CUTTER BUSINESS TECHNOLOGY JOURNAL VOL. 32, NO. 6

Feng Xu and Xin (Robert) Luo argue that because Industry 4.0 leads to potential new cybersecurity risks to manufacturing and supply networks, cybersecurity management must protect industry assets. The authors examine the issues specific to Industry 4.0, the three conventional essential security requirements, present and discuss the challenges of the security management cycle in Industry 4.0, and offer recommendations for cybersecurity management in Industry 4.0.
With the ever-increasing integration of information technology, services, and advanced manufacturing, we are in the midst of a paradigmatic transformation toward Industry 4.0. Through the diffusion of digitally automated technologies, Industry 4.0 can combine operational technology, such as industrial control systems (ICSs), with information technology to enable smart manufacturing.1 By optimizing the computerization of its predecessor (Industry 3.0), Industry 4.0 triggers a huge number of digital connections between devices and networks. In fact, Forbes estimates that there will be more than 75.4 billion devices connected to the Internet by 2025.2
The concept of Industry 4.0, first coined by Germany Trade & Invest (GTAI) in 2011,3 was considered an evolution of manufacturing that transfers embedded systems to cyber-physical systems (CPSs). To illustrate the concept of Industry 4.0, GTAI invoked two crucial elements of Industry 4.0: the Internet of Things (IoT) and CPSs. Recent research has extended the concept to include other technology, such as wireless sensor networks4 and the cloud.5 While IoT and CPSs are deemed the most important technology components of Industry 4.0, this new wave of technology also relies on IoT device networking6 and data networking.7 These technology components form the foundation of Industry 4.0.
While enhancing digital transformation, Industry 4.0 inevitably ushers in new potential cyberrisks to manufacturing and its associated supply networks. Indeed, 31% of more than 3,600 respondents interviewed for the Cisco 2018 annual cybersecurity study reported that they had experienced cyberattacks affecting their industrial equipment.8 The physical-to-digital-to-physical connection allows participants to access real-time data instantly, but at the same time, possible attackers can gain unparalleled access to the IoT network and disrupt physical devices. Therefore, it becomes imperative to understand how to identify and manage cybersecurity issues in the emerging era of Industry 4.0.
This article attempts to identify the challenges of cybersecurity management in Industry 4.0. We first examine the specific characteristics of security challenges and then discuss the challenges of cybersecurity management in Industry 4.0. Based on these discussions, we present actionable insights that can effectively protect industrial assets.
Cybersecurity Issues in Industry 4.0
The three conventional essential security requirements are confidentiality, integrity, and availability, which present somewhat different issues in the age of Industry 4.0 (see Table 1). The essence of security in Industry 4.0 is to protect the confidentiality, integrity, and availability of two critical assets: industrial control systems and CPSs. The critical element of Industry 4.0 is the IoT, which requires integration and cooperation across these systems. However, security objectives across systems are rarely aligned.9 For example, a control system engineer is not concerned about data loss, but an IT system administrator cares about information assurance. In addition, increasing connectivity leads to greater and farther-reaching risks. Attackers might attack the targeted systems by intruding into the weakest parts of other connected systems.
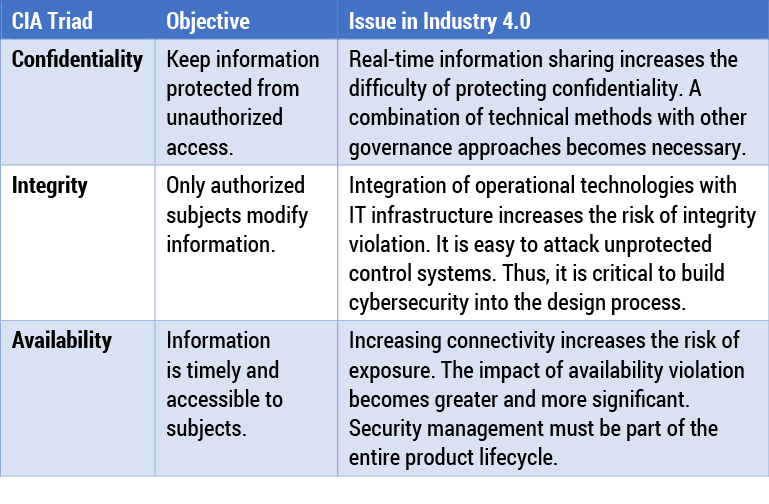
Confidentiality
As manufacturing evolves, it requires real-time information sharing among all participants in the digital supply network. However, information sharing creates significant cyberrisk; balancing confidentiality and data sharing is difficult. The protection of confidentiality becomes more complex and dynamic in Industry 4.0 as the violation of confidentiality might destroy the entire industrial supply chain. Plus, techniques that solely address confidentiality risks are inadequate. They must be combined with other approaches, such as data governance, to ensure the confidentiality of industrial systems.
