Assertion
The market momentum behind cloud computing continues to grow. Many organizations will likely move some of their IT operations into the cloud, some at greater risk than others. This movement cannot be stopped, but organizations should head into the cloud with their eyes open. Viewing migration to cloud computing solely as an exercise in cost cutting may blind organizations to other risks.
Syllabus
More people are realizing that enterprise IT assets are more than just hardware and people, and that data assets are more than just numbers. In some cases, data assets are among the most valuable assets in an enterprise. We are on course to increasingly show this data asset value directly on a company's balance sheet, especially since hard assets are being devalued at every turn due to the changing macroenvironment.
As we begin to value data assets more highly, our attitude toward them will change, and the procedural and accounting controls surrounding them will also change. We can all agree that cash is a corporate asset. Corporations are supposed to have stringent rules about who gets to put what cash where and equally strict rules about reporting this activity. Thus, as companies begin to treat data assets more like cash, it is likely that auditors and regulators will demand the same procedures and controls be applied to those data assets as are applied to cash. Placing these assets in the cloud exposes them to levels of risk that would be inconceivable if they were cash.
Certain aspects of cloud technology may be realized without a wholesale migration to the "public" cloud. Private and hybrid cloud architectures are likely to gain popularity as our risk/benefit awareness matures.
Contents
- Opinion by Lou Mazzucchelli
- Partial Concurrence by Lynne Ellyn
- Concurrence by Tim Lister
- Partial Concurrence by Ron Blitstein
- Partial Concurrence by Robert D. Scott
- Partial Dissent by Claude R. Baudoin
OPINION BY LOU MAZZUCCHELLI
Cloud computing has taken its place among the gallery of IT silver bullets that many of us have seen come and go over time. Like those before it, this concept has kernels of truth that have been amplified and distorted by the market to fuel sales of hardware, software, and services. Some intelligent IT consumers will be able to separate the actual benefit from the puffery. However, many IT consumers will move to the cloud in the absence of a clear picture of benefit versus risk. This warms the hearts of those who can't wait to exploit the latter group.
A quick Google query for "cloud computing" yields more than 15 million hits -- the concept is clearly being talked about in cyberspace. However, a query for "cloud computing security" yields about 210,000 hits; one for "could computing privacy" about 43,000 hits; and one for "cloud computing risk" about 56,000 hits. One might think that security, privacy, and risk would be the three most important aspects of any discussion about cloud computing, but apparently not. This raises a red flag for me, as it suggests a huge gap (two orders of magnitude wide) between the cautious and the clueless.
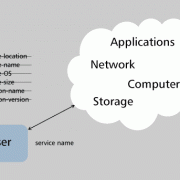
What's all the fuss about cloud computing, anyway? Like many IT concepts, this one can trace its origins back to telephony, where the term "cloud" was used to identify the boundary between user and network domains in a VPN environment -- what happened in the cloud was the carrier's business, not the customer's. Beneficial attributes of that concept have been refined so that today we can talk about a cloud computing architecture as seen in Figure 1.
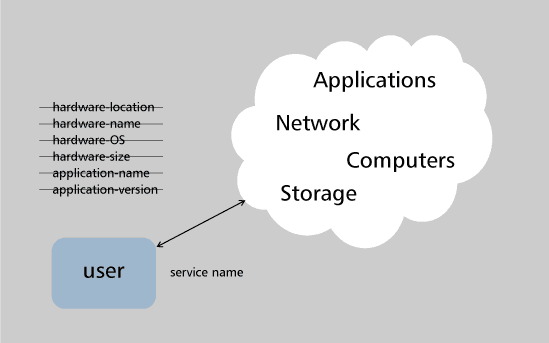
Figure 1 -- Cloud computing: one definition.
In this view, all a user has to know is a service name, without regard to location or implementation details. This concept is congruent with other service-oriented architecture (SOA) concepts but uses the public Internet as its primary interconnection infrastructure. This is cloud computing's strength -- and also its weakness.
Cloud computing vendors like to focus their discussions on three major benefit areas of cloud computing: lower cost, increased capability, and increased agility. This is a siren song to IT organizations facing seemingly constant pressure to cut costs. When we look at the source of cloud computing cost reduction, it can generally be derived from the list in Figure 2.
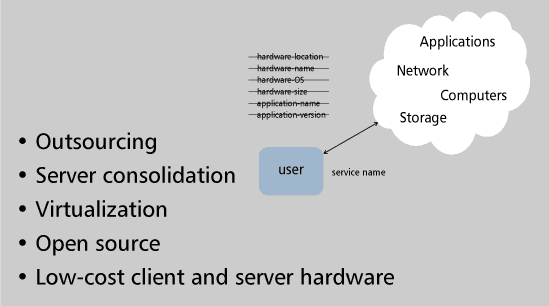
Figure 2 -- Drivers of cloud computing cost reduction.
