CUTTER BUSINESS TECHNOLOGY JOURNAL VOL. 33, NO. 5

Robert A. Martin addresses the complete ecosystem involved in the procurement of products and services. What does it mean to trust that what you buy, and the organizations that sell to you, meet all the conditions required to merit your trust? Martin describes the elements of a system of trust for supply chain security that is currently under development and is based on collecting information from a wide community of procurement departments and standards organizations.
In this article, we examine an effort to develop and validate a process for integrating evidence of organizational, technical, and transactional trustworthiness of supplies, suppliers, and services for decision makers. Leveraging the MITRE community’s decades of experience across a widely diverse set of customers and domains, along with the work of colleagues in industry and academia, the supply chain security system of trust (SoT) has four focused objectives. The first objective is to gather and organize a single structured corpus of the concerns surrounding trust with respect to organizations, products/components, and service offerings. Second is to capture the techniques and mechanisms available to gather evidence as to whether concerns with trust are or are not substantiated (e.g., a bill of materials, whether for software or hardware, can provide a streamlined, repeatable, and scalable method for collecting evidence about salient trustworthiness aspects for supplies you use to build and operate your systems). The third objective is to provide a mechanism for winnowing and tailoring the overall SoT to a custom set of concerns and investigative questions that considers the resources of an organization, the significance of the system or service to its operations, and the consequences that could result from failing to fully vet concerns. Finally, the SoT aims to put in place objective scoring mechanisms that an organization can adapt to its priorities, operational sensitivities, and experience with its type of business and partners.
Along with these elements of SoT, this article describes how various community efforts — like the Industrial Internet Consortium (IIC)1 and its focus on trustworthy Industrial Internet of Things (IIoT) systems in operation and Plattform Industrie 4.02 with its ideas on trustworthy organizations — and other endeavors to define trustworthy systems can be integrated.
Context for the SoT
The supply chain security SoT is a MITRE community initiative aimed at defining, aligning, and addressing the specific concerns and risks that stand in the way of organizations trusting suppliers, supplies, and services. The SoT effort includes an examination of the issues that can undermine trust in a supplier and/or in the supplies and services it provides. This examination encompasses the multiple contributors to the development and provisioning of systems and services, as well as the suppliers’ offerings of services to maintain systems and proffer upgrades/updates.
The topic of trust and trustworthiness is one confronting many communities around the world. At the same time, these communities often reflect distinct perspectives and different purposes. The IIC, for example, has been exploring how to define a trustworthy IIoT system and how to demonstrate or establish that it is trustworthy.3 Simultaneously, Germany’s Plattform Industrie 4.04 use of the term “trustworthy” suggests what it means to work with trustworthy partners, and this group collaborates to align with the IIC’s work on the trustworthiness of systems.
When we explore what many define as supply chain issues, most organizations tend to focus on whether delivered goods and all associated components and raw materials will be available where and when they are needed — the classic “logistics” approach to supply chain. When industry and government use the terms “trust” and “trustworthiness,” however, they focus on risk management, most often in terms of financial and regulatory perspectives.
Parties to transactions do not usually consider yet another source of risk: how to decide to trust those different parts. Moreover, they often do not have a complete understanding of the different areas of concern and risks that could disrupt a supply chain, or, importantly, the risks that could undermine trust in a system or a supplier. A frequent result is that, when two organizations “talk to each other,” they are instead talking past each other because of differences in each party’s definition of the word “trust” and accompanying concept of transactional trustworthiness.
As illustrated in Figure 1, the various entities involved in transactions exhibit different intentions, along with individual unique understandings of the meaning of trustworthiness. Real-world examples include parties concerned with creating or using trustworthy commercial-off-the-shelf (COTS) systems that incorporate information and communications technology (ICT), or those interested in having trustworthy high-value items like medical devices with embedded ICT capabilities, or those concerned with having trustworthy surveillance cameras across a large manufacturing complex. These parties undoubtedly often have different intentions, along with individual, unique understandings of the meaning of trustworthiness.
