Strategic advice to leverage new technologies
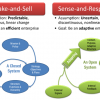
Technology is at the heart of nearly every enterprise, enabling new business models and strategies, and serving as the catalyst to industry convergence. Leveraging the right technology can improve business outcomes, providing intelligence and insights that help you make more informed and accurate decisions. From finding patterns in data through data science, to curating relevant insights with data analytics, to the predictive abilities and innumerable applications of AI, to solving challenging business problems with ML, NLP, and knowledge graphs, technology has brought decision-making to a more intelligent level. Keep pace with the technology trends, opportunities, applications, and real-world use cases that will move your organization closer to its transformation and business goals.
Recently Published
Inspired Reading for Enterprise Architects
In this Executive Update, I recommend some books that I have found most inspiring in my life as an enterprise architect. It is a very personal list. It comprises the books that have had the most profound influence on my enterprise architecture (EA) ideas and practice.
Establishing the organizational foundation for service leadership where everyone is the customer should be a high priority. In my leadership experience and interactions with service leaders around the world, I have learned that being an effective leader comes down to one thing: care and they will care.
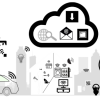
In this article, the author focuses on the security and privacy challenges inherent in IoT implementations and proposes solutions to help build a feeling of trust between all parties. In doing so, he answers such questions as “How do we assess the security risks in IoT?” and “How can the distinct interests of the sources and the collectors of personal data be expressed in a way that satisfies both parties and increases privacy and access control?”
IoT devices have many advantages, but also vulnerabilities and risks. Many smart household appliances are poorly protected (if at all) against cyberattacks. This means that any script kiddie with minimal hacking skills can use them to break into the home network. If, a few years ago, someone had said that TVs and refrigerators could be compromised by hackers to send malicious emails, you would have laughed at them. But such an attack indeed happened on January 2014 — the first known cyberattack to use smart household appliances.
Historically, social engineering exploitations in computer systems were limited to traditional Internet communications such as email and website platforms. However, in the Internet of Things (IoT), the threat landscape includes vehicles, industrial control systems, and even smart home appliances. Add to this mix naive users and default passwords that are extremely weak and easily guessed, and the threat becomes greater. As a result, the effects of a deception-based attack will now no longer be limited to cyberspace (e.g., stealing information, compromising a system, crashing a Web service), but can also result in physical impacts.
In this article, Claude Baudoin provide examples of the risks and a discussion of the methods available for mutual identification, authorization, and access control between IoT devices and control systems, as well as protection of data and commands as they cross the network. He also discusses how policies and risk management, not just the technology, need to be components of the overall approach.
Chatbots and intelligent virtual assistants are receiving a lot of interest from companies across various industries wanting to add capabilities to mobile apps and popular messaging systems that will enable customers to conduct common interactions in a conversational manner via speech and natural language-text-powered interfaces. This Advisor looks at the trends and developments in this area.