Once again, the end of the year has snuck up! That means it’s time for our annual Cutter Predicts … series. Below, Cutter Fellows and Senior Consultants showcase their visions of 2014 (and in some cases, beyond).
All Gov’t Levels to Search for Cost-Effective Operational Stability
by Mark Peterson
This coming year, government leaders will be looking for the most cost-effective means of operational stability for their level of government.
Public sector executive leaders will take specific steps to assess their organization (both operations and information technology) to determine the most cost-effective means for business operations. For the IT organizations, this means taking a detailed look at the utilization of operational disciplines, governance and business alignment methods. In addition, decisions will have to be made regarding human capital replacement, training and/or selectively sourcing required technology operations and functions.
At the same time, executive leaders will be faced with making decisions on modernization of systems and productivity applications. Progressive executive leaders will utilize an unbiased and trusted advisory firm to help them transition to a new business model of technology support rather than depending on a vendor strategy, which is usually based on selling product or software. Overall cost of 0perations will drive critical decisions for public sector leaders.
IT to Secure its Role in Selecting/Implementing Cloud Solutions
by Jeffrey M. Kaplan
Here’s what I see coming in the new year:
- Enlightened CIOs will regain a key role in the acquisition and implementation of enterprise Cloud solutions, including Software-as-a-Service (SaaS) applications and Infrastructure-as-a-Service (IaaS) computing resources. They will not only put policies in place that will encourage end-users and business units to include IT in the procurement and deployment processes, but will also enable IT to play a more proactive role in the evaluation and selection process.
- Corporate end-users and business units will be forced to enlist greater IT involvement and support in the acquisition and implementation of enterprise Cloud solutions because they will face greater challenges integrating them into their existing systems, software and data sources, and ensuring their security and performance.
- IT professionals will become more receptive to acquiring Cloud-based IT management solutions that enable them to more easily and economically perform their day-to-day duties so they can dedicate more time to strategic corporate initiatives.
- As the adoption of Cloud-based applications and computing resources becomes more mainstream, the focus will shift from generic horizontal applications and services to industry-specific solutions aimed at satisfying the needs of particular vertical markets and business processes.
- Government surveillance, such as the NSA activity, will drive greater demand for private, dedicated deployments of Cloud services at the SaaS, IaaS and Platform-as-a-Service (PaaS) levels. The advent of private clouds will give enterprises more choice, generate greater confusion and create more integration challenges.
Will the Laggards Speed Up, Please?
by Claude Baudoin
The Oil and Gas (O&G) industry, especially its so-called “upstream” segment, exploration and production (or going from the rock to the pipeline), is totally based on data. A seismic survey may collect petabytes of acoustic signals. Increasingly, when wells are drilled, sensors are inserted in them, and these sensors collect data for the next 30 years of production. Two completely different applications, but in both cases they result in masses of data. O&G’s dependency on data began decades ago when the Schlumberger brothers invented the “electric log” in 1926. And yet, this sector has been one of the most conservative, even lagging, adopters of modern modeling and management techniques for both information and processes.
Over the next several years – but it may take until 2020 – we will see this change. It will not result from a sudden waking up of O&G executives, who typically have no IT background and do not consider their top IT person to be a peer in the C-suite. It will instead result from a combination of forces that give them no choice:
- Some problems are getting too big for a single company to solve. Integrated and more secure processes, both inside and across companies, will just not be possible without ways to exchange information that has solid semantic underpinning (ontologies, metadata models, etc.).
- Regulators will demand certain reports on risk and mitigation procedures, as they are doing in the finance industry, among others. They won’t be able to accept and process the information if it is in plain English, or if each company delivers it in a different proprietary format.
The only solution will be to adopt standards such as the Business Process Model and Notation (BPMN), Decision Modeling Notation (DMN), XML Metadata Interchange (XMI), and others. If you are in the O&G industry, start learning about these standards, develop some business cases, and begin developing some models, even if it is just intially for intra-company sharing.
