Having been involved in the IT industry for many years, we find it interesting to observe the constant evolution of technical jargon. Thus we were delighted when we first learned of the acronym "SMAC" -- for "social, mobile, analytics, and cloud" -- as it embodies the essence of what our company has been doing for over a decade. (And we are eternally grateful that the acronym didn't end up being "SCAM.") A relatively new term, SMAC neatly embodies four core concepts that have some natural synergies: "social" equates to engagement, "mobile" equates to personal convenience, "cloud" equates to flexibility and scalability, and "analytics" ties a bow on the package by providing actionable knowledge. So together SMAC represents a bundle of complementary technologies that provide a flexible, scalable, and convenient way for organizations to engage constituent networks and extract actionable insights from that engagement.
So why isn't every organization embracing all aspects of SMAC? Statistics from a 2012 IBM survey paint an interesting picture of SMAC adoption rates.1 Not surprisingly, analytics is currently the most highly adopted of the four SMAC technologies (54% adoption in global organizations). What we today call analytics or Big Data is a direct descendant of older data warehousing, OLAP, and BI technologies, even though today's analytic applications typically involve far larger data sets and much more unstructured data than those earlier instantiations of analytics. Mobile is also rather widely adopted (49% adoption in global organizations), as organizations have quickly embraced the concept of "data anywhere, anytime." The two lagging technologies in the SMAC set are cloud (at 39% adoption) and social (at 34% adoption). Cloud and social are certainly the newest of the four technologies, and they present some interesting challenges for most organizations.
In this article, we're going to focus primarily on the social aspects of SMAC: why it is important and what have we learned about social engagement that can extend and enhance the value of cloud-based, mobile applications with analytics.
HOW SMAC ENABLES VALUE IN HUMAN NETWORKS (SOCIAL SCIENCE)
Mapping different elements of SMAC technologies onto human network behavior allows an enterprise to leverage its networks for an array of different business purposes. As you might expect, a great deal of research has been conducted on online networks in recent years, and this research has accelerated with the rapid rise of online communities such as Facebook, Twitter, LinkedIn, and online dating. In order to get the most value out of a social network, it is imperative to understand who the network members are and to have a deep appreciation of their motivations for participating. Enterprises need to take these factors into account when defining SMAC requirements in order to deploy audience-appropriate solutions.
We have a markedly different perception of "social" than do most organizations. It seems that many view social through either external or internal filters -- external being alternate media channels such as Facebook, Twitter, Pinterest, and the like, which serve as technological extensions of traditional media for marketing, advertising, or customer service; internal being collaboration, content sharing, and content management for employees and other internal stakeholders. We believe that social needs a broader definition: that of enabling networks of people to interact with one another to drive value. Human networks -- networks of customers, networks of partners, networks of employees, networks of developers, and so on -- are the lifeblood of all enterprises. All organizations, both public and private, have them; all organizations leverage them to achieve value. When we use the term "network" in the balance of this article, understand that we mean a human network or network of people. Similarly, we will use the term "network experience" to encompass this broader definition of social.
Consider as examples of our expanded definition two successful enterprises, neither of which is generally considered to be in the business of social: Amazon and Apple. Both are very good at leveraging their networks to enhance value. Amazon leverages its customers for reviews and product recommendations to enhance sales and customer satisfaction, while Apple leverages its network of third-party application developers to create, market, and sell apps for its hardware platforms.
When analyzing these human networks, it is vitally important to understand why people might seek out interaction in online networks and what benefit they achieve by their interaction. Failure to consider the needs of network members is the principal reason why so many online social implementations have failed so spectacularly in recent years. One humorous example, relayed to us by a marketing professional for an organization that shall remain nameless, involved a consumer packaged goods (CPG) company that attempted to create an online community for fans of its brand of toilet paper ... and was shocked when the community never got any traction. As additional examples, we will single out Apple, for its failed Ping social networking attempt, and Amazon, for its (to date) failing Living Social group buying endeavor. The latter proves that even organizations that have had incredible success leveraging some networks can drop the ball with others. To be successful, SMAC solutions must provide benefits not only to the enterprise that will be leveraging the networks, but also to the network members who are asked to participate.
