Strategic advice to leverage new technologies
Technology is at the heart of nearly every enterprise, enabling new business models and strategies, and serving as the catalyst to industry convergence. Leveraging the right technology can improve business outcomes, providing intelligence and insights that help you make more informed and accurate decisions. From finding patterns in data through data science, to curating relevant insights with data analytics, to the predictive abilities and innumerable applications of AI, to solving challenging business problems with ML, NLP, and knowledge graphs, technology has brought decision-making to a more intelligent level. Keep pace with the technology trends, opportunities, applications, and real-world use cases that will move your organization closer to its transformation and business goals.
Recently Published
One day, not far into the future, we will regard this era as the time of data breaches. Data breaches will still occur occasionally, but they will be smaller and far less frequent, because those we entrust with data will have learned how to defend it from theft. In that future time, what will we be doing differently to protect our data? One thing we will be doing better is understanding how people think.
Despite the many billions of dollars in expenditures and millions of people being impacted by data breaches around the world, what we have today is a very expensive -- and seemingly unwinnable -- game of cat and mouse being played by hackers with the companies and agencies they target. And let's face it, the cats (whether they be lone individuals or, as is more common today, organized or even state-sponsored groups of professional hackers) are winning handily. Thus it's time for a paradigm shift in data security -- a new approach that will change the game entirely. It's time for the Data Shell Game. In this article, I will explain how this new form of data security works and what implementing this new way of managing and protecting data will mean for IT and for organizations as a whole.
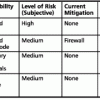
A corporate information security strategy will advance the understanding of risk management. It can bring with it a sense of security to the shareholders and corporate governance. When producing an architectural assessment, there should be a strategy that includes a management team responsible for operating procedures and a technical team to oversee the security efforts. These efforts include training, education, and implementation. Whether big or small, all organizations should have one primary individual who can direct the support, implementation, and deployment of information security.
In a recent Executive Report ("Jumping the Maturity Gap: Making the Transition from Average to Excellent"), we showed how levels of EA maturity should relate to the types of initiative and the outcom
Historically, there have been analogous eras of rampant theft. The items raided were stores of portable wealth -- art, gems, fabrics, spices, and metals.
In June 2013, the actions of Edward Snowden set off a firestorm of revelations about the inner workings of one of the US's most secretive organizations, the National Security Agency (NSA). As the country began debating the spy versus whistleblower status of Mr. Snowden, a second, equally chilling dialogue began: how was one person, a contractor, able to walk so easily out the door of a heavily monitored facility with a treasure trove of secrets? For all organizations, it served as a sharp reminder of how much damage one insider can generate.
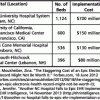
The established platforms developed by other industries have laid the foundation upon which the healthcare industry has begun to propel the IT world to new heights for all industries. This foundation also yields an opportunity for the healthcare industry to create a number of new ventures, many of which may ultimately revolutionize the medical community as Facebook did for social networking.