Analytics “Late-Comers” will Gain New Prominence
by Rick Harris
We’ve come to expect breakthroughs from retail, social and financial institutions as they apply leading-edge analytics to deliver impressive business insights. Heavy industries such as utilities, energy exploration and transportation have lagged these analytics power-users in three key dimensions: enterprise culture, technology foundation and business results. I believe 2014 will be the year when these analytics “late-comers” will gain new prominence. Here are six predications on what to expect:
Enterprise Culture: new beliefs and norms are necessary to embrace analytics within most enterprises
1. Analytics will be formalized as a leadership competency. Most large organizations have a set of leadership competencies that reflect their vision and strategy. In 2014, being able to drive decision making with analytics will become a key competency for leaders.
2. Everyday analytics will remain elusive. Translating the notion of analytics into routine action won’t become second nature in 2014. This is a classic process and change management challenge – it typically takes 2-3 years for an organization to make this journey.
Technology Foundation: advanced analytics requires adoption of rapidly evolving technology and new process disciplines related to information, integration, infrastructure, applications and visualization
3. Analytics start-ups will be viable. Driven by big investments from large enterprise and new ventures, every element of the analytics technology stack is evolving rapidly. Small, new companies will compete successfully with large, established suppliers in 2014. Analytics late-comers will appreciate the innovation, agility and focus on specific market segments that the leading start-ups provide. Don’t count out the large, established suppliers as some will leverage and integrate their broad offerings to deliver compelling results.
4. Undisciplined information governance will hinder progress. Most organizations struggle with traditional enterprise data management (data stewardship, master data management, integration…). Advanced analytics will require a broader and scaled-up approach to data management in addition to analytics management (data preparation, models…). Progress will be slow in 2014.
Business Results: translating information into business value requires new approaches and skills
5. Waterfall approach to analytics will disappoint. Analytics initiatives benefit from an agile and experimental approach to work. Traditional portfolio planning and waterfall development approaches will diminish results; this will prove to be a hard habit to break in 2014.
6. Initial analytics initiatives will be modest. Late-comers will enhance their existing operations or products in 2014 with simplistic, early ventures into analytics. Early wins will rarely be examples of highly sophisticated analytics, and don’t need to be.
The relevance of analytics is accelerating for every business. The tremendous potential for business results will make analytics an imperative. I’m looking forward to seeing progress from the late-comers in 2014.
IoT, Big Data, Mobile Apps, Drones to Impact Privacy & Security
by Rebecca Herold
Here are my predictions for 2014:
- 2014 will bring exponential expansion and evolution of the Internet of Things (IoT).
This will also bring new opportunities for information security trailblazers unlike any we’ve seen before. The potential benefits of the IoT will be huge, but just as large will be the new and constantly evolving information security and privacy risks. We will see some significant privacy breaches resulting from the use of IoT devices as a result. New IoT risks, and resulting security incidents and privacy breaches, will bring a significant need for technology information security pros to also understand privacy concepts so they can implement privacy protections within all these new devices, and into the processes and environments where the devices are used. Even though basic information security and privacy concepts will still apply, very little has been done to actually implement security or privacy controls in these new technologies. We will need more information security and privacy professionals who can recognize new information security and privacy risks. There is no textbook to look to for these answers as risks evolve.
- The increased power of Big Data analytics will redefine what it means to anonymize and de-identify data.
Long-used methods will no longer be effective because of Big Data analytics abilities to make correlations between disparate pieces of data to reveal intimate personal details that, up until recently, there were not any algorithms that could produce any correlations at all. The use of Big Data will proliferate dramatically in 2014, with little to no consideration of the related information security or privacy issues, especially by those using Big Data for new types of marketing, research, and for new types of services. Information security professionals who are not afraid to be trailblazers will need to be able to identify privacy risks associated with Big Data analytics, and be able to then create effective information security controls. Great opportunities exist for those willing to step out of their comfort zone and take chances to create security controls that, to date, have not existed.
