Failures of Notice and Consent in the IoT Context
One major purpose of the IoT is to collect massive amounts of very discrete data for analysis. Thus, the relevant privacy problems of big data come into play, specifically those of aggregation, scale, and difficulty in understanding what predictive analysis may ultimately affect the individual's interaction with the object.
Is Systems Thinking Finally Hitting Mainstream EA?
For many enterprise architects, the concept of systems thinking is almost synonymous with EA. But knowing about systems thinking and applying that knowledge in our daily work can be very different things. Is that finally starting to change? Is systems thinking finally hitting mainstream EA?
IaaS Contracts: From the Vendor’s Perspective
In this Executive Update, we look at IaaS contracts and the contentious clauses you might expect to see from an IaaS vendor. We focus on a public (unrestricted) example of IaaS because a private one (restricted to your organization) is nearly identical to a typical outsourcing agreement in which you have physical servers hosted at a vendor’s site.
IT Budgeting in 2015: Folks, It's Time to Remodel — Opening Statement
It is clear that our IT homes need a firmer footing, and there is a need for rethinking the fundamental relationships between the IT function, the IT budget, and all the other business entities within organizations. It is also clear that our IT homes need more light and reconfigurable spaces, and there is much we can gain from increasing the transparency and agility of the IT budgeting process.
IT Budgets: A Decade of Data
IT managers must construct the IT budget in such a way as to be obviously defendable as being supportive of the overall direction of the company. The wise IT manager will strive to have support from his or her non-IT colleagues whenever possible. This analysis of the latest CBR survey data will view the results from this perspective.
10 Years of the IT Budget Survey: A Look Back
In the past decade, we have had 658 respondents to survey questions about budget, governance, and IT costs -- that is, the elements that form the foundation of managing IT in the enterprise. With this 10th survey, it is appropriate to consider what we've learned over the past decade and draw some overall conclusions about the IT budget as it relates to the effectiveness of IT in the organization.
IT Budget for 2015: Survey Data
This survey, our 10th annual IT budgeting survey, examined general and specific aspects of IT budgeting in 33 organizations.
Farewell to Cutter Benchmark Review: Thanks for the Insights and Friends
Gabriele Piccoli reflects on the foundational thought behind his approach to editing CBR — a data-grounded collaboration between IT academics and practitioners.
Cutter Benchmark Review: A Personal Farewell
As philosopher Marshall McLuhan famously argued, "The medium is the message." So here are Joe Feller's final set of CBR takeaways, all drawn from the mission of the journal itself:
Cutter’s Farewell to Cutter Benchmark Review
Cutter Benchmark Review inaugurated its two-perspective (academic/practitioner) approach based on survey data from Cutter Consortium with the October 2005 issue. Our initial contributing authors were Cutter Senior Consultants Gabriele Piccoli and Ken Collier, with Gabe performing double-duty as Editor.
Fog Computing, the IoT, and the Open Fog Consortium
Fog computing, also referred to as "Edge computing," is an IoT applications architecture designed to distribute the resources and services of computation, communication, control, and storage closer to the devices and systems at or near the edge of an IoT network or its endpoints (e.g., mobile devices, connected machines, users).
Conway’s Law in a Time of Digital Disruption
With more and more companies embarking on digital transformation efforts of one kind or another, Conway’s law applies simultaneously to three levels of disruption, as identified by Geoffrey Moore: the traditional R&D and IT level, the operating model, and the overall business design. This Executive Update provides guidance on how to apply Conway’s law meaningfully within and across these three disruption levels.
Conway’s Law in a Time of Digital Disruption
With more and more companies embarking on digital transformation efforts of one kind or another, Conway’s law applies simultaneously to three levels of disruption, as identified by Geoffrey Moore: the traditional R&D and IT level, the operating model, and the overall business design. This Executive Update provides guidance on how to apply Conway’s law meaningfully within and across these three disruption levels.
Recognizing and Managing Indulgences
One of the joys of IT is that it gives people the opportunity to learn new concepts and new skills and explore an inner mental world of creativity and show off their new creations.
