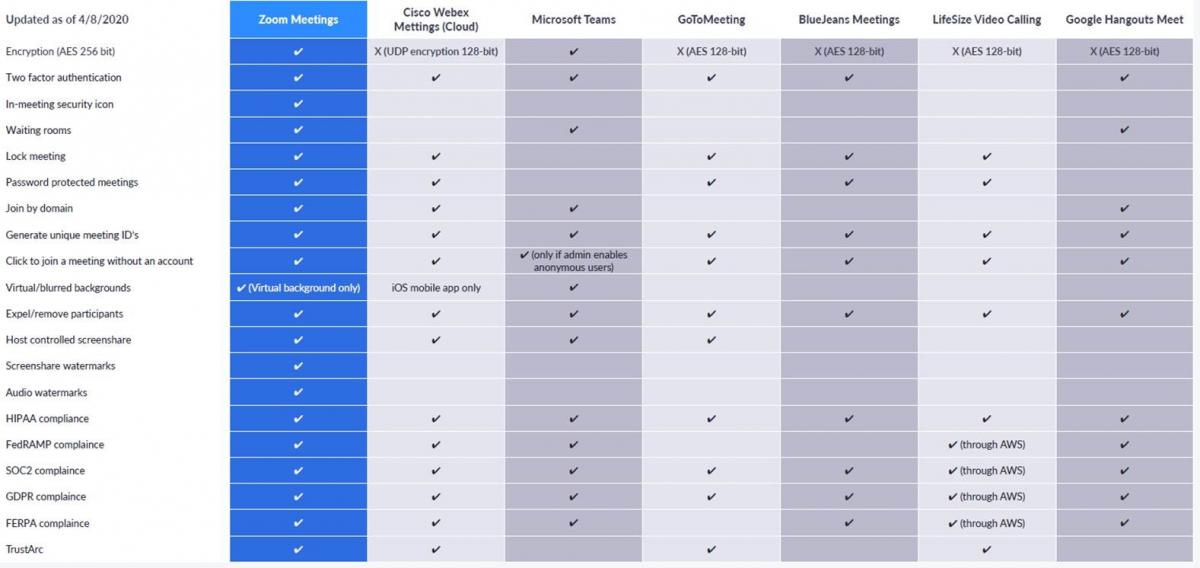
Below is a matrix of the most popular video platforms and their comparative security controls. A correctly configured Zoom meeting is as secure, if not more secure than most. More on Zoom security