Integrity
The integrity of industrial systems is easily violated due to tighter integration of operational technologies with the IT infrastructure. It is important to maintain the integrity of the information flow throughout the industrial supply chain. Compared to traditional integrity protection, integrity in Industry 4.0 requires consistency and trustworthiness of both the information flow and the physical components. However, a recent security report found that the physical systems of a third of manufacturers have not been protected.10 Organizations need to adopt advanced risk management to preserve integrity and remain secure.
Availability
The mounting number of network-connected devices leads to a variety of exposure points, which can be targets for attackers. Compared with Industry 3.0, this situation would have a broader and more significant impact on stakeholders, such as customers, producers, or manufacturers, in Industry 4.0. For example, increasing connectivity might cause the entire industrial supply chain to be out of service if components of the chain are attacked. Organizations need to focus more on the availability of a physical process, such as temperature control or energy consumption, and pay attention to the whole product lifecycle.
Cybersecurity Management in Industry 4.0
Cybersecurity incidents lead to huge loss or severe damage to industrial assets. To mitigate cybersecurity threats, it is essential to understand the cycle of information security governance and control: preparation, prevention, detection, response, and learning.11 This information security management cycle provides important guidance to organizations dealing with security incidents. However, in the context of Industry 4.0, these five tasks present different challenges. Table 2 lists the challenges of cybersecurity management.
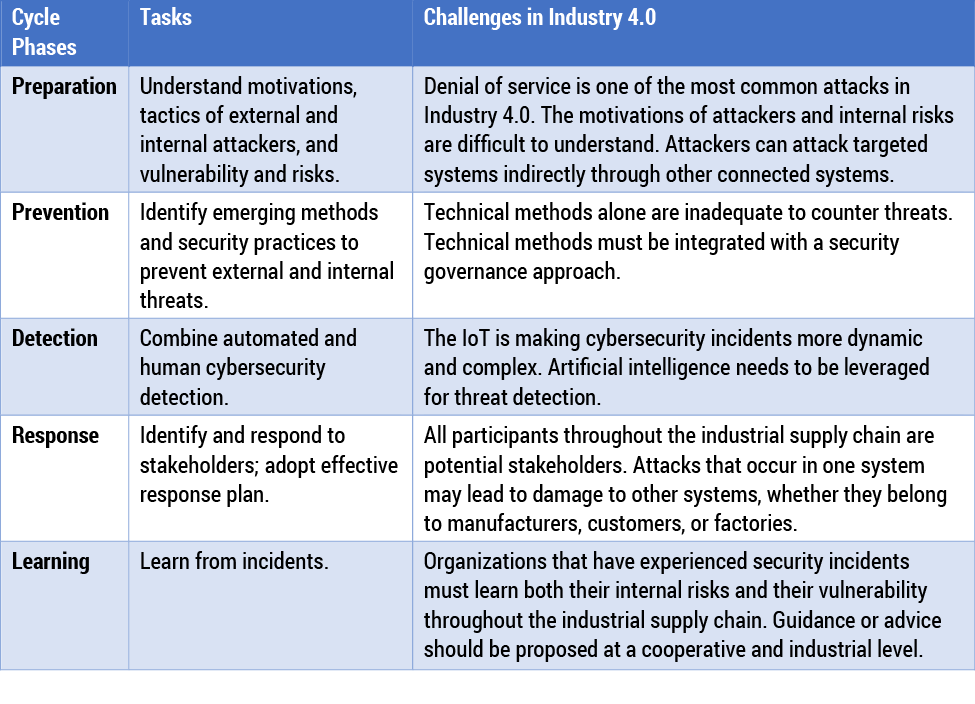
The Security Management Cycle
Preparation
Preparation is the first step in information security management. It emphasizes risk identification and understanding attackers’ motivations. For example, opportunist attackers do not have a specific target and are more likely to attack organizations that have known vulnerabilities. Rogue employees might be emotionally motivated to access sensitive systems or data. Understanding attackers’ motivations can help an organization adopt proper security management mechanisms. The organization might, for example, build response teams, provide checklists, or develop contingency plans. In Industry 4.0, it takes more effort to understand the motivations of attackers, who can successfully attack a target indirectly through the connected systems, making understanding their initial motivations a hard and complex task.