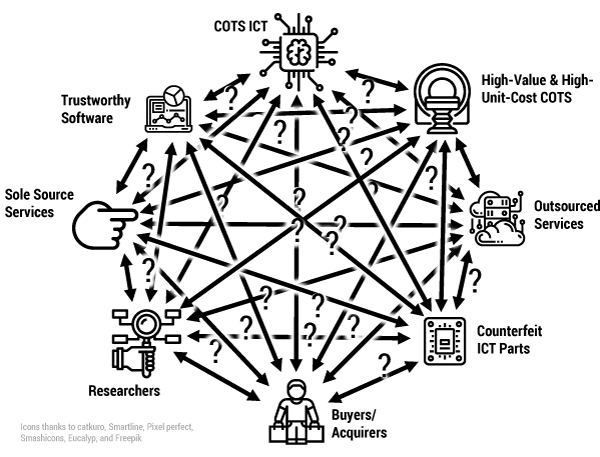
While each of the above roles and types of concerns uses the terms “trust” and “trustworthiness,” generally the various entities presume different concepts, scope, and level of veracity underlying those terms. This causes immense confusion and misunderstandings that negatively impact organizational transactions and trust and trust relationships (primarily external, and potentially internally). The SoT harmonizes the vocabulary of trust and trustworthiness while supporting the subtexts and nuances that delineate varied areas of concern and various roles among suppliers and those using their products and services. Without this harmonization by the SoT, each of these unique participants with their unique experiences and perspectives will continue to talk past each other due to their use of differing concepts or scope of issues when they talk about trust and trustworthiness.
Supply Chain Security’s Challenging Evolution
From a supply chain security perspective, the least understood risk to most organizations comes from needing to almost be a programmer to use everything from a vehicle, to an elevator, or to today’s medical devices, never mind trying to manage a “smart” power grid. Software- and network-enabled ICT has become a key enabler for a large portion of people’s homes and businesses, with new and enduring supply chain challenges.
While organizations have always had suppliers, the introduction of the supply chain as a unique source of economic harm and national security risk came in World War I, when “anti-tamper” became both a practice espoused for protecting the goods and services of the munitions industries and combat material and a focused law enforcement effort aimed at defeating sabotage and counterfeiting arose. This was followed by World War II–era efforts to protect nuclear and other defense industries’ production and critical infrastructure products throughout their full lifecycles. Subsequently, we saw the introduction of just-in-time (JIT) manufacturing, where flexibility, predictability, and multi-sourcing considerations came to bear. This created a much-expanded universe of supply chain partners and all manner of supplier qualification issues, including the transitive financial stability risks of those upstream of an organization and the need to trust a supplier to deliver the right quantities on time. If a supplier’s supplier is disrupted, the finely tuned JIT supply line might not just falter, but crumble.
In the 2000s, many US federal government practices of supply chain logistics management from the Cold War era were extended into the broader commercial IT marketplace, as those technologies and the efficiencies they brought to business and government started to become key enablers of the information economy. As if this were not enough of a challenge, the computerization of everything gave rise to pervasive cyber threats. For many suppliers serving the US Department of Defense (DoD) with commercial goods, the concept of a “cleared industry partner” became part of their way of life. In parallel, the globalization of ICT manufacturing and markets, coupled with security concerns such as the growth in export licensing of sensitive US technologies, extended the definition of, and areas of concern with, the supply chain. Consequently, visibility and control of highly complex microelectronic component supply chains and their global network of specialized software developers has become a difficult, perhaps impossible, technical management problem.
Naturally, the resulting potential for disruption and harm from the supply chain has become a key concern at the personal, organizational, and societal levels. Such supply chain–rooted risks require specific attention and different perspectives about an organization’s practices across the many business functions of both commercial enterprises and government. Figure 2 illustrates these disparate aspects of supply chain security and the variety of organizational elements that need to work together effectively to address them.
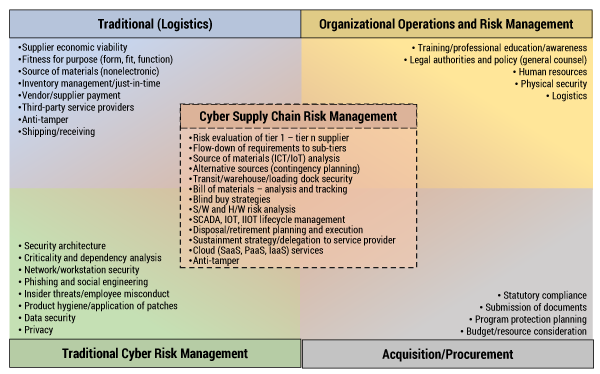
Today’s organizations must coordinate and foster cooperation across their various business functions to enumerate, measure, and manage their supply chain risks. In particular, techniques addressing the supply chain risks to software and software-enabled ICT components do not easily fall within the traditional logistics supply chain practices applied for the protection of physical goods and services in transit, although they share some commonality.