- 2014 will provide us with some significant new privacy breaches through new and quickly wildly popular apps.
Mobile apps continue to be used more widely. They will also continue to be used without having any meaningful security controls built in, and with little to no regard to privacy issues. “Hey, there’s no law against it so there must not be any privacy concerns!” I’ve heard that sentiment hundreds of times from enthusiastic marketers and developers. Guess what: privacy and information security laws are primarily reactionary and largely don’t get passed unless a significant number of breaches and harms have already occurred, and if they don’t significantly thwart the plans of the lawmakers’ large donors.
- 2014 will see dramatic expansion of drone use, and significantly more discussion by lawmakers. Not to mention the privacy invasions that will occur.
I’m already seeing significant numbers of journalism schools at universities investing in purchasing their own drones so they can get to places they’ve never been able to get to before to get photos and audio for news reports and investigative stories. The problem is, most of those locations are on private property. But there are currently no laws regulating the use of drones, so the drones will boldly go where no humans have been able, or allowed, to go before. Also, consider that Amazon (and now probably other retailers) is considering the use of drones for package delivery. They will not only deliver packages, but you can bet they will also collect data about everything encountered throughout their journeys. Police are using drones; insurance companies and a large cadre of other industries want to use them. There are safety, security, and privacy issues to address with all these envisioned uses. But from what I’ve read from these groups’ public descriptions of their wants and plans, they haven’t even considered the privacy issues. Some members of congress are concerned, though. In November, Sen. Ed Markey filed a bill to require the Federal Aviation Administration to establish privacy requirements for allowing drones to be flown in commercial airspace.
- Something significant is going to be happening with 3D Printers in 2014, beyond the creation of plastic guns and the associated safety concerns. It’s been gnawing at the back of my brain that there are going to be some information security and privacy issues. I’ve just not yet been able to bring those issues into focus sharp enough to articulate clearly.
I could go on. But this is probably a long enough list for now. What are your thoughts on these topics? I look forward to reading your comments.
Securing Internet Traffic
by Claude Baudoin
By the end of 2014 or the beginning of 2015, various large cloud providers as well as the Internet Engineering Task Force (IETF) will have developed mechanisms to protect most Internet traffic against the pervasive domestic spying performed by the U.S. National Security Agency. The NSA won’t be unable to decrypt the traffic it really cares a lot about, but it will just take too much computer time to decrypt all traffic, as it can do right now.
I predict this because there is a great convergence happening. First, the NSA’s antics have finally made companies aware of the security issues involved in taking client-server traffic that used to be inside the firewall and moving it to the Internet in order to access a cloud-based system. Secondly, the IETF is expecting to release the HTTP 2.0 protocol by the end of 2014, at which point it will be possible to encrypt Web traffic by default. Thirdly, large cloud providers such as Google and Microsoft will not be able to convince major clients to move to the cloud unless the data is protected in transit.
The irony, at least for the NSA, is that while the NSA’s powers will probably end up being curbed through legislative action, its technical capability will also be curtailed through these moves. By 2015, the Internet will be more secure… and regardless of what we may otherwise think about him, we’ll have Edward Snowden to thank for it!
Cloud customers should already be asking their suppliers what measures they offer to protect the traffic. The urgency just got greater.
Workforce Challenges
by Carl Pritchard
With the work force continuing its shrinkage, there’s going to be serious influence purveyed by the “do more with less” crowd. Entrepreneurs who can find ways to leverage smaller and smaller staffs will be seen as the prophets in the year ahead, with an ability to make businesses (and whole industry sectors) thrive with what once would have been considered bare-bones staff. This is bad news for the underskilled, as they will find fewer and fewer positions available to take advantage of their trainable strengths.