MobilePay by Danske Bank: A Disruptive Mobile Payment Platform
This Executive Report assesses how a Danish bank managed to become the dominant player in the Danish mobile payment market by pursuing a disruptive “up-market” trajectory. By creating an autonomous business unit with full access to tangible and intangible organizational resources, Danske Bank developed the mobile payment app MobilePay, which has been downloaded by more than 60% of the Danish adult population, while creating a significant branding spillover effect in the bank’s favor.
MobilePay by Danske Bank: A Disruptive Mobile Payment Platform (Executive Summary)
This Executive Summary and its accompanying Executive Report provides a case description of how a Danish bank managed to create a mobile payment application that has now been installed and activated by more than 60% of the adult population in Denmark.
The Unseen Contract: Your Greatest Outsourcing Friend or Foe
In this on-demand webinar, Sara Cullen demonstrates how the items you believe are understood have a direct effect on your outsourcing arrangements' success.
Agile Team Structure and Quality
What I have found over the years of deploying Agile is that organizations forget one of the fundamental reason why they deploy Agile practices: you want your scrum teams to mature as a team and as they mature you should expect that the level of quality in the software delivered will be higher than it used to be.
Organizational Experience with Big Data Technologies for IoT Applications
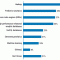
The Internet of Things (IoT) is expected to generate incredible amounts of data from a myriad of connected consumer devices and industrial applications. Achieving business value from this massive data stream will require the use of big data storage and analysis technologies that have the ability to scale to meet the constantly increasing demands placed on organizations. Of course, this brings up the question: just how familiar are organizations with the various big data technologies? A Cutter Consortium survey that asked 80 organizations worldwide about their IoT plans helps offer some insights into this question.
Wearables: Key Takeaways and Adjustments
Takeaways for developers from the companies developing wearables are clear right now. You can find them in the public keynotes at developer conferences from Google and Apple as well as the not-for-disclosure documents widely available to developers for those and other platforms. Detailed APIs are available to developers, and with little effort you can find discussions and test code on public and semi-public resources such as GitHub and YouTube.
Back to the Future with Shared-Screen Experiences
From the fantasy to the real world, there is already an emerging business in large shared-screen experiences. Museums, libraries, hotels, and resorts are among the first locations where organizations can see an immediate return on their investments in creating engaging experiences for visitors in an anonymous fashion. Currently most of these experiences are a small step forward from digital signage, providing people with the opportunity to navigate their own way through the content provided and in some instances share the content to their personal devices.
Beware Slack Elimination
As with most flawed ideas, there is an element of truth in the idea that "leanness" and absence of slack have benefits to companies over the long term. The hierarchical organizational forms that characterize most modern companies were developed in an era when we did not have our current communication capabilities. A large part of the function of traditional hierarchies was to manage information flow. Some of the changes that we have made to organizations have been inevitable adjustments to reflect the fact that we no longer need to devote as much effort to managing information flow because of the nature of new technologies.
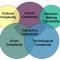
Understanding Complexity
In order to understand the many dimensions of sociotechnical systems, in particular their relevance and importance to the enterprise, we first need an overview of the key issues in the field of systemics, such as complexity.
Six Steps for Leveraging EA Metrics
An effective EA measurement program typically begins by identifying a set of precise and easy-to-use metrics recognized by both business and IT organizations across the enterprise. At a strategic level, EA metrics establish a number of quantifiable parameters that enable practitioners to assess and evaluate the EA program, the IT assets employed, and their relevance to delivering business value for the enterprise. At a tactical level, EA metrics include parameters that impact the EA and its effectiveness across the organization — both directly and indirectly.
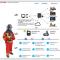
Wearables for Monitoring Workers in Industrial and Other Environments
Industrial, manufacturing, and process industries have used sensors, analytics, and other technologies to monitor and measure how equipment and processes are performing for some time. Now, we are seeing companies seek to apply sensor-enabled devices to support more human-centric monitoring in industrial settings.