What's interesting here is that almost all the benefits from the approaches listed in Figure 2 are available without a wholesale migration to the cloud. Wrapping all these into a single product or service offering, however, increases their appeal and evokes a notion of "utility computing," a concept that seems intuitively obvious until its flaws are revealed.
The concept of utility computing springs from the development of public utilities for electricity and water. Companies used to have their own power-generation plants and well or river water sources. As their number grew, it became obvious that spreading the cost of water and power across a larger ratepayer base made economic sense. For these utilities, there was a clear demarcation between producer and consumer.
With telephony, the utility model mutated a bit -- customers shared access to the network but produced the voice (and later, data) traffic on the network -- today, we call this "content." However, all the content processing could be done inside the network, and, initially, had to be done inside the network. In the US, it took a major legal action (the Carterfone decision) to allow processing outside the network. As computers became attached to the network, it was possible to connect a terminal to a remote processing resource; this was called time-sharing. In the time-sharing model, all user data was stored on a host computer, not at the customer premise. This is not utility computing in the same sense as an electric utility -- a consumer does not take delivery of computing cycles that can work on data at the customer site the way watts can power a local device.
As the circuit-switched voice network evolved into the packet-switched Internet, more content moved across the network, and some of the content came to be stored at remote nodes. From an architecture standpoint, the problem of distributed data for Web sites was simple because state was ultimately maintained at the client. However, cookies began the seemingly inexorable march to a distributed state that has now reached fecundity with HTML5 client-side databases -- powerful, to be sure, but also a fruitful terrain for mischief and abuse.
Customers have attempted to shield themselves from some of the seedier aspects of the Internet by employing firewall technology. But many of the cloud offerings I see basically ask the user to move data assets over the firewall onto a server under someone else's protection.
If we realize that an organization's primary IT asset is or will be its data, it is reasonable to ask what sort of protection a cloud provider will offer for these assets. And the answer is ... none.
Much lip service will be paid in the form of service-level agreements (SLAs), but any of the contract language I've seen ultimately disclaims any liability for anything. Credit the lawyers from Amazon with at least a sense of humor when they write in the Amazon EC2 contract:
We strive to keep your data secure, but cannot guarantee that we will be successful at doing so, given the nature of the Internet. (Emphasis mine.)
Which also happens to be the most concise and damning indictment of public cloud computing I have found. I cannot imagine how any agreement to a contract like this would survive the scrutiny of an audit of almost any kind. If the organization attempts to downplay the criticality of the data in question, management has a reason to inquire about why it is being collected in the first place. Data is either useful and valuable, or it's not.
I don't appear to be the only person thinking like this. IBM Gas created a Data Governance Council, which in 2008 suggested:
Data governance will become a regulatory requirement in an increasing number of countries and organizations. In some countries, organizations will have to demonstrate data governance practices to regulators as part of regular audits. This will likely affect the banking and financial services industries first, and will emerge as a growing trend worldwide. 1
Don't let the last sentence think you are off the hook if you are not a bank -- is your customer information in the cloud? Does it contain credit card information? You're probably already a publisher of such information to a wider audience than you think.
The IBM statement also raises the issue of cross-border treatment of data assets: Can your organization predict that your data will not cross a border on its way to a cloud server? Will the data be accessible in any case? Could your organization's access to such data be limited or removed by changes in local law? I would be hesitant to move data assets to the cloud without certainty that my access would be unimpeded -- and that certainty would be very hard to acquire.
Last, consider external conditions; moving to the public cloud assumes that the public cloud will be accessible. This assumption may be challenged in the next two years as we run out of IPv4 address space, and the transition to IPv6 does not go as smoothly as we hope. Or perhaps congestion or saturation will inhibit our unfettered access to our assets in the cloud. Netflix is already responsible for consumption of 20% of peak US Internet bandwidth between 8 and 10 pm, with only 17 million US subscribers. What happens when Netflix, or a competitor, is really successful?
Is there blood to be gotten from this stone?
While I am particularly suspicious of movement to the public cloud en masse, I see several interesting alternatives that can bring organizations the benefit of cloud technologies, while helping to mitigate the risk, as shown in Figure 3. As the figure suggests, there is significant benefit obtainable from a private cloud computing resource that sits on an organization's physical premise or on its VPN. There is then an opportunity to identify the minimum set of data that requires public cloud exposure to fulfill a business requirement and create the smallest possible silo exposed to the public Internet. The result is a hybrid cloud. I believe that such hybrids will become the norm as the risks of public Internet exposure become more widely understood.