Some of the smart executives will find ways to control their work force challenges (and the increased disparity between the very well-paid highly-skilled crowd and their less-skilled counterparts) by looking for the “diamonds in the rough,” and earning their loyalty through extensive training and opportunities for growth. Expect more than one story from the IT community where someone who is hired for something completely unrelated to the technical side of the business finds their way into the pantheon of top performers on the tech side of the house.
Oh, and yes, we’ll have flying cars…
Software Defined Networking (SDN) gets the attention of the CIO
by Jerry Grochow
Today’s Internet is a product of over forty years development, beginning with the ARPANET in the late 1960s and the formulation of the TCP/IP protocol in the early 1970s. We are now poised for the next major change in Internet development with the introduction of Software Defined Networking (SDN) – network architecture (hardware and software) that allows creation of “virtual internets” using potentially new protocols, running over the fiber optics and other hardware of today’s Internet. The National Science Foundation began funding university research in SDN under the GENI Project Office and moved to large scale prototyping in 2009. The Open Networking Foundation has been formed by all the big players in networking technology to further develop open standards (OpenFlow) and help brings these opportunities to the mainstream. All your next routers are going to be speaking OpenFlow in 2014!
Lean, Devops and the Resurgence of the Industrialization of Software
by Murray Cantor
One the constant tensions in our industry is the business need to make software more like manufacturing — highly predictable and controllable — and the reality that much of the software development lifecycle is not amenable to the process control techniques that are so effective in manufacturing. Software development is different than manufacturing in that:
- There is a wide range of uncertainty. Software efforts span from green field projects with little initial understanding of the needed system to bug fixes and small changes with very detailed specifications.
- There is an indirect relationship between the effort expended and value created. Generally, if one spends 10 hours painting a wall, one can expect there will a lot of wall painted. One can spend 10 days doing requirements analysis on a green field project, and who knows if any value has been added.
We saw the rise and fall (?) of the software factory movement over the last few years. The movement’s failures may be traced to a lack of accounting for the above differences. Maybe though, with the emergence of devops and continuous delivery, the software factory (which arguably is a mashup of factories and agile that is generally applied to deployed software).is only in remission.
Most organizations that see themselves as ‘Agile’ do in fact commit to the business to deliver desired content on a schedule and with high productivity. While striving to meet these commitments, these teams find using stories, scrums, sprints, work items, etc. do improve their ability to delivery. But even with the success of agile methods, there will be continued pressure on productivity of software development, especially on the cost of labor for most enterprises that rely on building software. For these organizations, labor arbitrage is only a partial answer. They need the teams to be more productive.
Even though factory methods have limited utility in software, the lean practices of identifying and eliminating waste can apply across the whole range of development efforts. So while industrialization will gain momentum, it won’t be in building software factories, but in making the software development supply chain (internal and external) more efficient by adapting techniques learned from manufacturing, such as Kanban and Value Stream Maps (VSM).
While this trend is already well underway, it will accelerate in 2014. In particular, as in manufacturing, effective implementation of VSM relies on instrumentation to collect operational measures. The next phase of industrialization will entail greater adoption of, and eventual standardization of, these measures.
Which MDM?
by Jim Love
In 2014, a number of vendors will emphasize Multi Database Management (MDM) tools in the cloud. Through the magic of marketing, we will somehow deal with the conflicting acronym generated as a result (Mobile Device Management). These tools will be available as Software as a Service and will create virtual databases to serve cloud-based BI. The value proposition will be the “democratization” of Big Data.
Collaboration and Social Tools in 2014
by David Coleman
For 2014, I predict …
1. The browser becomes the OS. More and more is being added to Google’s Chrome browser; so much so that it is starting to look much like an operating system. You have all of these plug-ins (like applications), you can customize and configure your device or the look and feel of the browser. Nowhere is Chrome more an OS than with Chromebooks, where it is the OS. And it is a very web-oriented OS (thin client), with just the browser, media player and file manager as its only native applications. The question is: will IE or Firefox follow suit? Or are they pursuing different directions?