Supply chain security is the superset of these different elements. Depending on the nature of a product, service, or provider, players from one or more of these elements may take the lead in addressing the current set of concerns and risks. However, an organization should be ready to shift focus to other aspects of supply chain security as circumstances change (e.g., the item is now installed and needs servicing), such as shifting focus from acquisition to operations risk management and cybersecurity. The relationship between supplier and customer also inevitably changes over the lifecycle of an item and its role in an organization. An organization may even fill various roles simultaneously, as an acquirer for one item, an integrator for another, and the supplier for a third.
Usually, the discussion of a supply chain will start with discussing immediate suppliers (often referred to as tier 1 suppliers), but when addressing many of the concerns with suppliers, we need to consider the suppliers’ suppliers as well (referred to as tier 2), and so forth, all the way to tier n. The realm of supply chain concerns includes both intentional and unintentional acts. So not only do we need to consider someone inserting tainted or counterfeit items, but also someone accidentally introducing poor-quality items due to errors or poor-quality checks of hardware, software, and/or services. A system of trust, therefore, needs to have a pervasive, holistic approach to everything that can be of concern; only then can the SoT be truly effective in supporting the management of relevant items of concern.
Guiding Goals for Building the SoT
As these past efforts have grown, evolved, and bumped into each other, the need for consistency in terminology and harmony in approach have become increasingly important. Today, enterprises of all sizes need to interact and work with a diverse community. Given the diversity of approaches used to manage and consider supply chain issues, the current likelihood that any two organizations will have the same considerations and sets of concerns is limited. Consequently, there will be wasted time and energy as they struggle to understand each other’s expectations and abilities to provide and utilize trustworthy products and services that can be trusted.
The SoT’s four objectives are as follows:
-
Gather and organize a single structured corpus of the concerns surrounding trust with respect to organizations, products/components, and service offerings.
-
Capture the techniques and mechanisms available to gather objective evidence as to whether the concerns with trust are or are not substantiated.
-
Provide a mechanism for winnowing and tailoring the overall SoT to a custom set of concerns and investigative questions that considers the resources of an organization, the significance of the system or service to its operations, and the consequences that could result from failing to fully vet concerns.
-
Put in place objective scoring mechanisms that an organization can adapt to its priorities, operational sensitivities, and experience with its type of business and partners.
In fulfilling the first objective, one goal of the MITRE SoT is bringing alignment and harmony to the array of concerns organizations — particularly large acquirers of ICT in government and in a country’s critical infrastructures — may have with the supplies they receive, the services they utilize, and the suppliers they rely on, so that the entire community has a common holistic set of concerns to consider. Additionally, the SoT seeks to inform users of the present trust posture of an entity and its products by means of a static assessment, using an objective set of metrics. The SoT is also constructed to provide a dynamic view supporting a forward-looking prognosis of the trust posture over time. This temporal aspect will make a SoT assessment more useful, but also more challenging to validate.
The second and third objectives focus on the process we are using to design and implement tooling to support the operational use of the SoT and assessments against it. The next section discusses the data model created to support these objectives and the piloting being established to validate that the SoT can meet these objectives when applied to real situations.
To fulfill the fourth objective, the SoT needs to:
-
Be the basis of a tailorable assessment that focuses on the context of a specific organization and the supply and service items it is examining
-
Be able to adjust the importance of the consequences of the risks to focus on the context of the operational capability into which the supplies/services are being integrated
-
Be widely applicable to different sizes and types of organizations and domains of businesses and operations
-
Be widely adoptable by regulated and unregulated entities, as well as governmental organizations
By meeting these objectives, the SoT will be well positioned to become the generally accepted principle for supply chain security, similar to the generally accepted accounting principles (GAAP) used in all businesses in the US or the globally equivalent international financial reporting standards (IFRS).
The SoT Creation Approach
The SoT is an amalgamation of MITRE’s decades of experience in supporting its customers’ efforts to address supply chain issues, along with its engagement in various national and international standards efforts on the topic and all the associated published work from MITRE, the standards developing organizations, and others working in various aspects of supply chain security. The SoT permits us to transform that knowledge base into a coherent whole that serves as a taxonomy and implementation model. Acknowledging the vast collection of past and current supply chain security work from across the world and the variety of questions each effort has established, the MITRE effort is both building from the ground up (using individual questions) and from the top down (using supply chain risk taxonomies).