Figure 3 -- Cloud computing and outsourcing are orthogonal.
If an organization thinks about cloud computing solely from the perspectives of applications and cost reduction, it may take actions that increase the volatility of its data assets and its liability resulting from their compromise. On the other hand, if that organization considers cloud computing from the perspective of data assets and risk management, the conclusions reached may be very different, but the entire organization is less likely to be disrupted, "given the nature of the Internet."
1"IBM Council Predicts Data Will Become an Asset on the Balance Sheet and Data Governance a Statutory Requirement for Companies Over Next Four Years." Market Wire, 7 July 2008 (www.ubistor.com/company/news/20080707.php).
PARTIAL CONCURRENCE BY LYNNE ELLYN
Lou has written a good piece that does a very credible job of taking some of the puff out of cloud puffery. The cloud is largely marketecture that may be described as outsourced data centers, software as a service (SaaS), virtualization, and retread outsourcing. The most significant and new (relatively new) technology that may be offered as a cloud is virtualization. Any CIO considering virtualization needs to determine whether it makes most sense to virtualize inside the company or to let someone else provide this technology. Like outsourcing, the best cost profile would be the result of aggressively virtualizing inside the corporate data center and then seeking a provider to add value. In many if not most cases, a provider cannot do this at less cost than can be done internally unless its data center is still following the one-application/one-server philosophy. In such a scenario, a provider can do "your mess for less."
For small undercapitalized companies with little to risk, a cloud implementation may be the only affordable alternative. For Fortune 500 companies, cloud services should not come from dubious sources. If you want to host mission-critical resources "in the cloud," stick with reputable vendors, such as IBM and HP. These companies have the ability to either help you virtualize your data center or provide the service on theirs. No sane company would host a mission-critical application on the new cloud arrivals.
CONCURRENCE BY TIM LISTER
Does the Hamburgler lurk in the cloud?
I guess I am completely biased by my views of risk management, but when I read Lou's comments about an organization's data assets, I think about an organization's data liability. You might be thinking that they are just two sides of the same coin. The more valuable the data to you, the greater your liability should that data escape. If this were true, then Lou and I are just looking at the same issue from different perspectives, but it is not true, and we all need to assess both assets and liabilities before we hand data to the cloud.
Lou has done a fine job from the data asset viewpoint, and I want to add to Lou's opinion the need to assess what might be a moderate or small asset for your organization, but a very large liability.
Look at what just happened in mid-December. McDonald's, of cheap burger fame, had its databases hacked with customer names, addresses, date of birth, and so forth, taken. No, the hackers did not get the recipe for the secret sauce or credit card or bank account numbers, but all the same, the FBI has been called in.
My guess is that names and addresses off the Micky D Web site are not pivotal to their billions and billions sold, but this is not good for them.
It turns out that McDonald's subcontracted to the firm Arc Worldwide to do some digital marketing, which in turn sub-subcontracted to an unnamed company that processes and stores e-mail information for Arc.
Now it gets weirder. The unnamed Arc subcontractor was the one that was actually hacked, and guess what? Other Arc clients appeared to go into the french fry-alator with them. The largest one named is Walgreens, the biggest drugstore chain in the US.
I found these bon mots in an online article by Eric Doyle of IT Pro, dated 14 December 2010:
Colin Tankard, managing director of security and encryption specialist Digital Pathways, believes that all personal customer and employee details should be stored in encrypted form....
"This case has highlighted the difficulty with interdependence and it is hard to see how cloud strategies can sensibly ensure that all possible links to the originators' data is secured," he continued. "It really is a due diligence issue for each link in the chain. Each company in the chain should be ensuring that its outsourcing company has robust security."... Tankard said, "At the end of the day, it is now McDonald's who is suffering from the bad publicity not the third-party company. The responsibility always sits with the primary company." 2
Who owns the risk, and now who owns the problem? It's you, the primary company, not the cloud admins; nobody cares about them. The data was given to you, and you blew it. Careful, careful, before anything goes to the cloud.
2Doyle, Eric. "McDonald's Customers' Data Exposed in Hack Attack." SC Magazine, 14 December 2010 (www.securecomputing.net.au/News/241641,mcdonalds-customers-data-exposed-in-hack-attack.aspx).