2. The social enterprise. As a result of there being more and better tools available for the social enterprise, I see more people moving off SharePoint or other large collaborative infrastructure systems, and moving to the more agile and less expensive SaaS offerings (of which there are plenty) like Box, PBWorks, SocialBridge, Wrike, Moxie, Huddle, HyperOffice, Zoho Work, Teambox, Google Apps, BaseCamp, etc. It is a good thing that there are easier tools, since I am not so sure that many organizations’ management understand the value of social tools in the enterprise. We did a study this spring that told us that 60% of management understands social in the enterprise… but we don’t believe it. Management may know what some social tools are, but they don’t know where they will get the most leverage, or even if a particular tool is good for their organization. Although a McKinsey report says that 70% of organizations are now using social, only 3% are getting a big benefit from the technology. I believe this will start to change rapidly in 2014 as more Millenials achieve management positions, or as current managers gets the training they need to make good decisions around these tools.
3. WebRTC will be more Prevalent. Although not yet ratified as a standard, WebRTC has the advantage of running in a browser and not requiring any download for audio or video conferencing. Unfortunately there is not yet a mechanism for screen sharing, but since Google put the original code into Open Source, WebRTC is evolving quickly. There are a number of new tools already using WebRTC: Kollaborate.io, Collaborate.com, Bistri.me and many of the major vendors like Cisco, Google (who started it all), and Citrix (Podio) are looking at incorporating this emerging standard into their tools, although they are mainly used as a backup offering to Flash or VoIP. (However, there are SIP to WebRTC solutions like Plivo and webrtc2sip.org/.) In spite of all this hoo ha over Web RTC, neither Microsoft nor Apple are yet in the mix. I believe that in 2014, not only will WebRTC become more common, but both Microsoft and Apple will also jump in with their implementations, possibly causing developers to look at three different implementations rather than just one.
4.Changing HR Landscape. Not many years ago, HR was just considered to be a place to help with onboarding and getting all the forms filled out. Today, with tools like Workday, things are quite different. HR has a more strategic role to play, and in at least 50% of companies, it is getting more budget for tech. The war for talent is driving a lot of innovation. Start-ups such as Entelo and TalentBin have figured out ways (through big data) to determine which employees you can poach before they even know that they wanted a new job. Other new HR tools help with everything from video applicant screening to automating benefits, and worker task optimization. Tools including PeopleMatter, Proven.com, Wozer.com, HireVue, Zenefits, ClearFit, WorkableHR, CollabWorks, Simpler and TalentSoft are changing HR forever by making previoulsy ineffective processes more effective, allowing HR professionals to spend more time on strategy.
2014: The Failure of Agile Software Development is Taken Seriously
by Hubert Smits
What happened in the past: Agile is all the hype in Software Development and the talk at the golf courses across the country. Consultancy and certification are booming and rumor has it that all software development projects will now end as a success: faster, cheaper, better.
What is really going on: More and more software developers are realizing that agile is being implemented as a hype. Processes become iterative. Documents are replaced by tools that maintain a backlog. Customers are still at a far distance from teams. People are still called resources. Cheap labor is still used to “reduce costs”.
A few honest managers are aware that nothing is really changing. Quality is not improving, delivery times are not shortening, turnover of staff is not reducing. The process gets all the attention, teams are moved to an iterative delivery cycle, new practices (pair programming, test driven development) are embraced. The result is that we now deliver the wrong features faster.
What should leaders do: Agile software development has two pillars, iterative and incremental, and the four values from the Manifesto. Leaders have to pay attention to both pillars and have to implement these pillars in the right groups. Iterative is less important for the development teams. Iterative starts with the leaders themselves: don’t initiate large initiatives, initiate multiple small ones.
Iterative is for product managers: creating a stream of changes, not projects. Only then does the development team get involved in the agile transitioning — not with process, but with the first value from the agile manifesto: people and interactions over process and tools. Give the development people all freedom and all support to handle the stream of changes that leaders and managers produce. The stream of changes will create the process change in the development organization that fits the change best. Maybe Scrum, maybe XP, maybe Kanban.
