A Leadership Perspective on Lean-Agile Business Intelligence
With greater clarity on "True North," effective measurement, and transparency, this Executive Update demonstrates how we can apply Agile methods to BI applications in a way that ties directly to customer value.
Integration and Divestment: Some Important Considerations
Integration and Divestment: Some Important Considerations
Integration and Divestment: Some Important Considerations (Executive Summary)
Integration and divestment form a key part of many corporate strategies. In line with that activity, enterprise architecture (EA) deals with integrating architectures from two or more organizations as they merge or split off architectural components for sale or divestment just as much as it has to support the evolution of architecture within an enterprise.
Integration and Divestment: Some Important Considerations (Executive Summary)
Integration and divestment form a key part of many corporate strategies. In line with that activity, enterprise architecture (EA) deals with integrating architectures from two or more organizations as they merge or split off architectural components for sale or divestment just as much as it has to support the evolution of architecture within an enterprise.
The Land of Snow, Ice, and Proactive Decision Making
The Yin-Yang of Agile
Customer Satisfaction: The Importance of Keeping a Balance
In the services industry, the importance of customer satisfaction is so apparent that it can hardly be overemphasized. To achieve customer satisfaction, we not only aim at meeting customers’ needs but also advocate the concept of exceeding their expectations by going the proverbial “extra mile” from time to time. But how far should we go in order to satisfy the customer?
Hackers and Malware Are Getting Smarter
Economically Sensible Scrum: Making Quick, Correct, and Understandable Decisions When Applying Agile
The simple truth is that performing the mechanics of Agile or Scrum well at the team level is just not enough to ensure that you will see all the benefits you should. Let me say that in another way: having teams perform Scrum or any Agile process exactly right, in a textbook-like fashion, does not guarantee you will achieve your organization's goals for adopting Agile.
The Internet of Things: Lots of Data, Lots of Opportunities -- Part II
In part I of this series of Advisors, I discussed the "Internet of Things" (IoT) and its industry/business counterpart the "industrial Internet" (see "The Internet of Things: Lots of Data, Lots of Opportunities -- Part I").
The Internet of Things: Lots of Data, Lots of Opportunities -- Part II
In part I of this series of Advisors, I discussed the "Internet of Things" (IoT) and its industry/business counterpart the "industrial Internet" (see "The Internet of Things: Lots of Data, Lots of Opportunities -- Part I").
The Internet of Things: Automation Heaven or Security Hell?
This Executive Update describes the good, the bad, and the ugly, and sounds a warning for all implementers and adopters of this new technology.
The Internet of Things: Automation Heaven or Security Hell?
This Executive Update describes the good, the bad, and the ugly, and sounds a warning for all implementers and adopters of this new technology.
Cyber Security: Inside and Out
What Scaling Agile Is About
On the Herding of Corporate Cats
As the workforce becomes better educated, more technology-savvy, and more flexible in handling job assignments, the pace of change will increase. Development of new management styles is now becoming imperative. These emerging management styles are already beginning to demonstrate significant benefit across a growing range of activity.
Toward a High-Performing Culture of Resilience
Traditionally, risk management is advocated and assumed to be a self-evidently correct framework. It offers a planning method for individual risks yet ignores systemic, complex risk and uncertainty. Often, ways of managing risk are established based on compliance with process. The process itself and its application are not themselves questioned.
Herding a Hurricane: Implementing and Managing API Programs
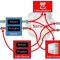
In this issue we take a close look at application programming interfaces (APIs). Now, APIs are both perennial and ubiquitous in computing. They've been around since the beginning and occur at every level of the IT stack -- from software-hardware interaction through system software to applications. They reside in protocols, libraries, and frameworks; in fact, they are intrinsic to the design of programming languages themselves. This raises the question: how can something so commonplace be causing so much excitement?
API Program: Strategic or Tactical?
We have examined the results of CBR's survey on the implementation and management of an API program, trying to analyze not only what the survey tells us directly, but also the "white space" between the survey questions and answers. This admittedly involves some speculation on our part. However, comparing what would logically be expected from the theory of what the API economy is, with what the survey reveals, gives us some interesting insights.
Develop New Partnerships and Distribution Channels Using APIs
Over the last decade, consumers have leveraged the Internet and phones to interact with businesses and thereby obtain a degree of self-service that did not exist before. These systems have provided consumers with access to information and the ability to execute transactions from anywhere. However, in the last few years we witnessed a drastic change in consumer behavior as smartphones started flooding the market and applications were developed to do almost everything from mobile devices.