There are several diverse disciplines that speak to the subject of how successful networks form and behave. Disciplines ranging from mathematics to sociology, anthropology, psychology, economics, and communication theory all have tenets that apply at various levels when crafting and managing human network experiences. Some apply early on when developing strategies for leveraging value out of networks; some apply later when defining the implementation requirements for a network experience; and still others apply to online networks once they become operational.
While it is beyond the scope of this paper to go into depth on the practical application of social science to human networks, we would like to briefly consider as an example the theory of diffusion of innovation.2 First described as such in 1962 by Everett M. Rogers, diffusion of innovation theory has gained wide acceptance. Although it was originally an observation about how the adoption rates of new farming practices spread through rural communities, the theory has since been used as a springboard for numerous academic papers and books across a wide variety of disciplines. It occupies center stage in popular management books such as Clayton Christensen's The Innovator's Dilemma 3 and Geoffrey Moore's Crossing the Chasm.4 And even if you don't know it by that name, you are almost certainly familiar with the curve as shown in Figure 1.
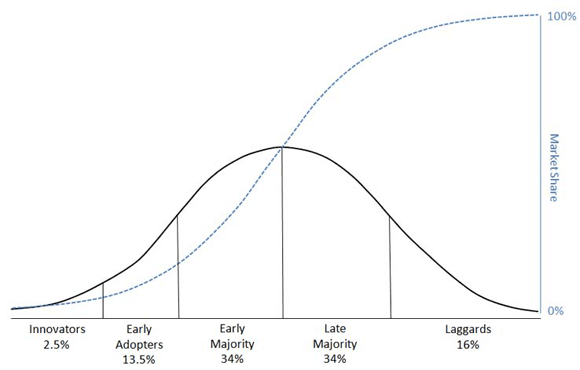
Figure 1 -- Diffusion of innovation.
The theory that new innovations spread in human networks in a predictable fashion -- first to a few innovators, then to early adopters, then to the early majority, then to a late majority, and then finally to laggards -- is a concept that has wide application when considering how to best leverage those networks. It applies not only to networks of rural farmers, but also to networks of customers, networks of employees, networks of suppliers -- indeed, all human networks.
Different aspects of diffusion of innovation theory apply to different levels of network study. For instance, the idea that innovations spread through a network in a predictable fashion and the idea that productivity increases brought about through an innovation will plateau as the adoption rate approaches 100% (the classic "S" curve also shown in Figure 1) are initially quite strategic: they are important considerations when an enterprise is analyzing its high-value networks to see which ones could be utilized to reduce costs or increase revenue by encouraging their members to adopt different types of innovation.
Other elements of the theory are less strategic and more tactical; for example, the concept that different factors influence network members to adopt or reject an innovation, such as its relative advantage, compatibility, complexity, trialability, and observability. These are important considerations when implementing a network strategy and defining requirements for a network experience, such as providing automated ways for members of the network to rate or recommend products or ideas.
Finally, the notion that the adoption rate can reach a "critical mass" -- where further adoption of the innovation is self-sustaining -- is more something to keep in mind when operating a network solution than when conducting either strategic or tactical analysis. This is an important consideration once a network solution becomes operational, and it speaks to the need of the network moderators to give innovative products or ideas an initial push so that adoption can reach the point where it naturally "snowballs."