Prevention
The prevention phase aims to identify emerging threats and methods to counter them and to provide security training and education. Due to the rapid evolution of cybersecurity threats, it is critical to identify new methods and tools to prevent threats. In addition, organizations should take efforts to prevent insider security threats, such as providing security countermeasure training. The purpose of prevention is to reduce the occurrence probability of security incidents. In Industry 4.0, the ramifications of insecure IoT devices increase threat occurrence probability. Organizations must not only take measures to prevent threats to themselves; they also need to protect distributed systems. Advanced technical methods alone cannot adequately prevent threats, making an integrated approach necessary.
Detection
With the rapid increase in data volume, information security incident detection requires more automated mechanisms to improve the efficiency of detection. Human cybersecurity detection will be supplementary to automated incident detection, and the combination will maximally protect organizational security. Despite the addition of improved automated incident detection, security threats in Industry 4.0 become more dynamic and complex due to the IoT, making the leveraging of artificial intelligence to detect cybersecurity threats necessary.
Response
Once a security incident is detected, an organization should respond quickly to analyze and deal with it. For example, organizations should hire specialists to analyze security incidents. According to the US Securities and Exchange Commission (SEC), after detection of an incident, organizations must identify and respond to stakeholders.12 In an industrial supply chain, an attack might intrude on one of the weakest systems in order to destroy the entire supply chain. Thus, a concerted effort is necessary in this process because all members of the industrial supply chain may be stakeholders in the attack response.
Learning
Organizations should learn from any incident they experience and must recognize the value of post-incident reviews. They need to compare different incidents, identify their system vulnerabilities, and strategize how to reduce the number and impact of future security incidents. In the context of Industry 4.0, advice and guidance must be provided at an industrial and cooperative level. Organizations need to consider not only their own systems but also those of the entire industrial supply chain.
Recommendations for Cybersecurity Management in Industry 4.0
Based on our discussion and analysis of cybersecurity features in Industry 4.0 and the challenges of cybersecurity management in Industry 4.0, we offer five recommendations for protecting cybersecurity in Industry 4.0.
1. Build a 360-Degree Focus of Information Security Management
In Industry 4.0, connected systems will likely create and expose new cyberchallenges. Due to these connected systems, security threats occurring in any part of the supply chain may lead to a catastrophic loss. Thus, information security management in Industry 4.0 requires a 360-degree orientation. Organizations should focus on a broad range of security issues across the entire industrial supply chain. For example, they need to coordinate and cooperate with all ecosystem constituents, such as suppliers, retailers, and customers. Traditional security management generally focuses on vulnerability, whereas security management in Industry 4.0 should consider the characteristics of interconnections and concern itself with the entire industrial supply chain.
2. Build Cybersecurity into the Design Process
In Industry 4.0, connected objects extend cyberrisks to physical objects. With the IoT, a huge number of physical devices, designed without concern for security, are connected to the Internet. Most of these systems have a low level of security protection, creating a higher likelihood of attack. Cybersecurity should be considered from the beginning to the end of the development lifecycle for IoT devices. It is essential that organizations build security into the design process, assess the effectiveness of security controls, and implement security practices to produce secure devices.
3. Develop an Integrated and Cooperative Approach to Cybersecurity
The cyberrisks of sharing data across the digital supply network increase with Industry 4.0. Cybersecurity now extends beyond the isolated organization. In Industry 4.0, cyberattacks can threaten any interconnected physical system, and an attack occurring in any component of the industrial supply chain will influence the security protection of the entire industrial supply chain. An organization’s focus on threats to internal systems is no longer sufficient to protect security. An integrated and cooperative approach, requiring cooperation across organizations and responsibility to the entire industry and all stakeholders, is now a necessity.
4. Recognize That Insiders Are the Weakest Link
Insiders have become one of the most perilous threats to organizational security. The potential impacts of insider attacks on industrial supply chains are becoming increasingly significant. With IoT-enabled connections, information becomes easily available through remote access mechanisms. Insiders are more likely to be motivated to attack CPSs in order to achieve huge benefits. All participants can access the information that flows throughout an entire industry, creating a huge challenge to control insiders so as to protect industrial assets.