PARTIAL CONCURRENCE BY RON BLITSTEIN
Lou makes many excellent points in his discussion of the overhyped salvation for modern data processing platforms: cloud computing. In the main, I wholeheartedly agree that this is a case where forewarned is forearmed. Marketers have done an outstanding job of presenting "The Cloud" as if it is the next best thing. However, I am waiting for marketing to reach the levels of true glory: "Cloud Computing: Don't Leave Home Without It"; "Cloud Computing: Just Do it"; or "Cloud Computing: It's the Real Thing." After all, with computing in the cloud, you sleep well at night, can seal the deal, and win the game. In fact, for guys, cloud computing is better than Axe body spray to help you get all the girls you could ever hope to attract.
However, those of us with longer memories will recall the days of computer time-sharing and wonder what all the hubbub is about. The fundamental concept of cloud computing is that the computing is not in a specified, known place, or even repeatedly performed in the same place. Cloud computing customers do not own the physical infrastructure and instead rent usage from a third-party provider. They consume resources as a service and pay only for resources that they use. Sharing perishable and intangible computing power among multiple tenants improves utilization rates for service providers, since servers are not unnecessarily left idle. A side effect of this approach is that, overall, computer usage rises dramatically, as customers do not have to engineer (i.e., understand) for peak load limits.
I guess eliminating the need to understand computing may be the rub for me. Absent a reasonable understanding of computing as a system, people throw iron or bandwidth at problems that could be better solved with more efficient programming. Computing is seen as mysterious and unfathomable for the layperson. This stuff we do is not necessarily easy, but it ain't quantum mechanics either. The fact is that all large-scale organizations should already have virtualized their computing environments. Depending on how one defines a medium-scale business, this should be true for them as well. For a comparatively modest investment, say US $100,000, your "WinTel" processing platforms are now virtualized. You get fewer boxes to maintain, higher uptime, faster provisioning, lower utility costs, and the opportunity to reduce system administration costs. You can certainly pay someone else to do this. My concern is what it says about you as an IT professional. When the costs of running a data center, releasing marketing campaigns, fielding a sales force to sell cloud computing, earning a profit, and paying taxes on income earned sum to a figure that is lower than your costs to run your data center in a responsive and secure manner, then something is wrong on the home front.
Where I part company with Lou is the value that cloud computing can bring to startup companies. For these firms, speed to market and capturing their first dollars of revenue are keys to survival. They will cut corners everywhere they can to avoid high burn rates or lumpy burn rates. Any spending that does not directly link back to getting their product to market or capturing sales will be minimized. Cloud computing may prove to be an essential ingredient that allows startup firms to stretch their available capital, thus improving their chances of achieving first-year sales goals and continued funding.
PARTIAL CONCURRENCE BY ROBERT D. SCOTT
While written with a dramatic flair that at times overstates for effect, I agree with Lou's fundamental point: a move to cloud computing involves significant risk, something that the today's marketing hype machine glosses over. The reality is that once in the cloud, you do not know what is happening to your information assets, much less who is doing it. Cloud hosting is simply not the most secure environment at present. This may be OK for some types of information. But for any mission-critical intellectual property, cloud computing is a risk that must be mitigated. If you're looking to achieve and maintain data privacy requirements for PCI compliance, HIPAA, SOX, e-commerce, and so on, then cloud hosting is not the solution for you.
Another hidden risk is the potential lack of redundancy. One of the misconceptions of cloud hosting is that it's hosted "in the sky and not in a data center," which is not true. Cloud hosting resides in a single data center somewhere. Recently, a large hosting provider's data center went down, shutting down several applications and Web sites. Cloud dwellers had an immediate reality check: single points of failure still exist within a cloud environment.
Then there is cost -- the big motivator for going "cloud" in the first place. Yes, it is true that the cloud gives businesses a hands-free method to scale their application development and hosting solutions. However, problems can arise that are financially surprising. For example, automatic scaling can make people extremely lazy. If you're not paying attention to your usage, you just might get a huge surprise on your next bill.
So should you "go cloud"? The answer is: it depends. If you are a startup with no critical data on your Web site or applications, the security level of cloud hosting may be fine. Small to medium-sized organizations may also benefit from the speed and agility that cloud computing enables. Cloud hosting is extremely fast to implement in most cases and claims to be infinitely scalable (we'll see about this). It also supports multiplatform development environments.
The punch line: ultimately, while cloud hosting may provide some distinct benefits and cost advantages for startups or noncritical Web sites, it isn't well suited for mission-critical sites and SaaS applications. You need to have a clearly defined application and data architecture that will enable you to access the risks versus benefits of cloud computing. Get your architect(s) to work first (you do have one, right?). In most cases, established enterprises will find that if they do anything, it will be a hybrid solution.