When applying social science to the development and operation of network solutions, it is useful to note that concepts that apply at the strategic level generally also have aspects that apply downstream when developing a solution's implementation requirements and operational policies and procedures. Similarly, implementation concepts (that don't apply at the strategic level) also apply downstream to operational practices. The reverse, however, is not true. Concepts that apply only to operational practices don't apply to strategy or implementation; concepts that apply only to implementation requirements don't apply to strategy. Interestingly, we find this is why enterprises that attempt to apply social networks as point solutions to tactical problems (such as marketing or customer service) have little success in integrating those solutions into a broader business strategy or overall enterprise architecture (EA).
ENTERPRISE ARCHITECTURE FOR HUMAN NETWORKING AND THE POWER OF RESTFUL APIS
When defining an architecture to support an enterprise's social goals, we must understand that human networks can come in many varieties and span different types of locations. They can consist of members who connect on their own "in public," independent of a product or service company's operational systems (e.g., Facebook, Twitter, LinkedIn, Pinterest, Quora). Other human networks are found on the opposite end of the spectrum, designed by product or service companies (or indeed, even governmental organizations) to drive internal improvements and support a "private" internal audience (e.g., social software-driven employee networks to improve sales or employee retention and performance).
From an EA standpoint, these public systems are inherently more "open," since the public domain human networks (Facebook et al.), were born and raised in the cloud. With regard to the other SMAC technologies, these public systems naturally leverage social technologies and techniques, are inherently mobile because the everywhere availability of the cloud demands it, and leverage analytics to derive lessons that help incrementally improve the network as a whole.
Meanwhile, the private human networks, from an EA perspective, are not required to be open. And from a SMAC viewpoint, they may or may not be cloud-driven or support mobile and analytic functionality as they strive to make internal collaboration more social.
However, with the third type of human network -- a "hybrid network" that bridges the public and private worlds -- it quickly becomes evident that a specific type of enterprise architecture is mandatory to help connect and coordinate the public and private networks. A hybrid network has social aspects that are both entirely public-facing and private-facing but tie a whole process together. For example, a public user may want to comment on an issue that all can see and vote and comment on. The enterprise can then transition these comments into a private network space and consider and process them internally without public visibility. The key top-level requirements for a hybrid network architecture are openness, flexibility, and extensibility. The goal is to have the capability for any SMAC component to be called upon and utilized at any point in a hybrid network where value is exchanged.
These SMAC-supportive architectural requirements are popping up everywhere:
-
An architecture needs to be ready to connect prospects to a company's marketing efforts (e.g., a smartphone-outfitted prospective customer spots an advertisement at a bus stop bearing a QR code that awards a coupon when the prospect "likes" a social media Web page).
-
An architecture must help generate more loyalty and revenue from established customers (e.g., analytics signal that a particular customer is a strong social influencer in the company's customer community and is therefore awarded special shipping rates).
-
An architecture must help fully resolve customer service requests (e.g., it must be able to seamlessly hand off a service activity to a partner through the cloud).
Enabling such scenarios is step one for a SMAC-enabling enterprise architecture.
After achieving this goal comes the revolutionary second step. With the right architecture in place helping to integrate the public and private networks, a company can further enhance the very useful capacity of innovation thanks to the assistance of social technology. The company can move forward even quicker where it could not before to create entirely new services for prospects and customers, develop new products, monetize new processes, or co-create revenue opportunities with partners (e.g., service issues could be handed off from the private network to an appropriate partner for resolution).
The EA technical feature that has emerged to provide the SMAC components such flexibility and data/process openness is composed of REST (or RESTful) APIs. The simplest description of REST APIs is that they expose data and services both internally and externally in a Web-based client-server fashion. Such flexibility helps tackle the numerous possible intersection and integration points inside and outside of a company's architecture in a scalable manner. Therefore, it helps forge valuable synergies by connecting traditional front- and back-office applications with the social, mobile, analytic, and cloud application services.