Let it happen, don’t prescribe. Motivate, lead, hire the best. Then let the best be their best.
Stealth Enterprise Architecture!
by Roger Evernden
This year I’m predicting more stealth enterprise architecture! I’d like to say that I invented this phrase, but I’ve found at least two previous uses: one in a comment by Peter Parslow in 2010; the other from Alec Blair, the head of Enterprise Architecture for Alberta Health Services, who described the journey of how his team has used stealth Enterprise Architecture to move AHS to operate more consistently like one organization.
Now, Enterprise Architects have always had to play the political game and use stealth to sell their EA visions. Tricking decision makers into taking small steps that in combination cause longer-term transformation has long been part of the art of EA. At an Enterprise Architecture Conference and Exhibition in Washington, D.C. in 2006, Darren Ash talked about offering quick, immediate fixes, rather than promising future benefits from a mature enterprise architecture, as the best way to sell it!
But what I’m predicting for 2014 is something different. What I’ve noticed is that there are several examples where organizations have been forced into using EA techniques, almost without realizing that they are using EA! For example, individual government departments are required to share data across borders with other departments, and the most practical way to do this is to adopt common architectures. What is happening is that pragmatic necessity is forcing companies to adopt EA practice to solve immediate concerns. But in adopting EA techniques, these organizations are putting in place structures that make a good EA foundation for the future. Enterprise Architecture by stealth!
So maybe we need to combine the political savvy that architects have always needed with recognition that there is often an emerging architecture that we weren’t necessarily planning or even expecting. 2014 could be a year in which some of our architectural goals are met by stealth — through the serendipity of individual EA outcomes within a broad eco-system that build and merge by chance into a coherent and well-architected whole! It could be just fanciful thinking, but then again, it might already be taking place — that’s the nature of stealth!
Things That Go Bump in the Night
by Claude Baudoin
By the end of the decade, self-driving cars will be on the roads in many developed countries. The electric grid will tell our heaters when it is more economical to run, “learning thermostats” will be in many homes, and we will track the movements of people, pets, packages, and many other things. By some estimates, the number of devices connected to this “Internet of Things” (IoT) will pass the number of connected human users by 2016.
The question is: will serious accidents be necessary before people take the risks seriously and harden this infrastructure?
Because the IoT senses and controls physical objects, serious harm can happen — either accidentally or intentionally. We need devices to be authenticated. They in turn need to authenticate the control systems from which they receive commands, and man-in-the-middle attacks need to be prevented – and that’s without exploring the infinite possibilities for industrial spying based on monitoring the signals that traverse this network.
If you make or use Internet-connected devices, you should already be thinking about the identification and authentication of individual devices and control systems, and about the end-to-end encryption of signals and commands. Otherwise, things will go bump (or “boom”) in the night and it won’t be very funny.
We Will Forget the ACA Web Site Fiasco
by Claude Baudoin on Dec 7, 2013
In a few months, the Affordable Care Act enrollment system will finally be working well, millions of people will have enrolled, and the debate will return to the basic policy and political question of whether the whole program is good for the U.S. or not. By 2015, the IT profession as a whole, government procurement services, and the contractors will forget the lessons of the October-November fiasco and will largely or completely return to the same practices as before: unrealistic deadlines, lack of testing, big waterfall lifecycle models, tell-me-what-I-want-to-hear practices, etc.
Why am I being so pessimistic? Because we’ve been here before. The Y2K effort consumed a lot of resources, and contrary to many people, I don’t believe it was in vain. But look at how many Web sites today still require dates in “mm/dd/yy” format, not “mm/dd/yyyy”! Or look at the 2008 financial crisis, which resulted in regulations for the reporting of financial risk information according to a standard that the government still hasn’t defined. Or at whether real changes have occurred in the deep sea drilling business after the Macondo accident?