Moreover, the SoT effort is arranging unilateral non-disclosure agreements (NDAs) with a variety of industry organizations. These unilateral NDAs are almost identical to the ones MITRE previously used to create the Common Weakness Enumeration (CWE) body of knowledge.5 Like other community efforts MITRE has pursued, feedback and engagement with experts and practitioners will be critical in creating something that promotes integration, eases the burden of working with others, and streamlines communications and understanding when multiple parties discuss a topic or share information.
In addition to the community published materials, MITRE’s past internal work, and the knowledge shared through the unilateral NDAs, the SoT will also integrate legal-focused content to allow for the SoT to identify areas of concern that an organization might be obligated (or precluded) from investigating.
By collecting the various sets of measures and questions currently in use across the various aspects of the supply chain security community depicted in Figure 2, MITRE is establishing a wide-ranging set of risk-determination questions for input into the SoT. However, rather than just have these as open-ended questions or questions requiring subject matter experts (SMEs) to interpret when used, the SoT will refine them into a series of yes/no questions that embed SME experience into the questions themselves so that less experienced practitioners can use them to identify where and at what level one might trust a supplier, its supplies, or its service offerings.
To illustrate this, consider the different modes of taking a measurement of human blood pressure. If we ask only for the systolic and diastolic measurement, there is an implicit requirement for someone with appropriate training and understanding to interpret the measurements (the evidence) into a finding of “normal,” “elevated,” “hypertension stage 1,” “hypertension stage 2,” or “hypertensive crisis.” If, however, we ask about these as separate range-based questions that are yes/no–based, the medical expertise is embedded into the questions themselves, for example:
-
Is the systolic number less than 120 and the diastolic less than 80?
-
Is the systolic number higher than 180 and/or the diastolic higher than 120?
To the extent possible, the supply chain security SoT will follow this paradigm of embedding informed risk expertise into the questions so that the SoT produces objective metrics that can easily be used by those who are not supply chain risk SMEs.
Rather than collect these items into a spreadsheet, word processing document, or some other unstructured form, the SoT will use a knowledge base along with an application tool to support viewing, organizing, and tailoring the content or subset of the content within the SoT. Further, this application tool will support evaluating a supplier, supplies, and services against the tailored SoT subset, as well as support adjusting the contributing weights of specific SoT questions and areas of concern. The SoT tools will focus on assessing the supply chain security concerns captured in the SoT taxonomy against specific supply items, service offerings, and companies. The SoT tools should not be confused with general risk management tools in common use at many organizations.
The SoT Knowledge and Evaluation Model
As part of bringing together the vast past work in supply chain–related risks and concerns and to support reviews, tailoring, and evaluation, the MITRE SoT effort has a knowledge and evaluation model at its core. This model leverages the work within the standards community6 for representing measures7 where high-level categories of the taxonomy are broken into lower-level collections of subcategories as appropriate and then into factors and measures for those factors, as shown in Figure 3.
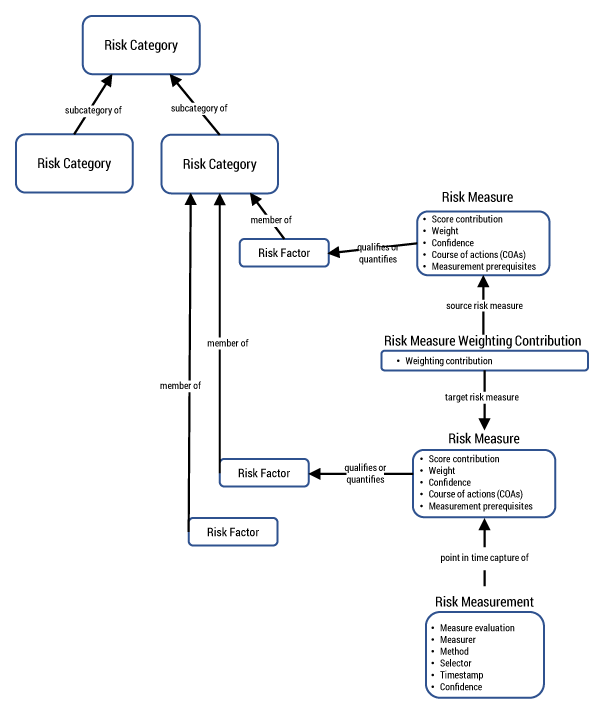
Through the use of this model, the SoT will bring alignment and consistency for the concerns it captures and the risk questions it incorporates, as well as support the contextual relationships between some aspects of the risk measures themselves and how one risk measure may potentially contribute to another. Specific scoring mechanisms, weights, confidence indicators, and measurement prerequisites should provide for wide adoption in diverse industries and organizations.