As companies explore how to leverage REST APIs and the innumerable connection possibilities, they must recognize that this architectural style requires them to learn to publish, manage, operate, and analyze REST APIs as part of their IT department's core capabilities. Such rigor helps companies securely expose their systems and keep track of the SMAC functionalities they either plan to or already integrate with. Furthermore, it allows them to open themselves up to integration with other companies' processes (i.e., those of prospective or current customers, partners, and suppliers). Extracting value from the SMAC capabilities therefore becomes more orderly, manageable, and measurable.
"DE-RISKING" TECHNOLOGICAL INVESTMENT THROUGH A SMAC API INFRASTRUCTURE
Enterprises are only just beginning to embrace the REST API architectural strategy, which helps capture the potential value of human networks over the long term because it is open, flexible, and scalable to a variety of possible network configurations. The value to enterprises lies not only with the initial installation of a solution; over time an enterprise will want to be on a continuous lookout for how to capture additional value as new opportunities arise and networks dictate the need for new experiences. For example, as an enterprise develops a relationship with a customer, it may encounter scenarios where it is best to introduce a partner into the equation to deliver a fitting new product or service. Leveraging a REST API architecture can make it easier to "hook" the partner in to help deliver that added value to the customer relationship. There is also inherent value in the way such architectural flexibility and open architecture "de-risks" the capital decision-making process for software selection, so that the capital risk mirrors the incremental approach decision makers take when going forward with social network strategies.
LEVERAGING "SOCIAL" TO IMPLEMENT SMAC
Enterprises that attempt to utilize social elements to achieve business goals and objectives often make the mistake of implementing packaged software solutions without regard to the software's suitability for solving the problem at hand. This is particularly troublesome in the social arena, where the ultimate success (or failure) of the implementation is entirely dependent on whether the targeted constituents (e.g., employees, customers, partners) adopt and use the solution. Unlike packaged back-office solutions, which can be forcibly imposed on a community, the primary value of social solutions lies in their ability to attract and keep constituents who use the software because they want to, not because they have to.
Organizations can apply several elements of social science as a means of developing conditions that promote the use of SMAC technologies in their organizations. One such element is uses and gratifications theory. Like diffusion of innovation theory discussed earlier, uses and gratifications theory has been built up over several decades. The theory got its start in various studies of television and radio consumption. Researchers were interested in why people watch (or listen to) different types of programs, from soap operas to political programs, and what they got out of them. From those studies, researchers have extracted numerous reasons why different people watch what they watch. Those reasons speak to fundamental needs that all people share and the personal satisfaction they receive from consuming media content. This has critically important implications when conducting a strategic assessment of potential network experiences.
Another strategic theory with practical application to the study of network solutions is social exchange theory, which has roots in sociology, economics, and psychology. The theory states that when viewing a network relationship (say, between a network member and the enterprise, or a network member and another member), people will inherently -- and usually unconsciously -- evaluate the worth of the relationship by comparing its benefits versus its costs. Relationships in which the benefits exceed the costs are likely to be long-lived, while those whose costs outweigh the benefits are not.
A theory with similar practical aspects at the strategic level is equity theory, first described in the 1960s by behavioral psychologist John Stacey Adams.5 Like social exchange theory, equity theory speaks directly to the value propositions mentioned in uses and gratifications theory: not only must there be perceived value in a network relationship (the benefits must outweigh the costs), but members must perceive a somewhat equal value to the relationship. If network members think that the cost of a relationship with an enterprise is too high relative to the benefits they receive (perhaps because they perceive that the enterprise gets much more value out of the exchange than they do), then they will be disinclined to participate.
The benefits of network participation can be wide-ranging, from actual goods and services to more intangible concepts such as member recognition, member security, or member reputation. Likewise, costs can either be tangible or intangible, such as effort required to participate, enthusiasm, skill, or tolerance. Understanding how network members might participate in enterprise networks is a critical success factor when analyzing the strategic worth of a network experience.