Companies are shortsighted because they work toward their next quarterly results. Governments are shortsighted because they work toward the next election. Do yourself a favor and look at your system architecture issues, your development lifecycles, your quality assurance practices, and your IT-business communication with a view toward long-term improvements. And it wouldn’t be a bad idea to start with a “technical debt” assessment.
A Focus on Organizations and Value Chains
by Jens Coldewey
If there was one major development in the Agile field in the last year or two, it’s been a shift of focus from teams and methodologies to organizations and value chains. I expect this development to gain more speed and depth in the next three years — becoming the major issue of the debate.
I see three main threads within the focus on organizations and value chains emerging. These seem to address different needs and markets.
The first thread is a tendency to “blueprint” an organization in order to facilitate Agile’s introduction. The “Scaling Agile Framework” belongs, in my opinion, in this group, as do the initiatives of the PMI. Despite a heated debate about whether it is a good idea to blueprint an agile organization, this thread seems to address a growing demand in the market, especially with “early majority” organizations. No matter what position you take, I think it is mandatory to follow this discussion closely and develop an informed and differentiated position yourself.
The second thread looks beyond the realm of Agile as it is understood in the software community, and reaches out to “co-evolution” approaches, such as Beyond Budgeting, Human Systems Dynamics or modern HR approaches. Over the last 10 years (some argue, even longer), Agile has successfully connected to the ideas of Lean; it will surely profit from connecting to compatible ideas of other business movements. Though these connections are not mainstream yet, you may want to actively participate in making them so, or just observe what’s going on here, depending on how innovative and adventurous you are with respect to Agile. In any case, these connections offer opportunities to gain additional insight about the nature of Agile.
The third thread searches for new approaches to leadership and thus, organizational structures that breathe the values of agile. “Servant Leadership” may sound nice (at least if you’re not a manager yourself), but gives little advice on what it means to take over leadership in an agile organization. I also disagree with a widespread notion (among non-managers) that self-organization and leadership are two conflicting concepts. Rather, I think that this notion comes from a limited idea of leadership as “heroic leadership”. What we need is to develop what the Orginzational Development community calls a “post-heroic leadership style”. This effects all parts of the organization, in particular: hierarchies, career support, leader selection, and so on. As an Agile community, we don’t have a coherent idea of how that might look, although some lighthouse organizations exist. I expect this debate to heat up and I recommend participating to learn more about what leadership in the 21st century — in times and domains in which Tayloristic management ideas have become outdated — means.
BYOD Will Become Mandatory In Order to Keep an Eye on You
by Robert Charette
For 2014, I see an increasing convergence of two trends that may not overjoy many of us.
The first is that bring-your-own-device (BYOD ) to work will be increasingly embraced by employers as well as other organizations, such as schools and universities. Earlier this year, it was predicted that half of all companies will mandate BYODs as a condition of employment by 2017. While I think that is an aggressive target, given not only the security issues involved, but the application/data/OS integration issues as well as the rapidity of device turnover, it is a trend that is already taking hold. Companies such as Cisco and VMWare have mandated BYOD, and universities (and now high schools) are increasingly doing the same. And while employers usually have some sort of device reimbursement plan, I can see that going away in the future as well.
The second trend has been the ever increasing demand by employers to access personal information on employees to check up on their productivity, health, etc., and even their off-duty activities. It is estimated that over two-thirds of employees already electronically keep track of their employees. What better way to get continuous, real-time access to what an employee is up to than via a mandated BYOD paid for by the employee themselves?
Now imagine coupling that information with predictive analytics. Are you unhappy at work and thinking about leaving your job for another employer? Your current employer may be able to determine that before you do, decide that you pose a future corporate “intellectual property risk,” and thus eliminate your job, after wiping all of your information from your BYOD of course. (That’s something that companies who mandate BYODs already claim they have a right to do.)
Back in 2007, Donald Kerr, principal deputy director of national intelligence stated that Americans needed to drop their outdated notion of privacy. Privacy no longer can mean anonymity, he argued. Instead, Kerr contended, it should mean that government and businesses properly safeguard people’s private communications and financial information.
