The Latest in Data Virtualization from Composite Software
This week, I spoke with the folks from Composite Software about the latest version of the company's data virtualization1 platform, Composite Enterprise Information Server 6.0. Composite Software's latest version adds new source data integration capabilities to the mix of sources it can access and integrate.
Are We Already Implementing Business Service Management?
Even though the concept of "business service management" (BSM) has been debated, advocated, debased, and promoted for years, the immaturity in articulating its mechanisms is still somewhat pervasive. Yet IT has been, is, and will continue to be hammered for being disconnected from the business needs of the customers that it serves unless something fundamentally changes within IT.
IT Reorganization: Part II
Business Architecture: Part I — Why It Matters to Business Executives
This Executive Update, the first in a series, discusses why business leaders should embrace business architecture as a means of addressing complex business challenges in ways that senior leadership can no longer ignore.
What Is a Complex Project Manager -- Really?
What Is a Complex Project Manager -- Really?
What Suppliers Say About Clients: Part II -- Managing Outsourced Services
In this two-part Executive Report series, we share in detail what suppliers have been saying to us and our colleagues about clients during the past two decades -- the things they wish clients would know or do as well as things they wish clients didn't know or do. In Part I, we covered the 10 statements suppliers make about establishing the outsourcing arrangement. Here in Part II, we examine another 10 pertaining to managing outsourced services.
What Suppliers Say About Clients: Part II -- Managing Outsourced Services
In this two-part Executive Report series, we share in detail what suppliers have been saying to us and our colleagues about clients during the past two decades -- the things they wish clients would know or do as well as things they wish clients didn't know or do. In Part I, we covered the 10 statements suppliers make about establishing the outsourcing arrangement. Here in Part II, we examine another 10 pertaining to managing outsourced services.
Why Do We Need or Want a Mobile Strategy?
Let's begin with the most basic of questions that senior executives are asking: "Why do we need or want a mobility strategy and, specifically, mobile applications for our existing and new customers and/or clients?" As one IT executive said, his challenge was convincing senior management that smartphones provide real business applications -- not just A
Why Do We Need or Want a Mobile Strategy?
Let's begin with the most basic of questions that senior executives are asking: "Why do we need or want a mobility strategy and, specifically, mobile applications for our existing and new customers and/or clients?" As one IT executive said, his challenge was convincing senior management that smartphones provide real business applications -- not just A
Corporate Use of Predictive Analytics: Part II -- Application Areas and Implementation
In February/March 2011, Cutter Consortium conducted a survey asking 60 end-user organizations various questions about the adoption and use of predictive analytics. The goal was to uncover corporate adoption trends and examine application development issues to discern how organizations are applying predictive analytics technology and practices to structured data analysis.
Ubiquity Is the New Sticky
In the early era of Web commerce, the strategic goal for all Web producers was to achieve and maintain "stickiness" -- the ability to attract repeat visitors to the producer's site. The site-centric Web, for all its disruptive impact on industry, still seemed an awful lot like the physical world of commerce.
Ubiquity Is the New Sticky
In the early era of Web commerce, the strategic goal for all Web producers was to achieve and maintain "stickiness" -- the ability to attract repeat visitors to the producer's site. The site-centric Web, for all its disruptive impact on industry, still seemed an awful lot like the physical world of commerce.
How Much Software Debt Do We Have?
In the past, teams could tell project stakeholders that software debt existed, but it was difficult to describe where and how much. Teams would increase their estimates for features that used to seem simple because it meant making changes to areas of the code they knew were infested with software debt. In the worst situations, teams would recommend a full rewrite of an application because the software debt was too difficult to work around anymore.
What Suppliers Say About Clients: Part II -- Managing Outsourced Services
Implementing a Technical Debt Prevention, Measurement, and Reduction Program in Your Company Webinar
In this on-demand webinar, Dr. Israel Gat presents the Cutter Technical Debt Framework. He describes the experience and insights gained by applying the framework in various Cutter client engagements. Dr. Gat puts special emphasis on critical success factors for making the technical debt initiative work for you, your company, its partners and its customers.
Risk Management = Testing
If we create a suitably accurate and comprehensive set of tests at the outset of the project -- tests for both performance and business functionality, the two primary reasons for project failure -- and apply those tests continually throughout the project, then the project can never fail on either basis.
Implementing a Technical Debt Prevention, Measurement, and Reduction Program in Your Company Webinar
In this on-demand webinar, Dr. Israel Gat presents the Cutter Technical Debt Framework. He describes the experience and insights gained by applying the framework in various Cutter client engagements. Dr. Gat puts special emphasis on critical success factors for making the technical debt initiative work for you, your company, its partners and its customers.
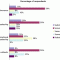
Corporate Spending Trends for Predictive Analytics
A survey conducted by Cutter Consortium in February/March 2011 offers some insight into corporate spending plans for predictive analytics.1 Specifically, when asked, "Does your organization plan to increase or decrease spending on predictive analytics and data mining this year (i.e., 2011) compared to last year?" participants responded as shown in Figure 1.
Evolution of Technologies to Prevent Data Leaks
The requirements from business for protecting confidential information are constantly growing, because the damage from disclosing such information may result in a loss of a company's competitive advantage and profits, sanctions by regulatory authorities, and even administrative and criminal liability. It is no secret that successful business performance depends on the confidentiality, integrity, and availability of corporate information.
Evolution of Technologies to Prevent Data Leaks
The requirements from business for protecting confidential information are constantly growing, because the damage from disclosing such information may result in a loss of a company's competitive advantage and profits, sanctions by regulatory authorities, and even administrative and criminal liability. It is no secret that successful business performance depends on the confidentiality, integrity, and availability of corporate information.
IT Reorganization: Part I
The recession and other financial woes of the last three years have affected almost every industry. Reorganization in one form or another, often accompanied by layoffs, became the norm. It is little surprise then that three-quarters of all organizations in a recent Cutter Consortium survey reported IT reorganizations during the period 2008-2010.
Do Cancelled IT Projects Leave a Carbon Footprint?
There was a recent story in USA Today about how venture capitalists have been pouring billions of dollars into startups that are targeting clean or "green" technologies, with billions more in investment on the horizon.1 The story noted that mainstream companies are investing billions in green technologies, too, as a way to save money and lower their social reputati
Do Cancelled IT Projects Leave a Carbon Footprint?
There was a recent story in USA Today about how venture capitalists have been pouring billions of dollars into startups that are targeting clean or "green" technologies, with billions more in investment on the horizon.1 The story noted that mainstream companies are investing billions in green technologies, too, as a way to save money and lower their social reputati