Consider the "toilet paper community" we mentioned earlier. This was an attempt by an otherwise successful CPG enterprise to create and leverage a network -- a community of dedicated toilet paper fans -- where none existed before. With a compelling value proposition, an enterprise can indeed create a network from members who have never interacted before, as Apple did with its app developers. But when companies attempt to build communities around brands, consumers are sharp enough to realize that the brand will likely get more value out of the relationship than they will. The exceptions to this are brands that have legions of dedicated fans (e.g., Disney collectors or Harley-Davidson owners). Where there is a preexisting network of enthusiasts, the value proposition is more balanced and more amenable to a network experience. The fans know the brand benefits from their participation, but they still get value from interacting with other fans (which they do in real life even when the company doesn't participate) and the brand itself.
CONCLUSION
Today's SMAC technologies provide a robust, extensible, and low-risk platform architecture for the long-term growth of network solutions and the organizations that offer them. We believe that utilizing what we've learned about engineering successful social solutions can (and should) be turned inward on the SMAC technologies themselves to help define and shape their use. The social aspect of SMAC -- knowledge about how people find value in interacting with one another -- can be successfully leveraged to create vibrant network experiences for members both inside and outside the enterprise, as well as to increase the adoption and success rates of the other elements of SMAC.
ENDNOTES
1 Lo, Jeffrey, Christopher Wyble, and Susanne Hupfer. "Fast Track to the Future: The 2012 IBM Tech Trends Report" (PDF). IBM Center for Applied Insights, 2012 (http://public.dhe.ibm.com/common/ssi/ecm/en/xie12346usen/XIE12346USEN.PDF).
2 Rogers, Everett M. Diffusion of Innovations. 5th edition. Free Press, 2003.
3 Christensen, Clayton M. The Innovator's Dilemma: When New Technologies Cause Great Firms to Fail. Harvard Business School Press, 1997.
4 Moore, Geoffrey A. Crossing the Chasm: Marketing and Selling Technology Products to Mainstream Customers. HarperBusiness, 1991.
5 Adams, J. Stacy. "Inequity in Social Exchange." In Advances in Experimental Social Psychology, Vol. 2, edited by Leonard Berkowitz. Academic Press, 1965.
RECOMMENDED READING
Allee, Verna. The Future of Knowledge: Increasing Prosperity Through Value Networks. Butterworth-Heinemann, 2002.
Barabási, Albert-László. Linked: How Everything Is Connected to Everything Else and What It Means. Plume, 2003.
Benkler, Yochai. The Wealth of Networks: How Social Production Transforms Markets and Freedom. Yale University Press, 2006.
Buchanan, Mark. The Social Atom: Why the Rich Get Richer, Cheaters Get Caught, and Your Neighbor Usually Looks Like You. Bloomsbury USA, 2007.
Christakis, Nicholas A., and James H. Fowler. Connected: The Surprising Power of Our Social Networks and How They Shape Our Lives. Little, Brown and Company, 2009.
ABOUT THE AUTHORS
Dave Higgins is a Senior Consultant with Cutter Consortium's Data Insight & Social BI practice and Principal Network Strategist at INgage Networks. Mr. Higgins has over 30 years' experience in strategic technology consulting, business process reengineering, and software development methodologies at numerous organizations, including Oracle and Sprint. He has worked extensively in a variety of industry verticals in both the public and private sectors. Mr. Higgins is also the author of five books on various aspects of software development and dozens of white papers and trade articles. He can be reached at dhiggins@cutter.com; Twitter: @DaveHiggins1.
Sam Clark is Senior Manager, Market Intelligence & Analyst Relations at INgage Networks. Mr. Clark has spent over 16 years in the enterprise software industry, primarily as an analyst relations expert. His expertise combines over a decade of inhouse and agency experience with four years as an accomplished analyst with the META Group. As an analyst, Mr. Clark provided strategic guidance to Global 2000 enterprises on solution acquisition and implementation following evaluations of leading and emerging vendors and general market trends. He can be reached at sclark@ingagenetworks.com; Twitter: @samuelcclark.