5. Establish Strategic Information Security Governance
Implementing cybersecurity as part of an organization’s strategy is critical to strengthen the new industrial ecosystem. In Industry 4.0, cyberrisks occur due to vulnerabilities in physical devices, insecure transmission of data, embedded application risk, and so forth. It is insufficient to base organizational information security only on siloed technical methods. Establishing strategic information security governance has become an indispensable way to protect an entire industry. This strategic governance considers not only security governance at the organizational board level but also security cooperation at the industrial strategy level. Leaders must recognize opportunities and risks associated with industrial supply chain systems.
Conclusion
This article described cybersecurity issues in Industry 4.0, identified the challenges for cybersecurity management, and presented five strategic recommendations for security protection in Industry 4.0. We believe that a better understanding of cybersecurity requirements will help organizations strengthen their defenses against potential attacks. Organizations should pay more attention to the challenges of cybersecurity management in Industry 4.0 and adopt effective and proper approaches or mechanisms to mitigate cybersecurity risk.
References
1Sniderman, Brenna, Monika Mahto, and Mark Cotteleer. “Industry 4.0 and Manufacturing Ecosystems: Exploring the World of Connected Enterprises.” Deloitte Insights, 22 February 2016.
2Columbus, Louis. “Roundup of Internet of Things Forecasts and Market Estimates, 2016.” Forbes, 27 November 2016.
3Kagermann, Henning, Wolfgang Wahlster, and Johannes Helbig. “Securing the Future of German Manufacturing Industry: Recommendations for Implementing the Strategic Initiative Industry 4.0 — Final Report of the Industrie 4.0 Working Group.” Forschungs Union/acatech: National Academy of Science and Engineering, Federal Ministry of Education and Research (Germany), April 2013.
4See, for example: Gurtov, Andrei, Madhusanka Liyanage, and Dmitry Korzun. “Secure Communication and Data Processing Challenges in the Industrial Internet.” Baltic Journal of Modern Computing, Vol. 4, No. 4, 2016; Xu, Peng, et al. “Lightweight Searchable Public-Key Encryption for Cloud-Assisted Wireless Sensor Networks.” IEEE Transactions on Industrial Informatics, Vol. 14, No. 8, 2018; and Hassanzadeh, Amin, Shimon Modi, and Shaan Mulchandani. “Towards Effective Security Control Assignment in the Industrial Internet of Things.” Proceedings of the IEEE 2nd World Forum on Internet of Things. IEEE, December 2015.
5See, for example: van Lier, Ben. “The Industrial Internet of Things and Cyber Security: An Ecological and Systemic Perspective on Security in Digital Industrial Ecosystems.” Proceedings of the 21st International Conference on System Theory, Control, and Computing. IEEE, 2017; and Urquhart, Lachlan, and Derek McAuley. “Avoiding the Internet of Insecure Industrial Things.” Computer Law & Security Review, Vol. 34, No. 3, 2018.
6van Lier (see 5); and Urquhart and McAuley (see 5).
7See, for example: He, Hongmei, et al. “The Security Challenges in the IoT Enabled Cyber-Physical Systems and Opportunities for Evolutionary Computing & Other Computational Intelligence.” Proceedings of the 2016 IEEE Congress on Evolutionary Computation. IEEE, 2016; Pontarollo, Enzo. “Industry 4.0: A New Approach to Industrial Policy.” L’industria, Vol. 37, No. 3, July 2016; and Daniels, Jeff, Ben Amaba, and Arman Sargolzaei. “Industrial Control System Applications Go Mobile in the Cloud.” Proceedings of the 25th International Association for Management of Technology Conference: Technology — Future Thinking. Curran Associates, Inc., 2017.
8“Cisco 2018 Annual Cybersecurity Report.” Cisco, 2018.
9Thames, Lane, and Dirk Schaefer. “Industry 4.0: An Overview of Key Benefits, Technologies, and Challenges.” In Cybersecurity for Industry 4.0, edited by Lane Thames and Dirk Schaefer. Springer Publishing, 2017.
10Huelsman, Trina, Ed Powers, Sean Peasley, and Ryan Robinson. “Cyber Risk in Advanced Manufacturing.”
Deloitte, 2016.
11McLaughlin, Mark-David, and Janis Gogan. “Challenges and Best Practices in Information Security Management.” MIS Quarterly Executive, Vol. 17, No. 3, 2018.
12Newman, Craig A. “SEC Cyber Briefing: Regulatory Expectations for 2019.” Harvard Law School Forum on Corporate Governance and Financial Regulation, 2 January 2019.




