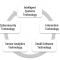
Five Disruptive Technology Clusters
Every year pundits, hardware vendors, software vendors, consultancies, academics, and even government agencies publish their technology “picks” for the following year. One cannot help but notice that just about all of the lists identify the usual suspects; cloud computing, AI, predictive analytics, wearables, and augmented reality are among about five others that make nearly everyone’s “Top 10.”
The approach I take here is a little different. I look at clusters of technologies. I do this because of the overlap among the usual suspects and because of the interrelationships among the technologies. The identification of clusters is also useful because it acknowledges the interdependencies among technologies as well as the integration and interoperability required to optimize whole technology clusters and meaningfully impact business rules, processes, and models. In other words, it’s operationally impossible to acquire, pilot, deploy, and support technologies individually because they’re always dependent upon each other and always connected.
Cognitive Computing 2017: What’s Up and Where to Begin?
As 2017 gets underway, I want to comment on a technology I see as poised for a breakout year: cognitive computing. We are now seeing a considerable amount of innovation in the development and application of cognitive computing across almost every industry. As a result, we recommend that companies start examining how they can benefit from applying cognitive computing in their organizations.
How to Maximize your Investment in Big Data with Lean Thinking
In this on-demand webinar, you'll discover how you can combine big data analytics with a Lean approach to disciplined problem solving, enabled by a Lean management system, to optimize decision making, investment, and performance.
The Essence of an Adaptive Learning Organization
A Lean management system encourages those closest to the customer, those who best understand the work, to own their processes, solve their problems, and make their own improvements and innovations, guided by the strategic priorities of the overall organization.
The Coming Backlash Boom?
The societal effects of AI-driven automation and the like are just beginning to be felt in earnest. The one thing that seems to be certain: over the next decades, companies and countries should be preparing for more political risk and uncertainty, and revamp their enterprise risk management approaches accordingly.
Data-Centric Security and Protection, Part II: Major Threats and Sensitive Data
In Part II of this series, we examine survey findings pertaining to the biggest perceived threats to sensitive data protection efforts as well as issues and concerns for protecting data in cloud platforms and applications.
Effective Execution of Business Strategy with EA
With EA, organization leaders can more readily improve the effectiveness, efficiency, and responsiveness of their enterprise. Effective EA is the key to enabling the enterprise to address orders-of-magnitude increases in complexity and orders-of-magnitude increases in the rate of change.
Approaches to NoSQL Analytics
In the history of NoSQL data, there have been many approaches to solving the problem of performing analytics on it. Not all of these approaches are able to solve all problems in NoSQL analytics — they vary greatly in their expressiveness and flexibility.
Security Architecture and Design
From the design and development of individual applications to enterprise network architecture, our approach is to make security an integral part of the finished product, ensure it is cost-effective and acceptable to your employees, and that it differentiates your products from those of your competition.
Security Architecture and Design
From the design and development of individual applications to enterprise network architecture, our approach is to make security an integral part of the finished product, ensure it is cost-effective and acceptable to your employees, and that it differentiates your products from those of your competition.
Digital Risk and the Need for Cyber Liability Insurance
There is significant potential value for companies of all sizes in reviewing their potential financial vulnerability in the case of a cyberattack, as well as determining whether purchasing (or increasing their) cyber insurance could provide the protection to keep them in business.
Business Architecture Framework for Digitizing Business
Business architecture provides a holistic business perspective of a business ecosystem based on a clearly defined, time-tested framework. Core business architecture domains include capabilities, value streams, information, and organization. The extended view of business architecture includes strategies and policies that drive actions and investments, external and internal stakeholders that receive and participate in value delivery, the products and services a business delivers, the initiatives in which a business invests, and the metrics that enable business performance management.
Data Breach Insurance Trends
According to our research, current adoption of data breach protection insurance is fairly limited. This is somewhat surprising, as I had expected usage to be considerably higher due to the many high-profile data breaches appearing in the news.
Digital Transformation & Innovation Bootcamp
Cutter’s Digital Transformation & Innovation Bootcamp is designed to help executive teams upend the reflex thinking that prevents essential change, take a fresh and creative look at opportunities, and dive deeply into what they need to do to succeed. Cutter Consortium Fellow, Professor Karim Lakhani will guide participants through a 2-day examination of how digital innovation is transforming our business landscape.
