In the digital world, where actions take nanoseconds and commands are increasingly issued without human intervention, the traditional “measure and manage” approach to risk management is rapidly becoming obsolete, and “sense and respond” is a more appropriate approach. Attacks are increasing in diversity, frequency, and ferocity, necessitating a challenge to the accepted practice that cyber risk can be managed within the IT function. To build effective digital resilience, leaders must adopt a c-suite response, embracing both robust technology and organizational culture approaches.
Poor Threat Perception
The cyber-threat landscape is evolving at a pace that many boards find difficult to grasp. In today’s dynamic digital environment, new threats are emerging and organizations must fend off phishing attacks, DDoS, and malware at unprecedented levels.
Threat actors are not always cyber criminals; threats can also be state-sponsored and insider threats. Threat actors exploit organizations’ vulnerabilities, with severity ranging from data loss to physical damage. Understanding your organization’s position within the cyber-threat landscape is crucial to understanding your cyber-risk profile: organizations holding valuable information assets (e.g., customer data, financial transactions) are high-value targets.
The gap between the perception and reality of threat widens as you go up the leadership chain, with many executives and board members largely unaware of the threat landscape in which their organizations exist.
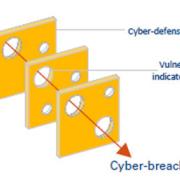
Cyber risk is a function of the threat posed, the system’s vulnerabilities, and its exploitability, as illustrated by the cyber Swiss Cheese Model (see Figure 1). A vulnerability can be defined as a weakness in the system; its exploitability is the likelihood of it actually being exploited. Reducing the exploitability of an organization’s vulnerabilities and improving their cyber defenses decreases the likelihood of a cyber breach.
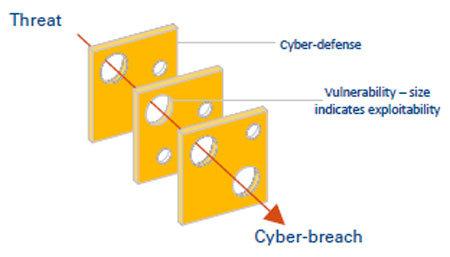
It is only in recent years that senior leadership has begun to recognize cyber risk as a core business risk. This has meant a history of a lack of organizational capability to protect against, detect, respond to, and recover from cyber incidents.
Digital Damage
A cyber attack’s damage may extend far beyond the digital domain, causing devastating reputational damage and financial losses. A holistic threat, such as a malware infection or server failure, can result in virtual damage, such as a data breach or operational loss, cascading into physical effects as well, with potential for death in hazardous industries such as oil and gas, transport, and utilities.
At the same time, businesses are becoming increasingly reliant on their digital platforms. Any successful business has comprehensive understanding of physical or human assets that are critical for it to be both successful and resilient. So why is its digital backbone, which is at least as critical as any other asset, so widely ignored?
Senior leadership tends to operate in a different world from the IT team, yet there is a critical need for improved understanding of business-critical assets, and the dependency that critical business processes have on them, to ensure there is a robust cyber-security risk management framework. A “scatter-gun” approach to protecting everything within an organization leads to a false sense of security. Organizations often underestimate the potential loss from a cyber breach due to overreliance on their IT functions to protect them and overconfidence in their ability to detect cyber attacks early. So, what steps can organizations take to improve this situation?
From Risk to Cyber Resilience
Elsewhere, we have examined how many companies are employing more traditional technology approaches or more audits to address the rise in cyber risk. We have explored the shortcomings of these approaches and the need to integrate both technological and risk management approaches into holistic solutions.
Our focus in this Advisor is on specific issues with the traditional technological approaches used to combat cyber risk and the critical role of culture and leadership in building resilience throughout the organization.
Traditional cyber risk management focuses on “hardening” the perimeter with firewalls or antivirus software to protect assets. However, digital connectivity means that simply building a hard shell around the business is not enough to ensure cyber resilience. Identifying and understanding business-critical assets is essential to protecting them. Organizations must engage with management at all levels across business functions to understand their businesses better. The c-suite must engage as cyber leaders of the organization, developing a business-led — rather than technology-led — approach to managing cyber risk.
Our research shows that while technical barriers reduce the likelihood of threat infiltration, there remains significant chance for threats to exploit an organization’s vulnerabilities. Investing heavily in a hard shell can cost more than it saves through reduced losses from cyber breaches. Focusing digital defenses outside the business perimeter limits the scope to which an organization can detect threats and protect its business-critical assets, as many threats arise from within the business. A more internally driven approach is required.
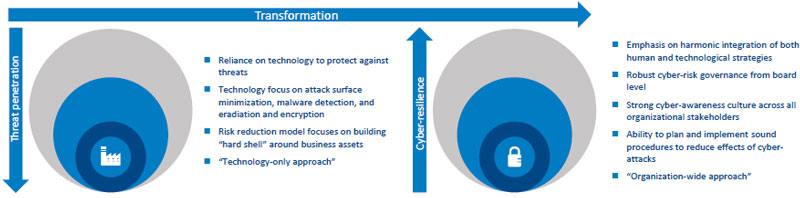
This “cyber resilience” must stem from an organizational response to cyber risk at the c-suite level, and requires stakeholder engagement, recognition of cyber risk as a core risk to all business functions, and the use of both human and technological strategies. We have created a C-Suite Cyber Culture Model, which aims to help the c-suite use a holistic cyber-risk framework for the business. Figure 2 illustrates the model’s transformation from risk to resilience. Resilience is built on, and can be monitored against, in five categories:
-
C-Suite Cyber Culture (CCC) Model — cyber-awareness and culture within the organization that comes from top-level management
-
Vendor cyber security — management of contractors, third-party procurement, and all IoT devices
-
IT management — management of IT applications in general operations and capacity management
-
IT security — both human and technological aspects of cyber-security breaches
-
Data governance — the security and integrity of an organization’s data and information assets
But how does the c-suite know if it is worth transforming into a cyber-resilient organization? Key risk indicators (KRIs) and key performance indicators (KPIs) allow the c-suite to measure performance at the executive level. Evidence suggests that building resilience stems from top-level strategies and governance to provide an organization-wide approach of embedding cyber risk within strategic risk oversight.
Continuous monitoring and improvement are vital for early threat detection and prevention. They enable identification of underlying causes of risk exposure and refinement in selecting appropriate leading KRIs. Organizations must adopt a proactive view to retaining key business knowledge of cyber operations, reviewing and responding to new developments, internally and externally, and always aiming for continuous improvement.
The National Institute of Science and Technology (NIST) Cybersecurity Framework provides a starting point for organizations to benchmark their digital defenses. This should be expanded to determine the total cost of risk (TCoR) using a combination of the NIST framework, scenario modeling and root-cause-and-effect analysis. “Bowtie” analysis, a widely established risk management technique, builds on the NIST framework to provide a more in-depth risk management view, building cyber resilience from within an organization.
Calculating the TCoR in this way, we can develop robust risk mitigation controls aimed at managing the costliest risk scenarios to optimize reduction of financial losses, protect reputation, and improve overall performance. Furthermore, a reliable assessment of the TCoR, supported by an appropriate suite of leading KRI metrics, can be used to demonstrate risk reduction to insurers and verify that insurance premiums truly reflect the residual risk that remains. By adopting a resilience-led approach to cyber risk, organizations can increase asset protection and reduce business losses.