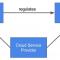
How Do Industries Regulate and Supervise Cloud Service Providers?
Cloud service providers (CSPs) are a new breed of IT service provider, popular around the world and across industries, and so the regulatory spotlight is shining on them more as they acquire larger enterprise customers in regulated industries.
From “Fast-Bleeding” to Market-Leading: A Telecom’s Digital Transformation Journey
In this article, Evangelos Vayias and Ioannis Konstantinidis offer a roadmap for digital transformation and tell us how OTE Group used it to transform itself “from a ‘fast-bleeding,’ bureaucratic telco into a modern, competitive, high-performance service company” through the application of IoT-related technologies.
Using the 5 “I” Terms to Drive Innovation Through Collaboration
This Advisor proposes a five-“I” framework for carrying out a discovery process to uncover opportunities for innovation and continuous improvement in business applications. Application development and support teams can use this framework for running continuous improvements using collaborating innovation and proactively address the evolving needs of business.
The Quest for “Appropriate”: Living with Understanding
Agility, the ability to change direction fast when change is needed, is not something achieved by training your teams in a base set of practices. That might improve efficiency, but it doesn’t, of itself, give the ability to change direction rapidly. If you need agility, you need people who understand; who understand what is appropriate in the new context, and who can switch to doing that very rapidly.
Opportunities and Challenges for IIoT in Oil and Gas
In this article, Claude Baudoin discusses promising IIoT applications in the oil and gas (O&G) sector.
Cyber Security Risks and Challenges for the Industrial Internet of Things
Anjali Kaushik and Kanishk Gaur discuss the most important reason for not adopting IIoT: security. In this article, they warn readers of the possible damage that can result from a lack of adequate security, providing several real-world examples of the harm caused by past cyber attacks.
Enterprise Personal Analytics: Embracing the Potential, Avoiding the Pitfalls
This article examines the way the data collected over the IIoT ecosystem of interconnected humans and machines can be collected, managed, and exploited. The authors focus particularly on a concept they call "enterprise personal analytics" (EPA) and provide a digital transformation roadmap companies can use to adopt EPA, examining the emerging concept through different perspectives (company, worker, and modality) and related concerns (individual information systems architecture, knowledge and intellectual property, motivation and remuneration, information governance, and quality assurance).
Enterprise Personal Analytics: Embracing the Potential, Avoiding the Pitfalls
This article examines the way the data collected over the IIoT ecosystem of interconnected humans and machines can be collected, managed, and exploited. The authors focus particularly on a concept they call "enterprise personal analytics" (EPA) and provide a digital transformation roadmap companies can use to adopt EPA, examining the emerging concept through different perspectives (company, worker, and modality) and related concerns (individual information systems architecture, knowledge and intellectual property, motivation and remuneration, information governance, and quality assurance).
The Why and Hows of IIoT Implementation: The View from a Regulated Industry
Łukasz Paciorkowski starts by asking two critical questions: first, why should we implement IIoT solutions, and second, how should we do so? He convincingly demonstrates why companies should invest in the Industrial Internet by offering a real-world example taken from an ongoing project in the biopharma industry, one of the world’s most restricted fields.
The Industrial Internet: Driving Digital Transformation — Opening Statement
We’re in the very beginning of a revolution dubbed the "Internet of Things," which enables us to propose and develop solutions for interacting with everything connected to the global Internet. Today, it’s the time for everything, rather than everyone, to get connected.
The Industrial Internet: Driving Digital Transformation — Opening Statement
We’re in the very beginning of a revolution dubbed the "Internet of Things," which enables us to propose and develop solutions for interacting with everything connected to the global Internet. Today, it’s the time for everything, rather than everyone, to get connected.
EVM for Agile Projects Part 1: The Planning Process: Developing the Baseline
Discover a light and flexible planning process that is rigorous enough to create performance indices that can control your project. You’ll learn how to plan your Agile project so that you can develop an effective and flexible performance measurement baseline (PMB) that sustains the implementation of EVM controls.
A 360-Degree Perspective for Enabling Innovation
In this Advisor, we provide an overview of our view on the role of the enterprise architect as a catalyst in enabling business transformation, driving innovation, and managing the innovation lifecycle.
Business Architecture Fireside Chat
Cutter Consortium Members Only: Get your business architecture questions answered. Get specific guidance. Share your experiences with other Cutter members.
The Doctor Is In: Blockchain in Healthcare
The healthcare industry is wide open for applying blockchain technology, and we are seeing many projects and commercial efforts underway that center around healthcare data sharing, data protection, regulatory compliance, and process and transaction optimization.
AI and the Consequences of Empowering the Machine
If we believe AI to be a threat to our civilization, it must introduce some substantial risk that is different from the risks that we are already exposed to. Does AI really introduce a new risk? Do machines that incorporate AI pose a threat to human existence? This Executive Update attempts to answer that question.
AI and the Consequences of Empowering the Machine
If we believe AI to be a threat to our civilization, it must introduce some substantial risk that is different from the risks that we are already exposed to. Does AI really introduce a new risk? Do machines that incorporate AI pose a threat to human existence? This Executive Update attempts to answer that question.
Trust Building in Agile Teams
One can argue that Agile methods do not pay off without trust to oil the wheels.
What’s Next for Banks?
The main threat for banks does not come from outside but from within. It is not the fintech companies that are the biggest danger. On the contrary, they offer many new and fresh ways of working that traditional banks would never have thought of. The biggest danger for banks is their difficulty in quickly adapting to this changing landscape, opening up, and determining whom to collaborate with, acquire, ignore, or compete against.
Business Architecture: Lessons from the Trenches
This on-demand webinar explores how a cross-section of businesses are deploying and leveraging business architecture in a variety of ways, across a number of industries.
Business Architecture: A Framework for Innovation, Transformation, Optimization, and More
Faced with a cross-section of seemingly disparate business and technology demands, one would logically ask how a business can concurrently execute a multiheaded set of strategies against operating models that are at best opaque and at worst driving companies out of business. The answer requires breaking down a business to its basic building blocks, which in turn provides a common lens through which to view and align business objectives, initiatives, and related investments.
Business Architecture: A Framework for Innovation, Transformation, Optimization, and More
Faced with a cross-section of seemingly disparate business and technology demands, one would logically ask how a business can concurrently execute a multiheaded set of strategies against operating models that are at best opaque and at worst driving companies out of business. The answer requires breaking down a business to its basic building blocks, which in turn provides a common lens through which to view and align business objectives, initiatives, and related investments.
Thriving Through Technology-Driven Turbulence
Business models are being disrupted across industries by savvy new entrants to markets who are leveraging emerging technologies and the latest digital practices. How is your executive team responding to technology-driven turbulence in your industry and in your marketplace?
The Business and Technical Challenges of Legacy Modernization
One of the greatest growing risks for legacy systems is not the applications themselves, but rather finding people with the skills necessary to continue to develop, maintain, and operate them.
Wrapping Your Head Around Contemporary Innovation
Cutter Senior Consultant Bhuvan Unhelkar goes in depth on why innovators in such a dynamic business space need to be extremely flexible and agile and why understanding the business value of innovations requires imagination and a capacity to map those innovations to existing business opportunities and challenges. He will also reveal how big data, the Internet of Things (IoT) and the Cloud necessitate agility and imagination in order to demonstrate the value of an innovation.