Top Intriguing Agile Product & Project Management Articles for 2016
Here are the Agile Product Management & Software Engineering Excellence articles that garnered the most feedback from Cutter Members and clients in 2016. Look for these lists from each of our four practice areas, and rediscover Cutter's most intriguing articles of the year!
Top Intriguing Business Technology & Digital Transformation Strategies Articles for 2016
As has been our tradition for the last several years, we've compiled the five most intriguing articles published by the Business Technology & Digital Transformation Strategies practice this year for today's Advisor. How did we come up with this list? We chose the articles that garnered the most feedback from Cutter Members and clients and those that created controversy among Cutter Senior Consultants and Fellows.
Top Intriguing Data Analytics & Digital Technologies Articles for 2016
As has been our tradition for the last several years, we've compiled the five most intriguing articles published by the Data Analytics & Digital Technologies practice this year for today's Advisor. How did we come up with this list? We chose the articles that garnered the most feedback from Cutter Members and clients and those that created controversy among Cutter Senior Consultants and Fellows.
The Outcome Design Challenge
Outcomes are becoming the moments of truth for customers and employees alike, developing into the points where value is created for the business. Shifting the dial is not about changing capabilities; it’s about changing the way organizations look at what people really need and delivering that as an outcome. This is a competitive differentiator now and will become an essential hygiene factor for competing tomorrow.
Near-Term Opportunities of Cognitive Computing — 3 Examples
In this Advisor, the author explores how cognitive technology can be used “in the small” with benefit today as potential users wait for it to scale for use “in the large.” The author shares three operational scenarios to show how firms could build tools to put cognitive computing techniques to work today.
Engaging Enterprise Architects in Acquisitions
Engaging enterprise architecture (EA) in the acquisition process allows the acquisition team to plan, execute, and evaluate acquisitions within a strategic planning framework that improves acquisition performance without compromising organizational performance.
Fire Alarm in Financial Services: The Regulatory Landscape for Cloud and Outsourcing
In this Executive Update, the first of three related articles, we examine financial services as an example of a highly regulated industry and outline the regulatory landscape that creates points of tension for cloud adoption. We also incorporate perspectives from a differentiated range of stakeholders, including lawyers, technologists, compliance executives, and outsourcing managers.
Fire Alarm in Financial Services: The Regulatory Landscape for Cloud and Outsourcing
In this Executive Update, the first of three related articles, we examine financial services as an example of a highly regulated industry and outline the regulatory landscape that creates points of tension for cloud adoption. We also incorporate perspectives from a differentiated range of stakeholders, including lawyers, technologists, compliance executives, and outsourcing managers.
Adoption Trends for Data Breach Remediation Plans
Data breaches are front and center in the news again. And with the hacking of the US Democratic National Committee's (DNC) servers, allegedly by Russian security services in an effort to influence the outcome of the American presidential election, and Yahoo's latest announcement of a yet another hack involving data associated with more than one billion (!) accounts, it is obvious that no system should ever be considered entirely safe from breaches, regardless of the data security and protection solutions in place.
Teaching New Dogs Old Tricks
I've been in the software development industry for over 30 years, which is more than half my life. I love it, but I’ve had to undergo many changes over the years to stay current and valuable to the industry. According to application developer Bob Martin, it’s possible that the number of professional software developers entering the job market doubles every five years. This means that 50% of software developers working professionally have less than two and a half years’ experience on the job. This is a scary thought for an industry that literally runs the rest of the world. This trend has been building for decades, and it’s getting worse. Because of the high demand for skilled programmers, computer science and software engineering curricula are now among the most popular in higher education, and there’s no sign of this letting up. But the skills students learn in school don’t always match well with what’s needed on the job.
Leveraging Business Capabilities in Digital Transformation
Business capabilities are a foundational business architecture domain. Capabilities play the role of anchoring business perspectives for a wide variety of transformation scenarios, including digital transformation. Coupled with value stream, organization, information, product, strategy, and initiative mapping, capabilities provide a central focal point for exposing multidimensional aspects of a business ecosystem.