Unfortunately, I think Kerr is entirely correct, especially when you consider BYODs and employers’ ever increasing employee-life voyeurism. For future employees, a key decision in deciding who to work for will be how businesses make use of and safeguard their personal information, especially after they leave, since the notion of “personal privacy” is rapidly becoming passé.
My List
by Gil Broza
In 2014…
- People will still call other people “resources.” Even to their face.
- Nominally Agile organizations will continue to administer performance appraisal schemes that emphasize the individual and downplay the team.
- Companies will continue to not train their developers in Agile engineering, because technical execution skills will remain off the radar.
- Technology managers and stakeholders will still assume that their teams ought to develop quality products faster than is realistically possible.
- Project managers will still struggle to come up with a good measure of Agile team productivity for their executives, and consultants will continue telling those project managers that they shouldn’t be measuring productivity.
- Bad meetings — and complaining about the number of meetings in Agile — will remain the norm.
- Cubicles and other sensory-deprivation cells will still dot offices — but there will be fewer of them.
- Female programmers and architects will still be unheard of in many organizations.
- Consultants will continue arguing over the merits of various methodologies and frameworks, while practitioners — getting more and more confused — will just do whatever their organization will tolerate.
- And … people like me will remain hopeful and driven to change all that!
Defined vs Ready Technology Adoption — The Future is Now (and Forever)
by Stephen Andriole
In the 20th century, companies waited until their industries and competitors fully vetted technologies before investing in even the most tried and true ones. Technophobes believed that investing too early was indulgent and reckless. Executives wore their late technology adoption strategies as badges of corporate honor. Today, emerging technologies are ready for immediate deployment: iPads are ready; Dropbox is ready; Skype is ready; ListenLogic is ready; Foursquare is ready; YouTube is ready.
I predict that these and many other hardware and software technologies will be adopted without clear (or “validated”) requirements models, without the venerable SDLC, and even without rapid prototyping. I predict that technology adoption will turbo-charge into instant deployments.
The figure below summarizes defined and ready technology adoption and the implications of ready technology adoption. It also provides some examples.
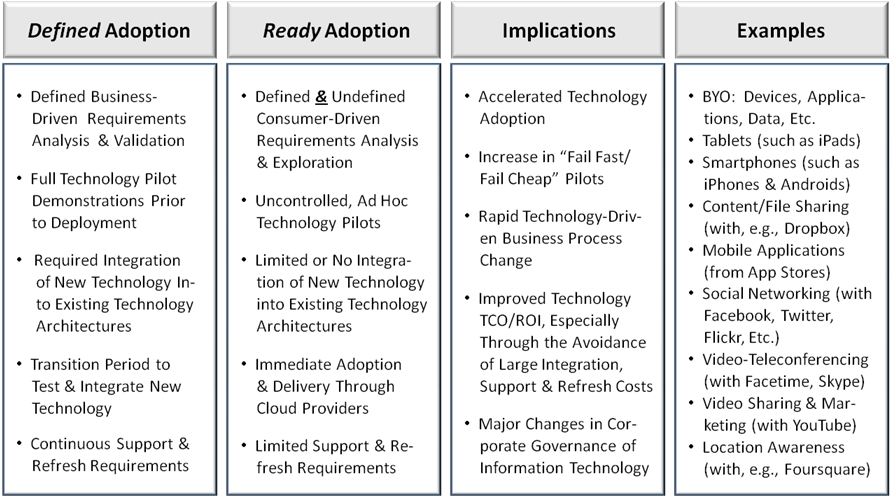
Defined vs. Ready Technology Adoption
I predict that the immediate deployment of ready technology will rapidly accelerate and eventually become a widespread best practice. Immediate technology deployment – of especially consumerized technologies – will forever change the way we think about how technology can impact business models and processes – and disrupt the status quo.



