Mobile Devices, Marketing, and Content Management Systems
In past Executive Updates, I have examined various issues relating to executing mobile applications in response to increased consumer demand for access to websites via mobile devices as well as some decision frameworks for determining the best operating system for your organization's mobile applications.
IT Value Creation
A remarkably prescient group of early technology pioneers first conceived the vision underlying modern, Internet-based IT value creation. In a 1945 Atlantic Magazine article, "As We May Think," Vannevar Bush anticipated the interconnectedness and indexing structures of the Web. Later, in 1968, J.C.R.
Reframing Frameworks: Part III -- The Information FrameWork
Agile Code
Much like agile requirements aim toward a goal, agile engineering practices help teams write code that meets the goals of an iteration and changes direction easily. To be an agile team, you need agile code. The agility of a code base is related to the architecture, development practices, and the delivery model. As working software is the main way of evaluating progress on an agile project, agile engineering practices can drive agile planning techniques when they are lacking.
Achieving Balance in Agile Adoption
In addition to changes in day-to-day practices, being agile requires a cultural shift across your organization. This Executive Update discusses how to balance agile values and practices when transitioning to an agile approach by using as examples three of the more common practices: pair programming, issue tracking, and unit testing.
What's New in TOGAF 9.1?
The Evolution of IT: Improving Organizational Capabilities and Promoting Business Value -- Part II
As we pointed out in Part I of this two-part Executive Report series, some may argue that IT's capacity to contribute to business competitiveness has faded, but we suggest instead that it has evolved and expanded, maturing and changing within a subset of companies that have effectively managed to use IT in various ways. However, it's important to note that not all companies achieve equal success with their mature approaches to IT-based capability and value creation.
The Evolution of IT: Improving Organizational Capabilities and Promoting Business Value -- Part II
Although some may argue that IT's capacity to contribute to business competitiveness has faded, we suggest instead that it has evolved and expanded, maturing and changing within a subset of companies that have effectively managed to use IT in various ways.
The Evolution of IT: Improving Organizational Capabilities and Promoting Business Value -- Part II
Although some may argue that IT's capacity to contribute to business competitiveness has faded, we suggest instead that it has evolved and expanded, maturing and changing within a subset of companies that have effectively managed to use IT in various ways.
The Evolution of IT: Improving Organizational Capabilities and Promoting Business Value -- Part II (Executive Summary)
As we pointed out in Part I of this two-part Executive Report series, some may argue that IT's capacity to contribute to business competitiveness has faded, but we suggest instead that it has evolved and expanded, maturing and changing within a subset of companies that have effectively managed to use IT in various ways. However, it's important to note that not all companies achieve equal success with their mature approaches to IT-based capability and value creation.
Creating a Governance Brand with Your Own Lingua Franca
Tackling Today's Enterprise Security Challenges
The threats just keep coming in this new, interconnected world. DDoS attacks, internal security breaches, and even politically motivated "hacktivism" all but ensure that your organization will experience a security incident. Don't think if, think when.
How DDoS Attacks Defy Conventional Security Wisdom
Over the past 12-15 months, there have been numerous high-profile distributed denial of service (DDoS) attacks launched against very prominent organizations. The motivation of "hacktivism," combined with the swiftness with which these attacks can be launched and redirected at other organizations, has caused many in the information security industry to rethink the threat landscape.
Identity Management in Technology-Assisted Educational Systems
On that long list of venerable institutions primed for a high-tech overhaul, higher education is near the top. Its shortcomings are much discussed: universities are expensive, inaccessible, inflexible, and out of touch with the needs of students and the world economy.
Securing Mobile Platforms with Biometrics: Opportunities and Challenges
Every year, millions of migrant workers leave their homes, searching for work and career advancement.
Securing Mobile Platforms with Biometrics: Opportunities and Challenges
Every year, millions of migrant workers leave their homes, searching for work and career advancement.
Tackling Today's Enterprise Security Challenges
The threats just keep coming in this new, interconnected world. DDoS attacks, internal security breaches, and even politically motivated "hacktivism" all but ensure that your organization will experience a security incident. Don't think if, think when.
Enterprise Security Architecture for the New, Connected World
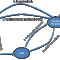
The ubiquitous and ever-changing technologies emerging in today's enterprise environment (cloud, social media, mobile devices, etc.) require a new perspective on enterprise security architecture (ESA). Effective enterprise risk management in this highly complex, heterogeneous, and seemingly "boundary-less" environment rests on the three pillars of information security in practice (see Figure 1):
Identity management
Security policy compliance
Cyber security architecture as defense
How DDoS Attacks Defy Conventional Security Wisdom
Over the past 12-15 months, there have been numerous high-profile distributed denial of service (DDoS) attacks launched against very prominent organizations. The motivation of "hacktivism," combined with the swiftness with which these attacks can be launched and redirected at other organizations, has caused many in the information security industry to rethink the threat landscape.
Identity Management in Technology-Assisted Educational Systems
On that long list of venerable institutions primed for a high-tech overhaul, higher education is near the top. Its shortcomings are much discussed: universities are expensive, inaccessible, inflexible, and out of touch with the needs of students and the world economy.
Identity Management in Technology-Assisted Educational Systems
On that long list of venerable institutions primed for a high-tech overhaul, higher education is near the top. Its shortcomings are much discussed: universities are expensive, inaccessible, inflexible, and out of touch with the needs of students and the world economy.
Securing Mobile Platforms with Biometrics: Opportunities and Challenges
Every year, millions of migrant workers leave their homes, searching for work and career advancement. Larger economic trading zones, changes in immigration rules, and the search for skilled staff have rapidly increased the movement of people both within and between the EU (European Union), other OECD (Organisation for Economic Co-operation and Development) countries, and non-OECD countries.