PARTIAL DISSENT BY CLAUDE R. BAUDOIN
I totally agree with the assertion that "organizations should head into the cloud with their eyes open." In fact, that was the main point of my seminar "Cloud Computing: Fear, Hype, Reality, and Pragmatics" at the Cutter Summit this past October as well as a recent Executive Update that I wrote around the same time. 3 Lou provides important facts and statistics about the risks inherent in entrusting your valuable data to an outside provider, and these are the reasons that my dissent is only partial; otherwise, his opinion adopts an unfortunate fearmongering tone that is more appropriate to current US politics than to IT research and consulting -- and does not serve the would-be adopters well.
Most significant changes entail benefits and risks, and they are often almost balanced: if the benefits were obviously much greater than the risks, we wouldn't waste much time discussing them. In those balanced situations, exaggerating the risks and minimizing the benefits completely change the conclusion, and that's where I wholeheartedly disagree with Lou.
It is true that most CEOs and CFOs -- and not a few CIOs -- see cloud computing primarily as a cost-reduction measure, but there are additional benefits, too:
-
Because of the large number of customers they have, cloud providers are more likely to put in place disaster recovery and security mechanisms that a single client would find prohibitively expensive.
-
Procuring a cloud-based resource (whether it is a database, an application, or hardware) is quicker than the procurement and delivery cycle of a purchased resource.
-
The shift from capital expenditures (CAPEX) to operational expenses (OPEX) makes it easier to justify and manage the cost -- and is one of the contributing factors to procurement cycle reduction, and to IT agility in general.
Lou argues that your data will be less secure in the custody of a cloud provider than on your own premises. This argument has appeal because we all like the things we love to be close to us, but it quickly breaks down: my money is not under my mattress; it is at the bank. Granted, banks have a longer history and have service agreements that are more stringent than the Amazon EC2 contract; my deposits are also insured by the government, up to a limit. But in the end, most of us decide that our money is safer at the bank than at home, where a single robbery or fire would erase our holdings. The same applies to your data: if your data center goes up in smoke and your disaster recovery plans were faulty, or if a competitor does "dumpster diving" and retrieves unerased disks, or if a disgruntled employee copies your next product design files onto a DVD and sells it to the competition, the purported safety of holding your data at home vanishes. My final point about security is that cloud computing is no better or worse than plain-old outsourcing -- and outsourcing is alive and well, thank you.
Data residency is a clear issue, as I have pointed out in my Summit seminar and Update. The previously quoted statement from the IBM Data Governance Council is important, but it makes the point that data is valuable and must be governed -- not that it cannot be in the cloud. Your approach, if this issue applies to you, should be to constrain the locations where your data can physically reside.
The argument about the dwindling number of available IPv4 addresses, and the potential difficulty of the transition to IPv6, leaves me about as unmoved as the Mayan calendar's end in 2012. People have predicted the collapse of the Internet before, and it didn't happen. There are enough economic actors whose business model totally depends on the Internet (ISPs, Netflix, Google, Amazon, Facebook, and an entire industry that cannot be named here because this is a family program) to ensure that the money will be spent to smooth the transition and/or put other temporary measures in place until IPv6 succeeds.
One of Lou's conclusions is that the cloud model may work -- as long as you deploy a private or hybrid cloud. I agree that a large enterprise can deploy a private cloud, though I question the economics of providing fast-enough, site-to-site connections to be able to use a central resource from remote sites (depending on the application, of course). It is much simpler to provide independent Internet access through various local ISPs, allowing each site to access a public cloud provider. But when it comes to small and medium-sized enterprises, the proposition falls apart. To engineer a private cloud, an organization has to own enough resources to handle peak demand -- precisely denying it the economies of scale that a utility service provides. If a small company buys a bunch of servers and virtualizes them in order to be able to shift workloads around, I claim that this is not really a private cloud; this is virtualization, a concept that is related but not equivalent.
If you go to the movies, but you're worried about your safety, there are a few things you can do: you can sit close to the aisle, and you can look at where the closest emergency exits are before the lights go down. But you don't address the crowd and yell, "Do you realize that if this theater caught fire, we'd all be dead?" We can't just move from the hype stage to the fear stage and stay frozen there. We have to go on, rationally, to a realistic assessment and pragmatic advice to leverage the cloud model whenever it makes sense.
3Baudoin, Claude R. "Cloud Computing: Both Less and More Than You May Think." Cutter Consortium Sourcing & Vendor Relationships Executive Update, Vol. 11, No. 11, 2010.