The SoT Draft Structure
The initial version of SoT tooling mechanics is still in final development at the time of this writing; however, essential aspects of the analytical tool have been developed. The top-down portions of the SoT taxonomy are currently represented by elements defined as “concerns about supply chain security,” which are then decomposed into: (1) concerns about suppliers, (2) concerns about supplies, and (3) concerns about services.
Figure 4 illustrates the first few levels of the draft SoT taxonomy as a mind map. This draft taxonomy is a reasonable generic starting point but will continue to evolve as other organizations contribute to it.
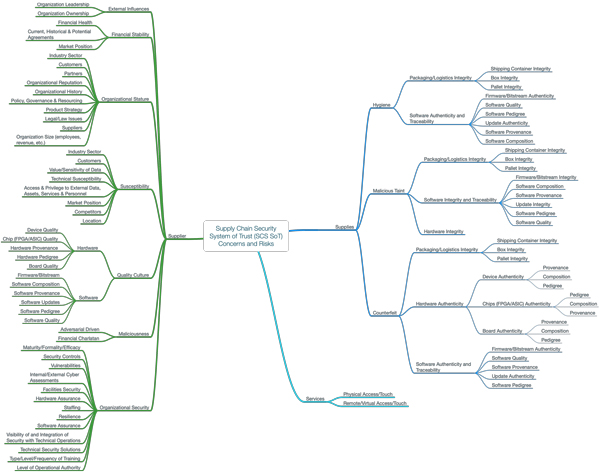
The Concept for Applying the SoT
Applying the SoT as an evaluation framework and tool will challenge organizations on both sides of any supply chain transaction to confront deeply embedded characteristics of their corporate behavior and culture. Customers/acquirers will use a variety of information sources to provide themselves with the types and depth of data they need to enumerate risks and build trust. That data may force customers/acquirers to adjust their internal risk management strategies to compensate for whatever they discover is blocking their ability to trust. Product/service providers should pay attention to what public and private information is being collected and shared about themselves, their products and activities, and their own suppliers. Providing evidence that demonstrates trust-building behavior will increase the attractiveness of their company as a supplier to those seeking to acquire items using the SoT.
For example, every organization faces a challenge in how to balance leadership goals, employee morale, and consistency of behavior across the organization with the financial incentives the organization offers to achieve those behaviors, goals, and the desired morale level. The outward perception of these characteristics shapes the ability of the organization to radiate trustworthiness to external stakeholders. Many consumers care only about the features and costs of an organization’s products and services. But supply chain intermediaries, including those that represent the needs of consumers, such as governmental and industry purchasers, should look beyond these basic, consumer considerations to assess the trustworthiness of a potential supplier. Even those suppliers with whom the acquirer has an existing relationship should be periodically assessed for their continued trustworthiness as an organization, to include their supply chain.
Beyond the obvious factors of features and cost, what remain are the characteristics addressed when applying the SoT. An assessment of trust — and of its counterpart, risk — should be an essential step in the acquisition process. Applying the SoT will assure that all parties to a transaction use a consistent assessment process and vocabulary.
Many of the factors in building trust and managing risk are not quantifiable. Applying the SoT will require the acquirer to compare its own organizational values to the demonstrated or acquired data about its potential supplier’s values. Customers seek evidence to trust or not trust organizations and to quantify risks to their own organizations. Applying the SoT, evaluating the resultant set of questions, and utilizing their weighted scoring will provide the foundation of a defensible rationale for an appropriate level of trust by assembling enough data points to distinguish those suppliers most worthy of trust.
Validating the SoT
To fulfill its envisioned role, the SoT needs a robust set of verification and validation (V&V) processes to assure users of its value in driving adoption of trust-building strategies for all ICT supply chain participants. During development, these processes will incrementally and methodically ensure that the indicators of both risk and trust make sense. Using internal, data-driven examination, benchmarking, and testing, as well as external application and critique, the V&V process will ensure the SoT is usable in its initial release and over time.
The Way Ahead
In addition to continuing to build the SoT, socialize the concepts it entails, and gather ideas for additional questions that explore how to make concrete the concerns organizations have with their suppliers, supplies, and services, the SoT effort will continue creating an assessment tool. This tool will allow an organization to tailor the SoT to just those select areas of concerns an organization feels are the most useful for its decision making. Eventually, it will support tuning of the weights and combinatorial mechanisms used to combine the individual answers into an overall trustworthiness finding. Finally, it will enable the exploration of mechanisms used for answering the questions, whether manually, through data analysis tools, or with both quantitative and repeatable qualitative methods.
At the same time that we explore these analytic approaches and methods, we will be identifying which of the questions can be answered with public or private information sources and exploring how to document these possible sources of evidence about those aspects of the SoT.
Many communities exist for the topics being amalgamated under the SoT. Their respective past, current, and future work will need to be explored and integrated, where appropriate, so that the SoT and those efforts can coexist, proffer synergy, and ensure their respective work, foci, and best practices are clearly understood.
Finally, there will be an immediate and evolving need to explain and train individuals and organizations on the use and utility of the SoT. Additionally, many of those currently working in the areas touched by the SoT work will, we hope, evolve their efforts to align with the integrated SoT vocabulary and concepts as we collectively solve the ICT trust and trustworthiness challenge, with a shared taxonomy and methodology and the SoT tooling (more ICT).
A Piloting Plan for the SoT
In view of both the novelty of the SoT concept as an element of supply chain security abilities and the anticipated broad scope of interest from organizations across industry and government, together with the broad applicability of the SoT’s concepts, taxonomy, evaluation methodology, and tool set, we have decided to embed the practices of frequent testing, expert evaluations, and interim exercises (both mini/tabletop exercises and full formal simulations) to test assumptions about the structure, functioning, and applicability of the SoT’s elements to the full technology lifecycle.
The SoT must be designed as a living system that evolves with changing needs. In addition to these continuing practices of testing and evaluation throughout the creation and maturation process of the SoT, there will also be two or three pilot implementations of multiple weeks to provide further evidence of functionality and to support further editing and restructuring, gap analysis, and overall refinement.
The first assessment pilot will focus on an acquisition of a large operational technology–focused system that is about to conclude. The planned pilot will analyze the procurement artifacts and compare the scope and coverage of issues considered by the just-concluded acquisition with what the SoT considers. The aim is to identify possible after actions for application to the winning solution, as well as to provide ideas for revisions to subsequent acquisition activities.
The second assessment pilot will involve a set of enhancements where a planned set of COTS and open source items are being integrated for use across a large community. The pilot will assess a widely used platform capability from the perspective of supply chain security concerns about the supplier and the software of the capability itself.
The third assessment pilot will address the gamut of cybersecurity and other ICT supply chain security challenges that many organizations face when looking to purchase COTS items. The pilot will assess a widely used commercial capability from the perspective of supply chain security concerns about the supplier, the software of the capability itself, and offering the service to the world.
Finally, a regular cycle of exercises and user evaluations is intended to be a signature element of the SoT’s “maturity model” during its future life. Ongoing exploration of applying the SoT to other acquisitions, suppliers, and products/services will occur in other transactional environments, including various intergovernmental and critical infrastructures transactions, as already described. The flexibility and adaptability of the SoT are expected to become key elements favoring SoT incorporation and adoption in these diverse transactional settings.
Acknowledgments
The summary work contained in this article is based on discussions with a number of individuals at MITRE and throughout the industry. The author offers a special thanks for the contributions of the MITRE SoT team, which provided valuable input to this article.
References
1Industrial Internet Consortium (IIC), 2020.
2Plattform Industrie 4.0, 2020.
3IIC (see 1).
4Plattform Industrie 4.0 (see 2).
5“Common Weakness Enumeration, Version 4.0.” MITRE, 2020.
6McGarry, John, et al. Practical Software Measurement: Objective Information for Decision Makers. Addison-Wesley Professional, 2001.
7“ISO/IEC/IEEE 15939:2017, Systems and Software Engineering — Measurement Process.” ISO/IEC/IEEE, 2017.
©2020 The MITRE Corporation.



